Microsoft Active Directory Indicators

22 Health Checks
282 Security Checks
59 Configuration Checks
SmartProfiler for Active Directory can look for both Security Indicators; Indicator Of Exposure (IOE) and Indicator Of Compromise (IOC).
Evidence that someone may have accessed a network or endpoint within an organization is known as an indicator of compromise, or IOC. This forensic data not only points to a possible danger, but also indicates that an attack—such as one involving malware, credential theft, or data exfiltration—has already taken place. Event logs, extended detection and response (XDR) systems, and security information and event management (SIEM) systems are the places where security experts look for IOCs. The team use IOCs to neutralize threats and minimize damage during an attack. IOCs aid an organization’s security team in strengthening security and lowering the likelihood of a recurrence of a similar incident by providing a deeper understanding of what transpired after recovery.
“Indicators of Exposure” describes various attack vectors that could be easily exploited by hackers to get access to a company. These attack vectors could include misconfigured or Active Directory components.
SmartProfiler for Active Directory supports Security Indicators recommended by ANSSI, MITRE and Microsoft.
Active Directory Security Indicators - RISKY ITEMS CHECKS
| Orphaned Admins on AdminSDHolder | IOC |
| Dangerous Permissions on AdminSDHolder | IOC |
| AdminSDHolder was Modified in last 30 days | IOC |
| Constrained delegation to domain controller service | IOC |
| Resource-based constrained delegation on domain controllers | IOC |
| Anonymous Access to Active Directory | IOE |
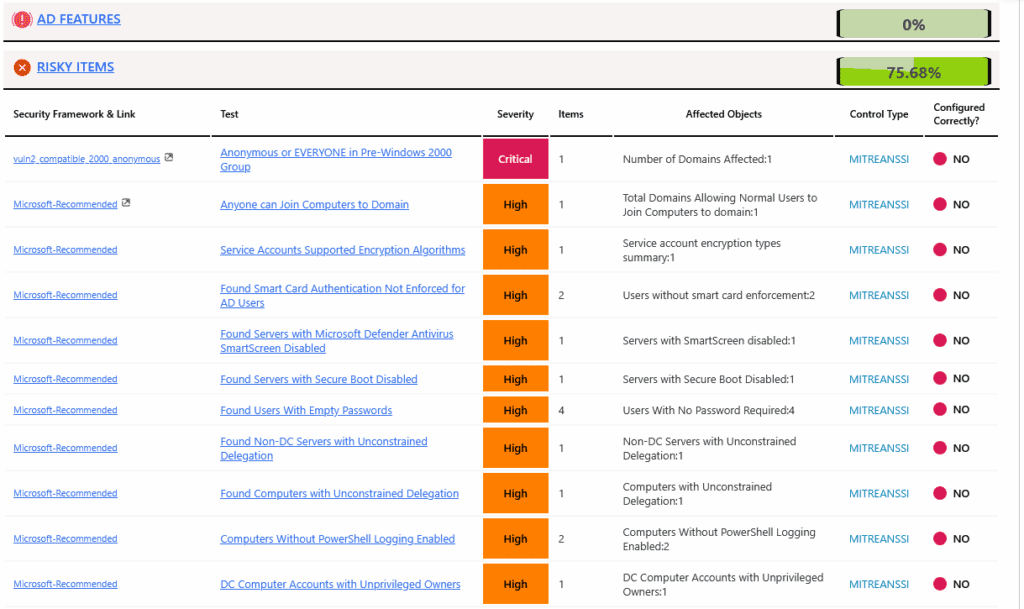
| Anonymous or EVERYONE in Pre-Windows 2000 Group | IOE IOC |
| Potentially Sensitive Information Found in User Description Field | IOE IOC |
| Found Hidden Domain Controllers | IOE |
| Successful Exploit Machine Accounts Found | IOE |
| Possible User-based Service Accounts found | IOC |
| Objects Modified in Last 10 Days | IOE IOC |
| Objects Created in Last 10 Days | IOE IOC |
| Domain Trusts Found | IOE IOC |
| Anyone can Join Computers to Domain | IOE |
| Replication Errors DCs | IOE |
| Normal Users Full Control Permissions on OUs | IOE |
| EVERYONE Full Control Permissions on OUs | IOE |
| Allowed RODC Password Replication Group is not empty | IOE |
| Found Privileged Groups in msDS-RevealOnDemandGroup of RODC | IOE |
| Managed service accounts with passwords unchanged for more than 90 days | IOE |
| Denied RODC Password Replication Group missing Privileged Accounts | IOE |
| msDS-NeverRevealGroupattribute RODC missing Privileged Accounts | IOE |
| Schema Admin Group members | IOE |
| Unsecure Updates Zones | IOE IOC |
| Missing Domain Zones Scavenging | IOC |
| AD Partitions Backup Status |
| Users with Blank Password | IOE IOC |
| Users with LastPasswordSet was never Set | IOE |
| Users with PWDLastSet to ZERO | IOE |
| Users with SPNs Configured | IOE |
| Password Expiration is misssing for smart card users | IOE |
| Accounts vulnerable to Kerberoasting Found | IOE |
| Users With DES encryption | IOE |
| Users With Reversible Encryption | IOE |
| Users With Kerberos Pre-Authentication | IOE |
| Users Modified with PrimaryGroupID | IOC |
| Users Sending Bad Logons | IOC |
| Users Disabled | IOC |
| Stale User Accounts | IOC |
| Users Expired | IOC |
| User Accounts Pass Never Expires | IOC |
| User Accounts Pass Not Required | IOC |
| Computers with SPNs Configured | IOE |
| Computers With Unconstrained Delegation | IOE |
| Computers Modified with PrimaryGroupID | IOC |
| Computers Sending Bad Logons | IOC |
| Computers Disabled | IOC |
| Stale Computer Accounts | IOC |
| Unsupported Operating Systems | IOE |
| Admins with SPNs Configured | IOE |
| Admins Sending Bad Logons | IOC |
| Domain Controllers not owned by Admins | IOC |
| Computer Objects not managed by Admins | IOC |
| Organizational Units not managed by Admins | IOC |
| Sensitive GPOs Modified | IOC |
| Recently Created Privileged Admins | IOC |
| Changes to Privileged Groups in Last 15 days | IOC |
| Users Identified with Privileged SIDs in sIDHistory | IOC |
| Computers Identified with Privileged SIDs in sIDHistory | IOC |
| Found Excluded Groups by AdminSDHolder and SDProp | IOC |
| krbtgt Account with Resource-Based Constrained Delegation | IOC |
| Built-In Admin Account Not protected | IOE IOC |
| Built-In Admin Account Not Disabled | IOE IOC |
| Built-In Admin Account Not Renamed | IOE |
| Built-In Admin Account Password Not Changed in 90 days | IOE |
| Built-In Admin Account was used in last 10 days | IOC |
| KRBTGT Account Password Not Changed | IOE |
| Guest Account is enabled | IOE |
| Administrator Account ServicePrincipalNames Found | IOE |
PRIVILEGED ACCOUNTS CHECKS
