In this article we define a how to perform Complete Active Directory Security Assessment for an Active Directory system, and do you actually have the expertise reviewing Active Directory beyond using the default criteria that come with an Active Directory assessment tool?
Someone is “securing” something, and someone else is “breaking” something. Attackers just need to employ the 18–19 approaches listed in order to get access to Active Directory, but security personnel must employ all available technological tools in order to defend the environment from attackers. When I say, “all technical means,” I mean looking at Active Directory from the standpoints of attackers and AD upkeep. A complete Active Directory Security Assessment involves checking all aspects of Active Directory environment.
After working with clients from all around the world, my path to Active Directory has been interesting. Since there were no ransomware attacks when we were working with Windows NT, Windows 2000 AD, and even Windows 2008, we never paid any attention to protecting Active Directory. Active Directory is now more open to attack. It’s because your Active Directory infrastructure is completely open to intruders once an attacker has obtained access to your network. Moving to Azure cloud would thus protect you from 60% of attacks, but the sad fact is that not many organisations can totally switch to Active Directory since the majority of in-house design applications will be severely impacted by performance issues as a result.
There are several reasons as to why I think that Active Directory is more vulnerable to attackers:
The fact that an attacker would have investigated every method of breaking into Active Directory despite the fact that not all Active Directory administrators are aware of them makes it necessary to conduct a “complete” security assessment for Active Directory. When I say, “complete AD assessment,” I mean looking for misconfiguration that an Active Directory administrator would overlook and never examine, as well as checking for configuration and issues that you can investigate depending on your level of Active Directory expertise. Let’s clarify the difference between a “Complete” and “Incomplete” Active Directory evaluation.
You are missing a lot of other components for an Active Directory review if you only discuss the default assessment criteria, which are also often used by AD professionals and businesses. When it comes to conducting a security assessment of an Active Directory system, there are a few standard criteria that every AD professional is aware of. PowerShell scripts are easily accessible and can be used to check 50% of an Active Directory environment’s security, and 20% of PowerShell scripts for an Active Directory environment’s health. However, this does not necessarily imply that you can use these scripts to perform a “Complete” technical assessment of an Active Directory environment.
If a company claims to offer a “complete” technical evaluation for Active Directory, or, to put it another way, a complete cybersecurity assessment, I believe this to be discussed with the company offering the service. I have tested and reviewed several utilities and tools for Active Directory security assessment in order to understand what they cover as part of their AD evaluation, but none of them pay attention to “all” parameters. For instance, if you claim to verify (as part of the security assessment) “Ensure the AdminSDHolder object’s permissions are right”, you really fail to check the orphaned Admins in the domains which are directly related to the AdminSDHolder object. A User account that is not visible in Active Directory as an admin but still qualifies as an admin is known as an orphaned admin. These orphaned admins are actually used by SDProp process and consider them as an admin for permissions propagation. So orphaned admins are admins, but they are hidden is a security risk too. Similarly, if you check all Service Principals in a domain how are going to make sure those service principals are real and won’t cause any issues.
If some companies claim to be able to lower the Active Directory attack surface by around 70% or some number, you should inquire further or perform a more thorough evaluation to see whether they are genuinely able to do so. And if companies claim to be able to undertake a “complete” technical evaluation of an Active Directory system, then why do you believe the AD assessment services you’re planning to offer will be able to perform a thorough AD evaluation?
Take note that the phrase “Complete” suggests that every risk and their related items in Active Directory will soon be mitigated as part of the evaluation. Saying “Complete” demonstrates that your Active Directory environment is now safe and that no one can access it or breach into any domain joined devices.
