Someone is "securing" something, and someone else is "breaking" something. Attackers just need to employ the 30–35 approaches listed in order to get access to Active Directory, but security personnel must employ all available technological tools in order to defend the environment from attackers. When we say, "all technical means," we mean looking at Active Directory from the standpoints of attackers and AD upkeep.
Learn About
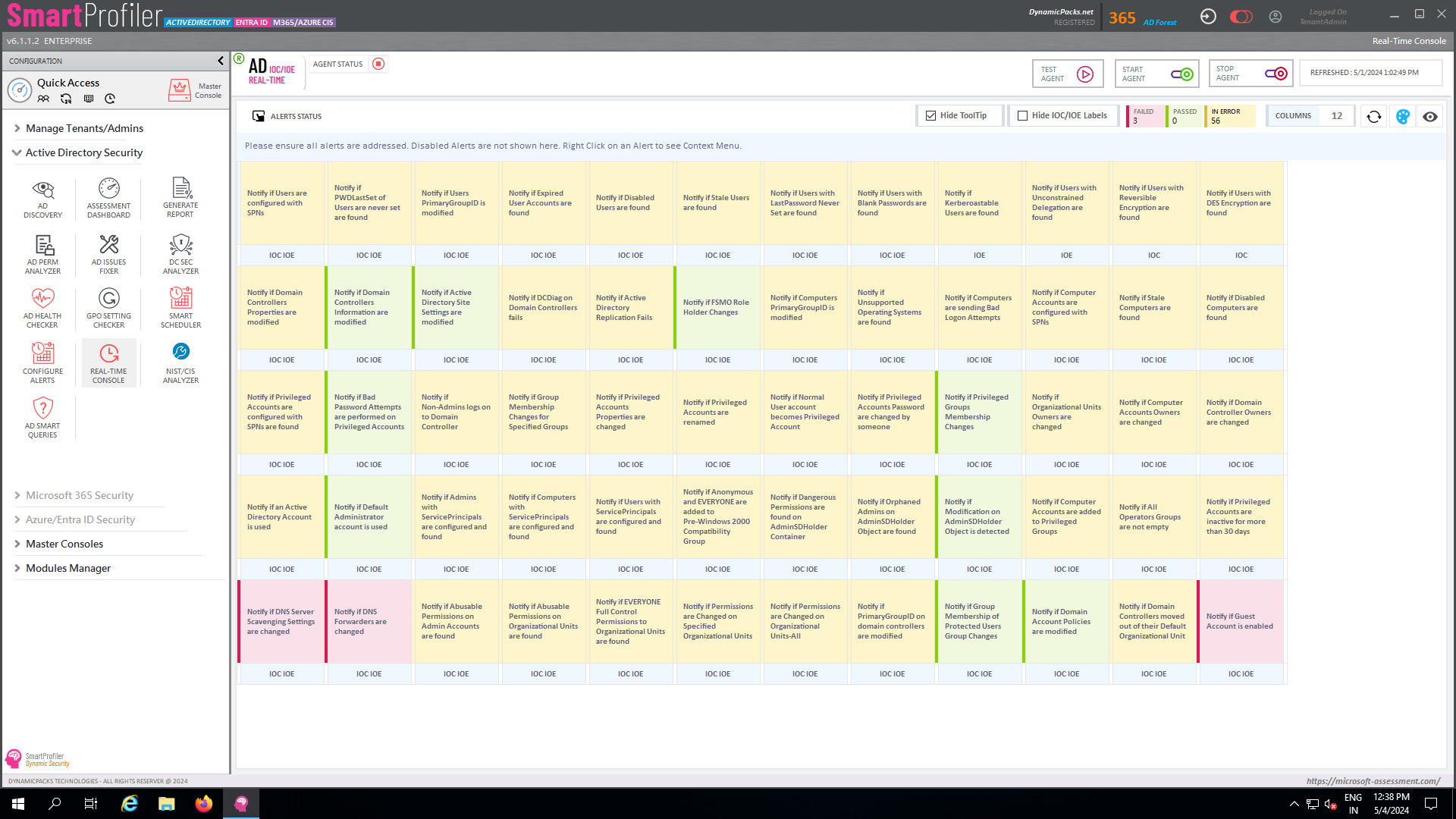
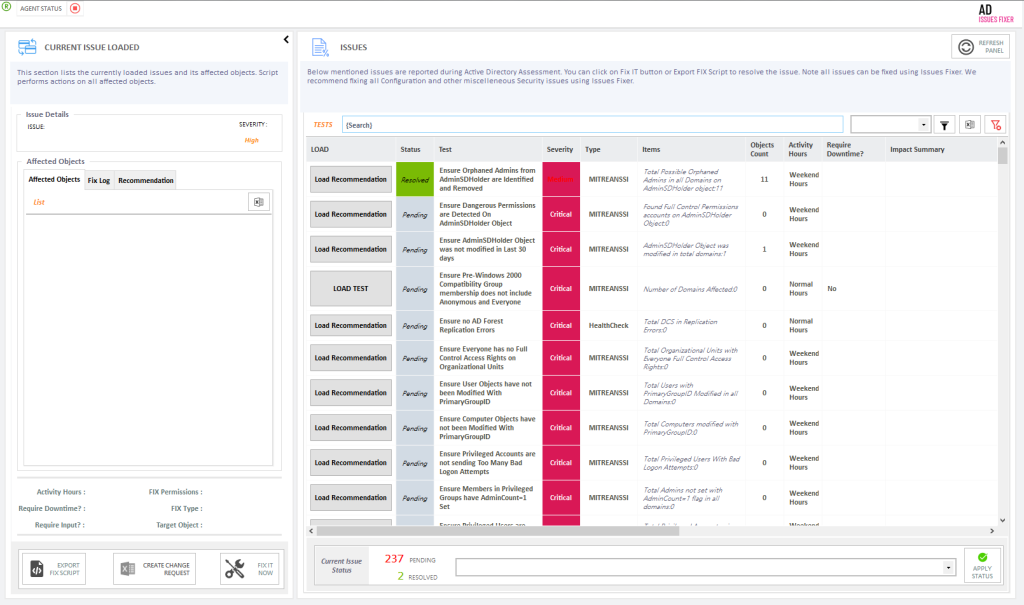
The fact that an attacker would have investigated every method of breaking into Active Directory despite the fact that not all Active Directory administrators are aware of them makes it necessary to conduct a "complete" security assessment for Active Directory.