| Misconfigured Administrative Accounts Found | IOE IOC |
| Missing Privileged Groups in Protected Users Group | IOE IOC |
| Privileged Accounts Pass Never Expires | IOE IOC |
| Too Many Privileged Accounts | IOC |
| Inactive Admins | IOE |
| Privileged Groups Contain more than 20 members | IOE |
| Kerberos Pre-authentication Disabled | IOE IOC |
| Disabled Admins part of Privileged Groups | IOE |
| Passwords Not Changed within 90 days | IOE |
| DNSAdmins Group has members | IOE IOC |
| Privileged Groups Contained Computer Accounts | IOE IOC |
| Privileged Admins missing AdminCount=1 Flag | IOC |
| ForeignSecurityPrincipals In Privileged Groups | IOE IOC |
| Operators Groups are not empty | IOE IOC |
| Weak Password Policies Affected Admins | IOE IOC |
| Password Do Not Expire | IOE |
| AdminsCount Flag set users not acting as Admins | IOC |
| Sensitive GPOs Modified | IOC |
| Recently Created Privileged Admins | IOC |
| Changes to Privileged Groups in Last 15 days | IOC |
| Users Identified with Privileged SIDs in sIDHistory | IOC |
| Computers Identified with Privileged SIDs in sIDHistory | IOC |
| Found Excluded Groups by AdminSDHolder and SDProp | IOC |
| krbtgt Account with Resource-Based Constrained Delegation | IOC |
| Default Domain Policy-Minimum Password Length | IOE |
| FGPP Policies-Minimum Password Length | IOE |
| FGPP Policies Not Applying | IOE |
| Account Lockout Policies Missing | IOE |
| High Value Targets Found | IOE IOC |
| Accounts with Extended Rights to Read LAPS Passwords Found | IOE IOC |
| Access Control Lists on Computers Found | IOE IOC |
| Access Control Lists on Security Groups Found | IOE IOC |
| Access Control Lists on Users Found | IOE IOC |
| Group Policy Objects with Improper Permissions Found | IOE IOC |
| Group Policy Object Assignments with Improper Permissions Found | IOE IOC |
| Dangerous Permissions Found on MicrosoftDNS Container | IOE IOC |
| Dangerous Permissions Found on Naming Contexts | IOE IOC |
| Outbound forest trust relationships with sID History enabled | IOE IOC |
| Trust account passwords unchanged for more than a year | IOE IOC |
| Pre-Windows 2000 Compatible Access Group is not empty | IOE IOC |
| Found Groups with SID history Set | IOE IOC |
| PDC Emulator Time Source | |
| Domain Controllers Time Source | |
| Domain FSMO Placement | |
| Domain Naming Master and Schema Master Placement |
DOMAIN CONTROLLER CHECKS
| Domain Controllers Modified with PrimaryGroupID | IOC |
| SMB 1 Protocol Enabled DCs | IOE |
| AllowNT4Crypto DCs | IOE |
| LAN Manager password hashes Enabled DCs | IOE |
| SMB Signing Disabled DCs | IOE |
| LDAP Signing Disabled DCs | IOE |
| TLS 1.1 Enabled DCs | IOE |
| NTLM Authentication Enabled DCs | IOE |
| Inconsistent DCs | IOE |
| RC4 Encryption Enabled DCs | IOE |
| Unauthenticated DCs since last 45 Days | IOE |
| Secrets not renewed DCs | IOE |
| Managed Service Accounts Not Linked | IOE |
| Missing Updates DCs | IOE |
| Missed Reboot Cycles DCs | IOE |
| No Contacts with Domain Controllers in Last Three Months | IOE |
| Orphaned DCs | IOE |
| Missing DNS Scavenging DCs | IOE |
| Missing DNS Forwarders DCs | IOE |
| Missing Root Hints DCs | IOE |
| Missing Host Records DCs | IOE |
| Not Enough Free Space DCs | IOE |
| Errors and Warnings in Log DCs | IOE |
| Loopback Address Missing DCs | IOE |
| Multihomed DCs | IOE |
| Missing SSL Authentication DCs | IOE |
| NTFS Replication DCs | IOE |
| Strict Replication Disabled DCs | IOE IOC |
| DCDiag Failure DCs | |
| Out Of Default OUs DCs | |
| Unsupported OS DCs | IOE |
| Missing Enough DNS Servers in NIC DCs | |
| Not Enough Local Disks DCs | |
| Missing DNS Dynmaic Registration on NIC DCs | |
| Missing _msdcs Zone DCs | |
| Event Log Config Not Correct DCs | |
| Event Log Size Not Optimized DCs | |
| Scheduled Tasks found on Domain Controllers | IOC |
| Fax Server role installed DCs | IOE |
| Microsoft FTP service installed DCs | IOE |
| Peer Name Resolution Protocol installed DCs | IOE |
| Simple TCP-IP Services installed DCs | IOE |
| Telnet Client installed DCs | IOE |
| TFTP Client installed DCs | IOE |
| Server Message Block (SMB) v1 protocol Installed DCs | IOE |
| Windows PowerShell 2.0 installed DCs | IOE |
| Print Spooler Service Running DCs | IOE |
| ADWS Service Set to Manual DCs | IOE |
| DHCP Service Running DCs | IOE |
| Additional Roles and Features DCs | IOE |
| AD Services not running DCs | IOE |
| Software Installed on Domain Controllers | IOE |
Active Directory Assessment Tests with Impact Description
| Category | Test Type | Test | Impact If not addressed |
| Active Directory Reporting | Reporting | Get AD Subnets Count Per Site | If addressed: Accurately managing the count and assignment of subnets per Active Directory site ensures clients authenticate and replicate with the correct Domain Controllers, optimizing network traffic and performance.