The concepts “Complete Assessment” and “reducing attack surface by 75% or some number” need to be discussed as part of this section. In the context of an Active Directory evaluation, the term “Complete Assessment” refers to the parameters that were examined. Keep in mind that Active Directory consists of a variety of elements, and because of the complexity of its structure, you must include all of them, from user objects to NTDS Objects and lower-level attributes. Group Policy Objects are important to remember. Similar to this, it is impossible to disregard DNS tests that must be examined as part of the AD technical review. Your tool or technique must examine every component of Active Directory in order to provide a thorough technical evaluation. Even if you checked GPOs, DNS, AD Replication, domain configuration, domain controllers, and other things, failing to check other components would result in an “Incomplete” assessment. The issues that you fix as part of an Active Directory technical assessment may not remain resolved if an incomplete assessment is performed.
Try SmartProfiler, a unified tool to help with security evaluation across many Microsoft technologies.
A basic strategy to perform a “complete” assessment of an Active Directory should include two things:
It should be noted that the tool or software you choose for an AD technical assessment can assist you in identifying problems but cannot ensure that the Active Directory environment will be safe once the issues uncovered by the tool are fixed. For example, you can fix those issues identified by those general PowerShell scripts, but what if someone with a “Write” permission can undone the change made by you to appear that issue again? Based on the basic evaluation result provided by the tool/software, you will utilise your knowledge to analyse a number of different Active Directory environment factors. Keep in mind that every organisation wants our assistance and relies on us to make sure that their Active Directory environment is protected against intruders including ransomware attacks.
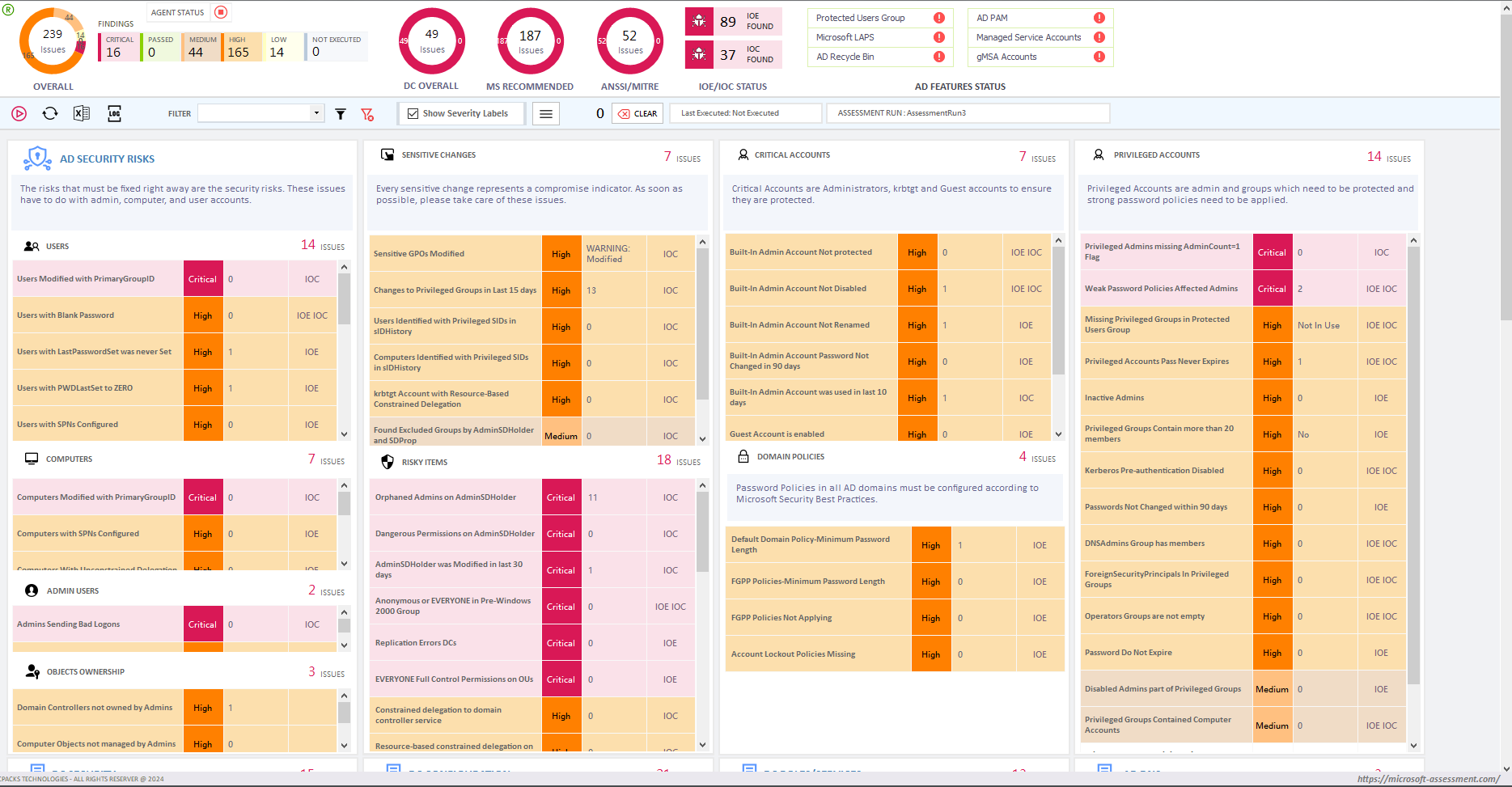
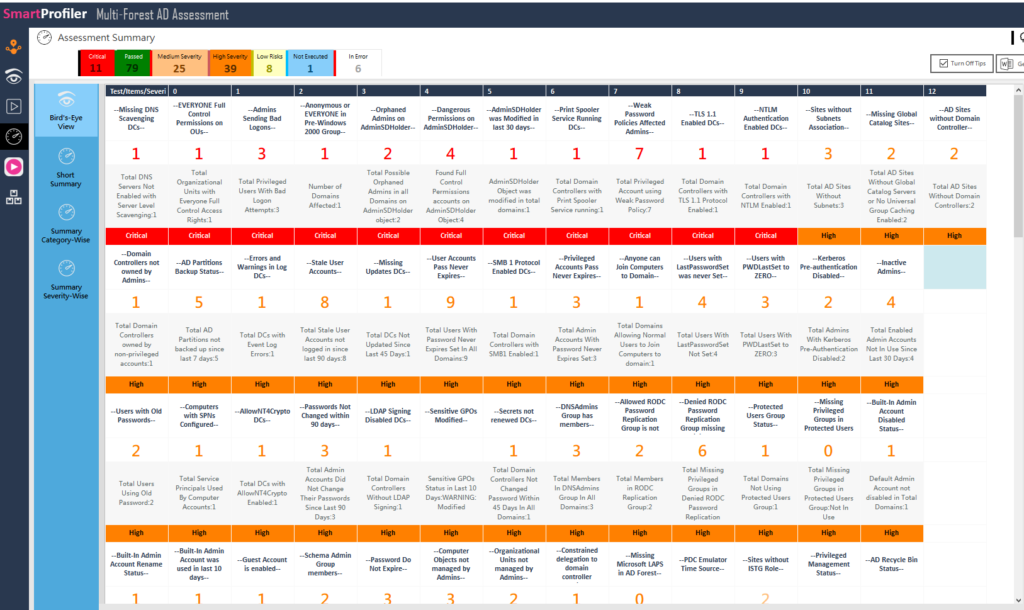
We were recently hired to do a review of the Active Directory assessment for a customer. We discovered a great deal of information that I won’t go into detail about here, but every interaction with a client teaches you more and improves your ability to assist them. All basic parameters and advanced parameters should be included in any tool or piece of software you choose to conduct an Active Directory assessment, depending on your level of Active Directory expertise. In my opinion, you should consider all the factors in the three main categories below while evaluating Active Directory. Each evaluation tool should include the following five fundamental assessment areas, whether it focuses on Active Directory, Office 365, or any other technology: Health Check, configuration errors, security risks, and noncompliance and Performance.
Health & Performance Parameters for Active Directory can help you understand if there are health issues with components such as KCC, NTDS, Domain Controllers, orphaned domain controllers, backup status of partitions, system state backup, domain controllers up time, domain controllers patching status, AD replication, domain controllers local disk configuration, DCDiag status and a few other parameters.