Advanced assessment parameters for an Active Directory security assessment includes:
1. Investigating further based on the assessment findings.
2. Checking all GPO Settings recommended by CIS and NIST for domain Controllers.
3. Ensure the necessary structure is defined for GPO and all recommended GPO settings are implemented.
4. Administration structure is defined for Organizational Units and to manage AD & domain joined devices.
5. Operational procedures are in place.
Learn About
While the Assessment Categories assist in selecting the appropriate Active Directory Assessment tool, the Methodology provides an overall perspective for both the IT Management Team and IT Operations Team. The SmartProfiler adopts a methodology that caters to the needs of both teams. The methodology should include the following:
- Assessing the current environment level: The tool should evaluate the existing Active Directory environment and discover all domains.
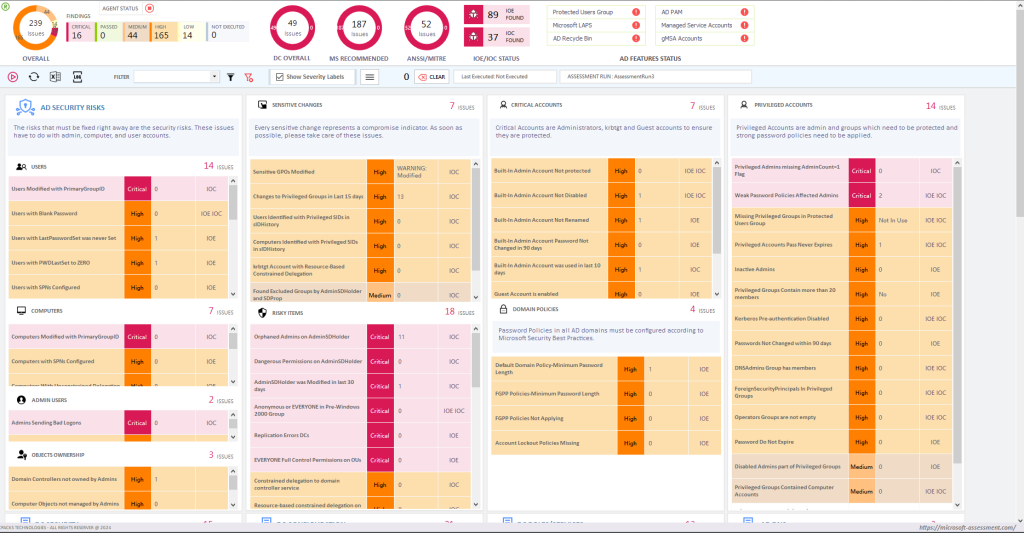
- Identifying Critical and High Risks: The Management Team needs to be aware of any critical and high-risk factors in the environment that might potentially disrupt business applications.
- Prioritizing Items in an Action Plan: The Management Team must determine if there are critical and high-risk items that require immediate attention, considering the cost associated with addressing them. Since budget limitations may exist, prioritization becomes necessary.
- Vendor Recommendation Link: It is the most important aspect of an Active Directory engagement. You would like to know what Microsoft and other vendors say about the issues reported by the tool and does the tool provides a link to check?
- Mitigation Pan: A mitigation plan can be drafted based on your engagement experience which includes preventing issues/failures in the near future.
Learn About
How many times have you assessed an Active Directory environment for a client and seen users with unrestricted delegation, trusted for delegation, DES-Encryption enabled, and pre-authentication Kerberos disabled? So, a small business running Active Directory with two to five domain controllers should to be able to manage their AD infrastructure easily without the need for utilising the aforementioned settings for users. Unrestricted delegation, DES-Encryption for users, and deactivating pre-authentication Kerberos for users are not actually required. You would still need to complete the tests associated to users as part of the standard checklist included in the Assessment tool to make sure everything is in order for user objects.
Learn About