If not addressed: : Incorrect or missing subnet assignments can cause clients to connect to distant or inappropriate Domain Controllers, leading to authentication delays, inefficient replication, and increased network load. |
| Active Directory Reporting | Reporting | Get AD Forest Info and FSMO | If addressed: Properly identifying and managing Active Directory forest information and FSMO (Flexible Single Master Operations) role holders ensures domain stability, prevents conflicts, and supports efficient replication and authentication services.
If not addressed: : Failure to monitor FSMO roles and forest configuration can lead to role conflicts, service disruptions, replication failures, and increased risk of domain-wide outages. |
| Active Directory Reporting | Reporting | Get AD Forest Site Info | If addressed: Properly gathering and managing Active Directory forest site information ensures accurate site configuration, enabling efficient authentication, replication, and service localization, which enhances overall network performance and reliability.
If not addressed: : Without accurate site info, clients and services may experience authentication delays, replication inefficiencies, and suboptimal network traffic, leading to potential downtime and degraded user experience. |
| Active Directory Reporting | Reporting | Get AD Forest Site Link Info | If addressed: Properly managing and monitoring Active Directory site link information ensures efficient replication traffic and optimal authentication routing, which improves network performance and reduces replication latency.
If not addressed: : Neglecting site link configurations can cause replication delays, increased network congestion, and authentication issues, potentially leading to data inconsistencies and degraded user experience. |
| Active Directory Reporting | Reporting | Get Domain Controller Info | If addressed: Properly gathering and securing Domain Controller (DC) information ensures administrators have accurate insights to maintain, monitor, and protect DCs, reducing risks of misconfiguration and unauthorized access.
If not addressed: : Lack of up-to-date or accurate DC information can lead to security gaps, poor management, delayed incident response, and vulnerabilities in domain infrastructure. |
| Security and Risk | MITREANSSI |
Ensure Active Directory have no Stale Computer Accounts | If addressed:
Improves directory hygiene by removing unused computer accounts and reducing exposure to dormant endpoints.
If not addressed: :
Old machine accounts may be reused or exploited to gain access without triggering alerts. |
| Security and Risk | MITREANSSI |
Ensure Active Directory have no Stale User Accounts | If addressed:
Reduces attack surface by disabling or removing unused accounts that may otherwise be exploited.
If not addressed: :
dormant accounts may be leveraged for privilege escalation or persistence without detection |
| Security and Risk | MITREANSSI |
Ensure Disabled Computers are identified and moved to OU | If addressed:
Enhances security by isolating unused or decommissioned computers Keeps Active Directory clean and well-organized Simplifies management and reduces clutter in production OUs Supports compliance and better audit readiness
If not addressed: :
Disabled computers may clutter AD, making management harder Increases risk of misconfiguration or accidental reactivation Can lead to security gaps and audit issues Wastes administrative time and resources. |
| Security and Risk | MITREANSSI |
Ensure Disabled Domain Users are identified and moved to OU | If addressed:
Enhances security by isolating disabled accounts Improves AD organization and simplifies audits Reduces risk of accidental reactivation or misuse
If not addressed: :
Disabled user accounts may remain scattered and unmanaged Increases risk of unauthorized access or misconfiguration Causes clutter and confusion in Active Directory |
| Security and Risk | MITREANSSI |
Ensure Active Directory do not have Expired Accounts | If addressed:
Prevents unauthorized access from expired but active accounts
Strengthens security and access control
Ensures compliance with access management policies
If not addressed: :
Expired accounts may still be active, posing a security risk
Violates compliance or audit standards
Increases risk of unauthorized or unintended access to systems |
| Configuration-Forest | Configuration |
Ensure Active Directory Sites are Covered by each other | If addressed:
Ensures reliable authentication and replication across sites
Improves logon performance and application access for users in all sites
Supports fault tolerance-sers can authenticate even if local DC is unavailable
If not addressed: :
Users may experience logon failures or delays
Domain controllers may not replicate properly across sites
Risks in availability during site or DC failures
Poor performance due to cross-site traffic for authentication |
| AD Forest | HealthCheck |
Ensure Active Directory do not have Orphaned Domain Controllers | If addressed:
Removes defunct or improperly demoted DC entries, ensuring a clean and accurate directory.