Misconfiguration entails the tool’s ability to identify and report misconfiguration items. In the context of Active Directory, this may cover aspects such as undefined subnets, AD Site Links, replication topology, time synchronization, Fine-Grained Password Policy (FGPP) parameters, Domain Account Policy parameters, strict replication, SMB1 protocol, unsecure updates, DNS scavenging, DNS round robin, manual connection objects, manual bridgehead servers, DNS static records and more.
Security and Risk assessment involves evaluating whether the tool can perform a comprehensive analysis of security vulnerabilities and risks. Specifically for Active Directory, this may include examining Lan Manager Hashes, SMB Signing, LDAP Signing, NT4Crypto, accounts with blank passwords, accounts using SPNs, unauthenticated domain controllers and servers, credential caching in RODC, duplicate SPNs, unprivileged accounts with excessive permissions on OUs, non-default principal accounts with full control or write permission on critical directory objects, anonymous access to AD, and numerous other AD security tests.
While the Assessment Categories assist in selecting the appropriate Active Directory Assessment tool, the Methodology provides an overall perspective for both the IT Management Team and IT Operations Team. The tool should adopt a methodology that caters to the needs of both teams. The methodology should include the following:
Once you have identified categories, you need to define sub-categories in each of the category to ensure you do not miss from the parent category point of view. For example, for Health Category, what all components of Active Directory you will be checking to ensure components are healthy and define those sub-categories for each component for example GPO sub-category. Similarly, what all parameters you need to check when it comes to check DNS in misconfiguration category. Now to define a complete picture of sub-categories associated with above categories here is a list of sub-categories:
Note that even if you include above sub-categories to be checked as part of the AD Assessment, the assessment still can’t be considered as “complete” assessment. As I stated earlier, the AD evaluation requires that you perform an assessment in above sub-categories, but still use your own experience to evaluate rest of the parameters based on the technical findings. Please check section “Advanced Assessment Parameters” in this article.
Coming back to the test parameters to be included in an Active Directory, there are actually many of them depending on how much experience you have working with Active Directory? If I am to provide you a list of test parameters for each sub-category, there could be more than 200. However, some of the basic assessment parameters are highlighted here:
| Sub-Category | Parameters |
| Account Policies | Ensure Domain Account Policies are configured correctly Ensure FGPP Policies have correct Password parameters configured Ensure FGPP Policies are applying to objects. |
| DNS | Ensure Domain Zone Scavenging is enabled Ensure Domain Zones have Secure Updates configured Ensure Domain Zone do not have Static Records Ensure DNS Servers are configured with Forwarders Ensure DNS Root Hints are configured Ensure DNS Round Robin is Enabled on DNS Servers Ensure DNS Servers have _msdcs zone hosted Ensure Conditional Forwarders Configured on DNS Servers are working Ensure DNS Server Level Scavenging is Configured Ensure Domain Controllers have Host Record Registered with correct IP Address |
| AD Forest | Ensure Active Directory do not have Orphaned Domain Controllers Ensure AD Forest TombstoneLifetime has not been modified Ensure no AD Forest Replication Errors Ensure AD Sites have Subnets Defined Ensure AD Site has Location Text Specified Ensure each AD Site has Global Catalog Role or Universal Group Caching is enabled Ensure AD Site has at least one Domain Controller Ensure AD Forest has ISTG Role defined in AD Sites Ensure Manual Replication Connection Objects are identified and removed Ensure AD FSMO Placement is as per Microsoft Recommendation Ensure Domain Naming Master and Schema Master are hosted on same domain controller Ensure AD Privileged Access Management is Enabled Ensure AD Recycle Bin Feature is Enabled |
| Configuration-Domain | Ensure No Empty Organizational Units in Domains Ensure No Empty Security Groups In AD Domains Ensure End Of Life Operating Systems and Unsupported Operating Systems are detected Ensure Managed Service Accounts are in use Ensure Managed Service Accounts Are Linked Ensure Domain Users have UPN Specified Ensure Orphaned Group Policy Containers are identified and removed |
How many times have you assessed an Active Directory environment for a client and seen users with unrestricted delegation, trusted for delegation, DES-Encryption enabled, and pre-authentication Kerberos disabled? So, a small business running Active Directory with two to five domain controllers should to be able to manage their AD infrastructure easily without the need for utilising the aforementioned settings for users. Unrestricted delegation, DES-Encryption for users, and deactivating pre-authentication Kerberos for users are not actually required. You would still need to complete the tests associated to users as part of the standard checklist included in the Assessment tool to make sure everything is in order for user objects. The advanced parameters of an Active Directory include but not limited to:
Let’s take a look at each of these topics one by one:
You will be evaluated on your Active Directory experience when you work with the advanced evaluation criteria. Let’s go over some of the factors for a complete Active Directory Security Assessment and how you might look into them more.