If not addressed: :
Orphaned DC metadata may cause replication errors, delays, and unpredictable AD behavior. |
| Security and Risk | MITREANSSI |
Ensure Domain Controllers are not in Inconsistent State | If not addressed: :
Replication failures between DCs
Login/authentication issues
Group Policy misapplication
Security risks (e.g., stale credentials)
Application/service failures
If addressed:
Reliable authentication and access
Consistent Group Policy enforcement
Healthy AD replication
Stronger security posture
Fewer user and system issues |
| Security and Risk | MITREANSSI |
Locked Out Accounts Found | If addressed:
Enforces lockout thresholds to prevent brute-force attacks on user accounts.
If not addressed: :
accounts remain susceptible to unlimited login attempts, increasing risk of password-guessing attacks. |
| Group Policy | Configuration |
Ensure GPO Naming Convention follows Standard Convention | If not addressed: :
Confusion over GPO purpose or scope
Risk of misconfiguration or duplication
Harder to audit, troubleshoot, or manage GPOs
Inconsistent practices across teams
Difficulty identifying critical vs. test policies
If addressed:
Clear and consistent GPO purpose/ownership
Easier auditing and compliance
Faster troubleshooting and management
Reduced risk of accidental changes
Scalable GPO management across teams |
| Group Policy | Configuration |
Ensure Domain GPO Description is set | If not addressed: :
Unclear GPO purpose or function
Increased risk of accidental deletion or misconfiguration
Harder to audit or troubleshoot
Slower onboarding for new admins
Poor GPO lifecycle management
If addressed:
Clear understanding of GPO purpose and owner
Easier maintenance and auditing
Improved collaboration across teams
Reduced risk of mistakes
Faster issue resolution |
| Configuration-Forest | Configuration |
Ensure Active Directory does not have Duplicate Site Links | If not addressed: :
Replication confusion and inefficiency
Increased replication traffic and latency
AD topology calculation issues by KCC
Difficulty troubleshooting replication issues
Possible replication loops or failures
If addressed:
Optimized and predictable AD replication
Accurate site-to-site replication mappingEasier troubleshooting and maintenanceReduced unnecessary replication traffic
Improved AD performance and reliabilit |
| Configuration-Forest | Configuration |
Ensure Active Directory has an Automatic Selected BridgeHead Server Configured | If not addressed: (Manually Selected Bridgehead Servers):
Risk of replication failures if the selected server is offlinePoor fault tolerance -replication won’t reroute automatically
Increased administrative overhead to manage changesPotential bottlenecks or delays in inter-site replication
Scalability issues in larger environments
If Addressed (Automatically Selected Bridgehead Servers):
High availability and resilience in replication paths
KCC automatically selects the best server per site
Reduced risk of single points of failure
Simplified replication management
Better performance and scalability |
| Configuration-Forest | Configuration |
Ensure Active Directory has No Manual BridgeHead Servers Configured | If not addressed: (Manual Bridgehead Set):
Single Point of Failure: If the chosen server is offline, inter-site replication can fail.
No Automatic Failover: KCC (Knowledge Consistency Checker) can’t dynamically choose alternatives.
Harder to Manage: Adds admin overhead and increases complexity.Poor Scalability: Becomes problematic in large or changing environments.
Unbalanced Load: Some DCs may become overloaded while others are underutilized.
If Addressed (No Manual Bridgehead Set):
Automatic Failover: KCC can select the best available DC for replication.
Improved Resilience and Uptime
Easier Maintenance: No manual updates needed when adding/removing DCs.
Load Balancing: Replication loads are better distributed.
Scalable and Future-Proof |
| Configuration-Forest | Configuration |
Ensure AD Sites do not contain more than two AD Sites | If not addressed: (Site Links with >2 Sites):
Complex replication paths, hard to troubleshoot
Unpredictable replication flow, especially during failure or congestion
KCC inefficiencies, making suboptimal replication decisions
Higher risk of replication delays in larger environments
Difficult to apply custom schedules or costs per site-to-site pair
If Addressed (Only 2 Sites per Site Link):
Predictable and optimized replication paths
Simplified topology management and troubleshooting
More granular control of replication costs and schedules
Improved KCC performance
Better scalability and fault isolation |
| Configuration-Forest | Configuration |
Ensure AD Site Replication Interval is configured Per Microsoft Recommendation | f NOT Addressed (Incorrect Replication Interval): Too Frequent Replication – Wastes bandwidth, especially over slow WAN links Too Infrequent Replication – Causes delayed AD updates, login/auth failures, stale data Inconsistent replication behavior across sites Unoptimized network performance Poor user experience and potential security risks If Addressed (Configured Per Microsoft Recommendation): Balanced performance and consistency across AD Efficient bandwidth usage Timely replication of changes (passwords, group updates, etc.) Improved user authentication reliability Better supportability and alignment with Microsoft guidance |
| Configuration-Forest | Configuration |
Ensure AD Sites have at least two Domain Controllers for Redundancy | If not addressed: (Only One DC in Site):
Single Point of Failure -if that DC fails, users may experience:
Login failures
GPO/application errors
Replication delays
No local replication partner -increases latency and reliance on other sites
Reduced availability, especially in distributed or remote locations
Higher risk of business disruption during patching, upgrades, or outages
If Addressed (At Least Two DCs per Site):
High availability for authentication and replication
Improved fault tolerance and load balancing
Local replication partner -faster and more efficient updates
Minimal service disruption during maintenance or failure
Scalable and resilient AD design |
| Configuration-Forest | Configuration |
Ensure AD Sites are in Site Links | If not addressed: (Sites Not in Site Links):
No replication between isolated sites
Stale or inconsistent directory data at those sites
Authentication delays or failures for users
Group Policy and login script issues
Increased risk of operational disruption and security risks
If Addressed (All Sites Included in Site Links):
Reliable and predictable replication between sites
Consistent and up-to-date directory data
Better fault tolerance and performanceImproved user experience and security complianceEasier AD topology management |
| Security and Risk | Configuration |
Ensure GPOs are applying to Objects | If not addressed: (GPOs Not Applying):
Policies do not enforce required settings
Security gaps and compliance risks
Inconsistent user and computer configurations
Troubleshooting complexity and user frustration
Potential operational disruptions
If Addressed (GPOs Applying Correctly):
Consistent policy enforcement across users and computers
Improved security and compliance posture
Predictable system behavior and configurations
Easier troubleshooting and management
Enhanced user productivity and experience |
| Configuration-Forest | Configuration |
Check AD Forest Functional Level | If not addressed: (Using Outdated/Lower Functional Level):
Limited access to latest Active Directory features
Compatibility issues with newer Windows Server versions
Increased security risks due to missing enhancements
Reduced manageability and functionality
Potential application and service incompatibilities
If Addressed (Appropriate or Latest Functional Level):
Access to latest AD features and security improvements
Better support for modern authentication and replication
Improved performance and manageability
Compatibility with latest Windows Server OS and apps
Stronger security posture |
| Configuration-Forest | Configuration |
Check AD Domain Functional Level | If not addressed: (Using Lower Domain Functional Level):
Limited access to advanced AD domain features (like Fine-Grained Password Policies, SID History improvements)
Compatibility issues with newer Windows Server versions or apps
Security features may be missing or outdated
Reduced management and automation capabilities
Potential issues with cross-domain trusts and replication
If Addressed (Domain Functional Level Raised Appropriately):
Access to latest AD domain features and security enhancements
Better integration with modern systems and services
Improved authentication, replication, and trust functionalities
Simplified administration and policy enforcement
Stronger security and compliance |
| Security and Risk | MITREANSSI |
Ensure Organizational Units are protected from Accidental Deletion | If not addressed: (OUs Not Protected):
Accidental deletion of entire OUs, including:
Users
Computers
Group Policies
Security groups
Service disruption, user login issues, GPO loss
Data recovery complexity and downtime
Increased risk of human error during AD cleanup or scripting
If Addressed (OUs Protected):
Prevents accidental deletions of critical AD objects
Protects integrity of user and computer accounts
Reduces administrative risk
Supports compliance and change control policies
Easier recovery planning and safer AD operations |
| Configuration-DomainController | HealthCheck |
Ensure Domain Controllers DNS Loopback Address Configured | If not addressed: (Loopback Not Configured or Misconfigured):
Domain Controller (DC) may fail to resolve its own name
Group Policy and AD replication issues
Login/authentication failures for users and computersIncreased dependency on external or other DNS serversReduced resiliency in DNS and AD services
If Addressed (Loopback Correctly Configured):
DC can always resolve its own hostname
AD services remain stable even if network issues occur
Improved DNS and replication reliability
Faster name resolution on the local machine
Improved fault tolerance and performance |
| Configuration-DomainController | HealthCheck |
Ensure NIC on Domain Controllers Have DNS Dynamic Update Configured | If not addressed: (DNS Dynamic Update Disabled):
DC may fail to register its A and PTR records in DNS
Other machines may not be able to locate or resolve the DC
Authentication failures, replication issues, and GPO processing errors
Event log warnings like 5774, 5781, or 5783
Manual intervention needed to register DNS records
If Addressed (DNS Dynamic Update Enabled):
DC automatically updates its DNS records (A, PTR)
Ensures reliable name resolution across the domain
Stable Active Directory and replication functionalityFewer DNS-related errors and event log warningsImproved resiliency and manageability |
| Configuration-DomainController | HealthCheck |
Ensure Domain Controller is not a Multihomed Domain Controller | If not addressed: (DC is Multihomed – Has Multiple NICs/IPs):
Unreliable DNS registration (multiple A records for one DC)
AD replication failures due to unreachable or incorrect IPs
Kerberos and authentication issues
Inconsistent name resolution (clients may resolve the wrong IP)
Complex firewall, routing, and security configurations
Increased risk of misconfiguration and service disruption
If Addressed (Single NIC and IP per DC):
Stable and consistent DNS records
Reliable replication and authentication
Simpler network and security configurationReduced troubleshooting complexityImproved AD performance and reliability |
| Security and Risk | MITREANSSI |
Ensure Domain Controllers are fully updated | If addressed:
Ensures DCs are protected with the latest security patches and bug fixes.
If not addressed: :
Unpatched domain controllers may be vulnerable to known exploits and zero-day attacks |
| Configuration-Forest | HealthCheck |
Ensure AD Partitions are Backed up regularly | If not addressed: (No Regular AD Partition Backups):
-Permanent loss of Active Directory data in case of corruption, deletion, or failure Unable to restore users, computers, GPOs, DNS records, or domain structure Increased downtime and recovery time during a disaster.
-Higher risk of security breaches or compliance violations
-No authoritative restore option availableIf Addressed (Regular Backups in Place):
-Ability to recover from accidental deletion or corruption
-Meets disaster recovery and compliance requirements
-Supports authoritative/non-authoritative restores
-Faster incident response and minimal disruption
-Ensures data integrity and security |
| Group Policy | Configuration |
Ensure GPOs are Linked to Organizational Units | If not addressed: (GPOs Not Linked to Any OU):
-Group Policies do not apply to any users or computers Security, compliance, or configuration settings are unenforced.