It completely depends on your basic assessment that you performed for the Active Directory before you can use your own experience in performing an advanced assessment.
Be aware that the assessment tool may not be able to gather all of the hundreds of settings listed in every Group Policy Objects if you do an Active Directory evaluation. All GPOs must be gathered, together with the parameters that are specified in each one. To gather all GPO settings, use a PowerShell script. You must run the following tests on the GPOs you have gathered:
Have you every thought that there are recommended GPO settings by the CIS and NIST which need to be configured and applied to every Domain Controller in an Active Directory Forest? Checking all GPO settings is required as part of the complete Active Directory Security Assessment. CIS stands for Center for Internet Security is a non-profit organization working closely with Microsoft to release standard benchmark for Microsoft technologies. CIS released standard GPO Settings to be applied for Domain Controllers running below Operating Systems:
SmartProfiler for Active Directory ships with CIS/NIST Analyzer module that can help you check CIS/NIST settings on your domain controllers.
Given that Active Directory is quite complicated when it comes to understanding its permissions structure, analysing organisational unit permissions is a challenging undertaking. The Active Directory permissions defined on Organisational Units and Tier 0 objects must be checked when doing an Active Directory assessment, though. Inability to do so would leave the consumer with an incomplete assessment. Let’s imagine that after fixing the problems found during the evaluation and completing the client interaction, you neglected to handle some of the abuseable permissions. In such situation, someone with a privilege that may be abused could acquire access to Active Directory and subsequently do bad things. So, keep the following things in mind while analysing permissions for an Active Directory environment:
Although Active Directory has a wide variety of objects, five of them are vulnerable to attack: the User, Computer (regular computer or domain controller), Managed Service Account, gMSA, and inetOrgPerson classes. In other words, whether the permissions are explicit or implicit (direct or indirect), Active Directory attack routes apply to an object that has a password associated with it and then those permissions that make the object a privileged account. Complete Active Directory Security Assessment often involves checking permissions assigned on Organizational Units and its structure.
If you’re referring to Azure Active Directory (Azure Entra ID), these attack paths would include Global Administrators, Guest accounts, Azure Applications, Azure application permissions, and a few other flags that all Hybrid Admin should be checking out. However, we will briefly discuss Azure AD (Entra ID) permissions and attack paths in another article.
Keep in mind that before performing an operation, Active Directory significantly relies on the permissions given to objects and the properties of objects. For instance, if I want to change someone’s password, I can only do so if I have been granted the Password Reset permissions, am a part of a security group that has already been granted the Password Reset Permissions, or am a member of a security group that has the ability to change an object’s password by default. Password Reset authority is “indirectly” granted to Domain Admin. In the same way, in order for me to remove an item, I must first have those permissions granted to me.
Active Directory’s structure is complicated because of its design. It might be a direct assignment, the user could be a member of a group that has Password Reset permission assigned, or the user could be a member of a group that explicitly has Password Reset permission, such as the Domain Admins group. The largest issue to date is assessing the rights given to objects in Active Directory. Before delving into Active Directory permissions, let’s look at the many types of actions that may be carried out there:
However, note that these operations will occur with the help of three types of standard permissions: Read, Write (Modify), Full Control.