-Creates management confusion (ghost GPOs not doing anything)
-Wasted administrative effort maintaining unused policies
-Increased risk of misconfiguration, drift, or policy gapsIf Addressed (GPOs Properly Linked to OUs):
-GPO settings are enforced across targeted users and computers
-Centralized configuration and security control
-Ensures policy compliance and operational consistency
-Cleaner GPO structure and easier troubleshooting
-Improved performance by removing unnecessary/unlinked GPOs |
| Domain Controller | HealthCheck |
Ensure Domain Controllers have been rebooted once in 30 days | If addressed:
-Helps ensure patch installations are completed and system performance remains stable.
If not addressed: :
-Pending reboots can leave updates incomplete and cause system or authentication issues. |
| AD Forest | Configuration |
Ensure AD Forest TombstoneLifetime has not been modified | If not addressed: :
-Too short (e.g., < 60 days):
-DCs disconnected longer than this can’t replicate -must be forcefully demoted/rebuilt
-Risk of lingering objects or inconsistent replication
-Object recovery window too shortToo long (e.g., > 180 days):-Increases size of garbage-collectable data
-Delays permanent cleanup of deleted objects
-May impact AD performance
— Impact if Addressed (Tombstone Lifetime Set Correctly):
-Reliable AD replication
-Healthy domain controller re-joins within expected time
-Allows for safe recovery of deleted objects (e.g., via AD Recycle Bin)
-Maintains AD performance and integrity |
| AD Forest | HealthCheck |
Ensure no AD Forest Replication Errors | If addressed: Ensures consistent directory data, reliable authentication, and healthy AD operations across all domains and sites.
If not addressed: : Leads to data inconsistency, GPO failures, login/authentication issues, and potential domain controller isolation. |
| AD DNS | Configuration |
Ensure Domain Zone Scavenging is enabled | If addressed:
-Helps maintain clean and accurate DNS zones by removing outdated records.
If not addressed: :
-Stale records may cause resolution failures, IP conflicts, or security issues due to outdated information. |
| AD DNS | Configuration |
Ensure Domain Zones have Secure Updates configured | If addressed:
-Helps maintain clean and accurate DNS zones by removing outdated records.
If not addressed: :
-Stale records may cause resolution failures, IP conflicts, or security issues due to outdated information. |
| AD DNS | Configuration |
Ensure Domain Zone do not have Static Records | If not addressed: (Static Records Present):
-Stale or incorrect records may remain if IPs or hostnames change, causing name resolution issues, login failures, or service disruptions.
If Addressed (Static Records Managed or Removed):
-Ensures accurate, dynamic updates of DNS entries, reducing risk of stale data and improving DNS reliability and automation. |
| AD DNS | Configuration |
Ensure DNS Servers are configured with Forwarders | If addressed:
-Improves DNS resolution by directing requests to known, secure DNS forwarders.
If not addressed: :
-Lack of forwarders may result in failed external name resolutions or slower DNS performance. |
| AD DNS | Configuration |
Ensure DNS Root Hints are configured | If not addressed: (Root Hints Missing or Incorrect):
-DNS servers can- resolve external domains (e.g., google.com) if forwarders are unavailable -leads to internet name resolution failures.
If Addressed (Root Hints Properly Configured):
-DNS can resolve external names independently, improving redundancy and resiliency in name resolution. |
| AD DNS | Configuration |
Ensure DNS Round Robin is Enabled on DNS Servers | If not addressed: (Round Robin Disabled):
-DNS will not distribute client requests across multiple IPs, leading to load imbalance or overuse of a single server.
If Addressed (Round Robin Enabled):
-DNS distributes traffic evenly among multiple hosts (same name, different IPs), enhancing load balancing and availability. |
| AD DNS | HealthCheck |
Ensure DNS Servers have _msdcs zone hosted | If not addressed: (Missing or Misconfigured _msdcs Zone):
-Domain controllers cannot locate each other for replication or services, causing authentication failures, GPO issues, and replication breakdown.
If Addressed (Proper _msdcs Zone Configuration):
-Ensures reliable DC-to-DC communication, proper SRV record registration, and healthy Active Directory replication and functionality. |
| AD DNS | HealthCheck |
Ensure Conditional Forwarders Configured on DNS Servers are working | If not addressed: (Forwarders Misconfigured or Unreachable):
-DNS name resolution for specific external/internal domains fails, causing cross-domain trust issues, application failures, and authentication errors.
If Addressed (Forwarders Working Correctly):
-Ensures fast and accurate resolution of names in partner domains or remote forests, improving efficiency, trust communication, and DNS reliability. |
| AD DNS | Configuration |
Ensure DNS Server Level Scavenging is Configured | If addressed:
-Enables automatic removal of Stale DNS records, improving name resolution accuracy and reducing risks related to ghost devices or IP conflicts.
If not addressed: :
-DNS zones may fill with outdated records, leading to resolution failures, confusion in asset tracking, and potential security loopholes. |
| AD DNS | HealthCheck |
Ensure Domain Controllers have Host Record Registered with correct IP Address | If not addressed: (Incorrect or Missing Host Records):
-Domain controllers become unreachable via DNS, causing replication failures, authentication issues, and Group Policy application failures.
If Addressed (Correct Host Records Present):
-Ensures reliable DNS resolution for domain controllers, supporting healthy AD replication, logons, and GPO processing. |
| Group Policy | Configuration |
Ensure Domain GPO WMI Filters are identified and reviewed | If not addressed: (WMI Filters Unreviewed or Incorrect):
-GPOs may fail to apply to intended targets or apply incorrectly, leading to configuration drift, performance issues, or security gaps.
If Addressed (WMI Filters Reviewed and Valid):
-Ensures targeted and efficient GPO application, avoiding misconfigurations and supporting performance and compliance. |
| Domain Controller | Configuration |
Ensure Undefined Subnets are identified and defined in Active Directory | If not addressed: (Subnets Undefined):
-Clients may be assigned to incorrect AD Sites causing authentication delays, inefficient replication, and poor resource access.
If Addressed (Subnets Properly Defined):
-Enables clients to connect to the closest Domain Controllers, improving logon speed, replication efficiency, and overall network performance. |
| Group Policy | HealthCheck |
Ensure Domain GPOs are Applying | If not addressed: (GPOs Not Applying):
-Results in inconsistent configurations, policy non-compliance, security risks, failed login scripts, or user experience issues.
If Addressed (GPOs Apply Correctly):
-Ensures consistent policy enforcement, system hardening, security baselines, and proper user/system configuration across the domain. |
| Group Policy | Configuration |
Ensure Disabled GPO are identified and reviewed | If not addressed: (Disabled GPOs Left Unreviewed):
-Leads to GPO sprawl, confusion, potential security/configuration gaps, and unnecessary complexity in policy management.
If Addressed (Disabled GPOs Reviewed and Managed):
-Improves GPO hygiene, reduces clutter, and ensures that only valid and relevant policies remain in the environment. |
| AD Forest | Configuration |
Ensure AD Sites have Subnets Defined | If not addressed: (Subnets Not Mapped to Sites):
-Clients may connect to random or distant domain controllers, causing slow logons, replication delays, and poor resource access.
If Addressed (Subnets Properly Defined and Linked):
-Clients are correctly mapped to local AD sites, improving logon speed, replication efficiency, and authentication performance. |
| AD Forest | Configuration |
Ensure AD Site has Location Text Specified | If not addressed: (Location Field Not Set):
-Makes it difficult for admins to identify physical site locations, leading to confusion during troubleshooting, audits, or incident response.
If Addressed (Location Field Set Properly):
-Improves visibility, administration, and supports automated tools and scripts that rely on site metadata for decisions and reporting. |
| Security and Risk | MITREANSSI |
Ensure No Domain Users with Password Never Expire | If addressed:
-Enforces regular password changes, improving password hygiene and reducing risk of password-based attacks.
If not addressed: :
-Passwords may never be changed, increasing likelihood of compromise due to reuse or aging. |
| Configuration-Domain | Configuration |
Ensure No Empty Organizational Units in Domains | If not addressed: (Empty OUs Exist):
-Leads to directory clutter, confusion, and can result in administrative errors, mislinked GPOs, or security blind spots.
If Addressed (No Empty OUs Remain):
-Maintains a clean and organized AD structure, simplifies management, and ensures GPOs and delegation are applied effectively. |
| Configuration-Domain | Configuration |
Ensure No Orphaned ForeignSecurityPrincipals | If not addressed: (Orphaned FSPs Exist):
-These stale objects clutter the directory and may point to deleted or unresolvable external accounts, causing access issues and security confusion.
If Addressed (No Orphaned FSPs):
-AD remains clean, secure, and efficient, with all group memberships referencing valid and resolvable security principals. |
| Domain Controller | HealthCheck |
Ensure Domain Controller Local Disks are configured per Microsoft | If addressed:
-Ensures that domain controllers are operating reliably and meeting diagnostic checks.
If not addressed: :
-failures may go unnoticed, resulting in replication delays, service outages, or authentication issues. |
| Domain Controller | HealthCheck |
Ensure Enough DNS Servers are configured on Domain Controller NIC | If not addressed: (Too Few or Improper DNS Entries):
-Can cause DNS resolution failures, replication issues, or even DCs failing to locate each other, disrupting AD services.
If Addressed (Sufficient DNS Servers Set Properly):
-Ensures robust name resolution, failover capability, and healthy AD replication between Domain Controllers. |
| Domain Controller | HealthCheck |
Ensure Domain Controller Disks have enough Free Space | If not addressed: (Low Disk Space on DCs):
-May cause Active Directory services to fail, SYSVOL replication to break, and prevent critical processes like backups or updates.
If Addressed (Sufficient Disk Space Maintained):
-Ensures stable AD functionality, reliable replication, event logging, and system performance. |
| AD Forest | Configuration |
Ensure each AD Site has Global Catalog Role or Universal Group Caching is enabled | If addressed:
-Enabling Global Catalog Improves user logon performance and Ensures universal group membership is accessible across sites.
If not addressed: :
-Users in those sites may face delayed authentication, group membership issues, and limited directory searches. |
| AD Forest | Configuration |
Ensure AD Site has at least one Domain Controller | If addressed:
-Ensures every site has a DC to handle authentication and replication locally, improving performance and redundancy.
If not addressed: :
-Clients in that site will rely on remote DCs, causing latency, failed logins, or GPO issues. |
| Time Sync | Configuration |
Ensure Root PDC Emulator is configured With Correct Time Source | If not addressed: (Incorrect or No Time Source):
-Can cause time drift across the domain, leading to Kerberos authentication failures, replication issues, and domain-wide instability.
If Addressed (Correct Time Source Set on PDC Emulator):
-Ensures accurate, secure, and synchronized time across all domain members, supporting reliable authentication and replication. |
| Time Sync | Configuration |
Ensure Domain Controllers have correct Time Source Configured | If not addressed: (Incorrect Time Source):
-Causes Kerberos authentication failures, replication issues, and domain instability due to time drift across domain controllers and clients.
If Addressed (Proper Time Sync Configured):
-Maintains secure, synchronized time across the domain, ensuring stable logins, trust relationships, and AD replication. |
| Configuration-DomainController | Configuration |
Ensure Domain Controllers are running with Supported Operating Systems | If not addressed: (Unsupported OS Versions):
-Leads to security vulnerabilities, lack of updates, and incompatibility with newer AD features, risking domain stability and compliance.