The two interesting standard permissions are “Write” and “Full Control”; occasionally, AD refers to “Full Control” as “Generic All”. It’s important to understand that a write action on an object in Active Directory might occur at multiple places for the same object, as indicated below:
Remember that not all permissions in Active Directory begin with the word “Write”? That’s another challenging aspect. While some permissions go by a different name, they really write to the object. “Self” permission is one of the illustrations. The “Self” permission enables a user to belong to the target security group. For instance, I may join the group myself if I have the “Self” permission. Is it confusing that a permission with the name “Self” is also carrying out a write operation? If the word “Write” had been the first word in each permission that actually performs the task of writing to an object, things would have been much simpler! It’s okay though because this is how the AD developed.
Actually, in addition to using permissions to take over Active Directory or its objects, attackers may also leverage other weak properties. Not all of these attributes will be explained in this article. Here is a list of permissions that attackers are more likely to be interested in and can use or assign themselves in order to take control of Active Directory as we continue our study of permissions. For our discussion, however, and to make sure you understand the difference between changing an object’s property and the whole object, I have produced a table that indicates if that permission would change the entire object or simply its property:
| Permission | Description | Affecting | Property Name |
| WriteProperty | Ability to modify a specific property. | Property | Any property, but the actual permission entry will list which property can be written. The permission entry if reports “All” that means all properties of the target can be modified. |
| WriteDACL | Ability to modify permissions of an object. | Property | ntSecurityDescriptor (SDDL) of the target object. |
| Ownership or Owns | Assigned Object becomes the owner of the object. | Object | All Properties |
| ManagedBy | |||
| WriteOwner | Ability to change ownership of an object. The right to assume ownership of the object. The user must be an object trustee. The user cannot transfer the ownership to other users, but user can just write to the owner property. | Property | ADS_RIGHT_WRITE_OWNER (part of SDDL or set in ntSecurityDescriptor). There is no property associated with it. |
| GenericWrite | The ability to write all the properties on this object, and perform all validated writes to this object. | Object | All Properties |
| Self | The ability to add self to a Security Group. | Object | Member Attribute |
Note: In a subsequent article, I want to go into further depth on Active Directory Permissions. Attackers frequently exploit the aforementioned permissions to access Active Directory, though.
Your assistance is now needed to resolve the noted problems once the evaluation was completed. Whether they are GPO issues, permission issues, important issues, high, medium, or low issues, each one needs to be carefully examined before being resolved.
The whole purpose of investigating Active Directory is to ensure you identify and fix those “ghost” entries/issues. A ghost entry in Active Directory is an object that is unknown to “administrators”. A ghost entry is always an object that has a password associated with it. If you can find and fix those ghost entries/issues, then you can eliminate 95% of attacks in Active Directory. Those 5% you can’t eliminate as those 5% belong to “social engineering” where one admin supplies credentials to an attacker or create a user account with necessary permissions required for attacking active directory.
In this section we will learn how you can fix those issues identified during the basic and advanced assessment stages. We will look at below:
Many Active Directory specialists, according to what I’ve observed, have recommended disabling TLS 1.1, NTLM, RC4, and other things that were discovered during the Active Directory evaluation. But it’s important to remember that you can’t just address the problems if you don’t have a plan for doing so. To put it another way, you must evaluate the customer’s environment in relation to the problem you want to fix. For instance, if you choose to disable the TLS 1.1 protocol in Active Directory, you must first confirm with the client that none of their apps use the protocol or are enforcing it. So keep the following strategy in mind when fixing problems in the Active Directory environment:
Create an excel sheet with a summary of the problems you noticed, and the columns mentioned above. Make sure that the customer is aware of your plan for resolving the issue.
It’s not required to address every issue separately. Some of the issues are automatically resolved if you resolve another problem. For instance, problems with errors and warnings on the domain controllers will be resolved immediately if the Active Directory replication topology is corrected and related issue is fixed. Here, you must take some time to sit down and go over each issue one at a time. Then, using your own logic and experience, you must determine whether any of these issues may be resolved by addressing others.
You need to be addressing those permissions in such a way that customer understands the need for assigning these permissions. For example, you decide to remove full control permission for a Service Account, but you don’t know what an application does as part of the permissions assignment then it is important to know what actual permissions are required by the application to ensure it can work without assigning Full Control permissions to the organizational unit or OU. When fixing Active Directory permissions, take following approach:
SmartProfiler for Active Directory ships with AD Issues Fixer which can also be used to fix critical, medium, high and low issues using the built-in component:
An Active Directory Tiering model can help you streamline your permissions structure. You need to define an structure for managing Tier 0, Tier 1 and Tier 2 objects in Active Directory if its not implemented you are required to work with the customer and have it implemented. There are several benefits associated with Active Directory Tiering management as listed below:
When working on a tiering model for customer, ensure to collect required information from the customer by having a discussion with them on the following topics:
Note that these “Managed Objects” can be Tier 0, Tier 1, or Tier 2 objects, but let’s not get into details as to understand what are Tier 0, Tier 1 and Tier 2 objects. If you can define all objects in an excel sheet under the “AD Managed Objects” category, then all you need to is just put a check mark in respective column indicating that the object can be managed by the respective Tier Admin.
There could be multiple admins that can be defined a Tier Admins. You need to work with the customer to help you understand their current management model for managing these AD Managed Objects.
Please take a note that all objects in an Active Directory environment can be read by an authenticated user. You may want to block read access to some critical objects depending on the assessment outcome and your discussion with the customer. If you find that some important organizational units contain some important objects that are very critical to the business, then you must block read access to these objects and organizational units and also apply a logical thought process to ensure only allowed users can access or read those objects.
Active Directory engagements that are reactive don’t benefit your customer. It could help you earn some money, but it doesn’t benefit the consumer in any way. The customer you deal with for an Active Directory assessment engagement has high expectations of you, since you are more knowledgeable about technology, and you are the technology leader. If you only run the tool and address the problems you identified during the evaluation, you cannot consider the engagement to be finished. Making the assessment and addressing the problems identified during the assessment are examples of a reactive strategy. While a proactive strategy involves putting in place the essential safeguards to secure and protect the customer’s environment against problems/disasters. What other controls do you believe you could put in place as part of a proactive strategy, now? Your prior expertise is helpful in this situation. If you have experience with such engagements, you are aware of the controls you must put in place to safeguard the environment of your clients. For instance, a client could be using a pricey solution to fully backup and snapshots of Active Directory domain controllers, but failing to take a system state backup poses a serious risk in the event that Active Directory needs to be restored following a disaster. You may wish to compile a list of documents and develop a mitigation strategy while assessing the environment of a client in order to avoid failures in the near future. These documents should include:
The scheduler that comes with the assessment tool allows you to set up all or some checks as part of the schedule. The scheduler runs at pre-defined intervals and provides you warnings if it discovers any critical or high concerns. Keep in mind that you must perform the assessment checks each week to make sure the problems you found and resolved as part of the remediation services do not come up again. You need to start working on the mitigation plan at this point.
To satisfy the needs of a proactive Active Directory engagement, DynamicPacks Technologies has worked very hard to redesign the SmartProfiler for Active Directory and to ensure you are able to perform a complete Active Directory Security Assessment. When you propose Active Directory engagement to your customer, you are doing so with a complete Active Directory security assessment package that includes an issues fixer to address issues, a permissions analyzer and fixer to examine and address permissions, a scheduler to plan assessments, an operational scheduler to run operational scripts at pre-defined intervals, and many other features that will help with the assessment and allow for a quick evaluation. Note that SmartProfiler performs Active Directory advanced assessment based on the recommendations highlighted by ANSSI, MITRE and Microsoft.
As you can see in the Assessment Dashboard below generated by SmartProfiler for Active Directory,
Try SmartProfiler, a unified tool to help with security evaluation across many Microsoft technologies.