If Addressed (All DCs on Supported OS):
-Ensures security patches, feature support, and optimal performance, maintaining a secure and stable Active Directory environment. |
| Configuration-DomainController | Configuration |
Ensure Domain Controllers are in Default OU | If not addressed: (DCs Moved Out of Default OU):
-Can cause Group Policy application issues, management difficulties, and potential security policy misconfigurations.
If Addressed (DCs in Default OU):
-Ensures proper Group Policy application, easier management, and consistent security settings for Domain Controllers. |
| AD Forest | Configuration |
Ensure AD Forest has ISTG Role defined in AD Sites | If not addressed: (No ISTG Defined):
-Leads to inefficient inter-site replication, possible replication delays, and increased network traffic affecting AD performance.
If Addressed (ISTG Properly Assigned):
-Ensures optimal inter-site replication coordination, reducing latency and improving replication reliability across sites. |
| AD Forest | Configuration |
Ensure Manual Replication Connection Objects are identified and removed | If not addressed: (Manual Connections Exist):
-Can cause replication inefficiencies, conflicts, or loops, leading to inconsistent Active Directory data and increased administrative overhead.
If Addressed (Manual Connections Removed):
-Ensures Active Directory replication uses automated topology, promoting efficient, consistent, and reliable replication. |
| Security and Risk | MITREANSSI |
Ensure Highly-Privileged Administrative Groups do not contain more than 20 members | If not addressed: (Too Many Members):
-Increases risk of privilege abuse, insider threats, and difficulty tracking accountability, weakening overall security.
If Addressed (Limited to -20 Members):
-Enhances security posture by enforcing least privilege, improves auditability, and reduces the attack surface. |
| AD Forest | Configuration |
Ensure AD FSMO Placement is as per Microsoft Recommendation | If not addressed: (Improper FSMO Placement):
-Causes performance bottlenecks, replication issues, and potential domain instability, risking service availability and AD integrity.
If Addressed (FSMO Roles Properly Placed):
-Ensures optimal AD performance, reliable replication, and high availability of critical domain services |
| AD Forest | Configuration |
Ensure Domain Naming Master and Schema Master are hosted on same domain controller | If not addressed: (Roles on Different DCs):
-Can cause increased replication traffic and latency, and complicate troubleshooting during forest-wide schema or naming changes.
If Addressed (Both Roles on Same DC):
-Simplifies role management, reduces replication overhead, and aligns with Microsoft best practices for efficient forest operations. |
| Configuration-Domain | Configuration |
Ensure No Empty Security Groups In AD Domains | If not addressed: (Empty Security Groups Exist):
-Leads to confusion, unnecessary clutter, and potential security risks if groups are accidentally assigned permissions without members.
If Addressed (No Empty Groups):
-Improves security hygiene, simplifies administration, and reduces risk of privilege misuse or misconfiguration. |
| Configuration-Domain | Configuration |
Ensure End Of Life Operating Systems and Unsupported Operating Systems are detected | If not addressed: (EOL/Unsupported OS Undetected):
-Exposes the environment to security vulnerabilities, compliance violations, and lack of vendor support, increasing risk of attacks and failures.
If Addressed (EOL/Unsupported OS Detected Promptly):
-Enables timely patching, upgrades, or decommissioning, reducing security risks and ensuring compliance. |
| Domain Controller | HealthCheck |
Domain Controller Services Status Test | If not addressed: (Service Failures Undetected):
-Causes authentication failures, replication issues, and overall AD service disruption, impacting user access and network operations.
If Addressed (Services Monitored and Running):
-Ensures continuous AD availability, reliable authentication, and healthy replication, maintaining network stability and security. |
| Group Policy | Configuration |
Ensure Domain GPOs Block Inheritance is Identified and reviewed | If not addressed: (Block Inheritance Ignored):
-Can cause expected GPOs to not apply, leading to security gaps, inconsistent configurations, and policy conflicts.
If Addressed (Block Inheritance Reviewed):
-Ensures GPOs apply as intended, improves policy consistency, and maintains security and compliance across the domain. |
| Group Policy | Configuration |
Ensure GPO Replication Consistency Across Domain Controllers | |
| Active Directory Reporting | Reporting | Get AD Domain Info and FSMO | f Not Addressed (No Visibility into Domain & FSMO Info): -Leads to mismanagement of critical roles, potential performance issues, or AD failure during outages or upgrades. If Addressed (Domain Info & FSMO Roles Known): -Ensures proper role placement, efficient troubleshooting, and controlled changes in the AD environment. |
| Account Policies | Configuration |
Ensure Domain Account Policies are configured correctly | If not addressed: (Policies Misconfigured or Weak):
-Increases the risk of unauthorized access, brute-force attacks, and non-compliance with security standards (e.g., ISO, NIST, CIS).
If Addressed (Policies Correctly Set):
-Enforces strong authentication controls, improves domain-wide security posture, and ensures regulatory compliance. |
| Account Policies | Configuration |
Ensure FGPP Policies have correct Password parameters configured | If addressed:
-Improves password complexity enforcement for privileged Users through Fine-Grained password Policies.
If not addressed: :
-Weak or short Passwords may still be used by privileged accounts, reducing password strength and security. |
| Account Policies | Configuration |
Ensure FGPP Policies are applying to objects | If addressed:
-Ensures the defined password policies are enforced correctly on targeted Users or groups.
If not addressed: :
-Policy misapplication may lead to inconsistent password enforcement and weaker protection. |
| Configuration-Domain | Configuration |
Ensure Managed Service Accounts are in use | If not addressed: (MSAs Not Used):
-Service accounts may use hardcoded, weak, or expired passwords, leading to security vulnerabilities and management overhead.
If Addressed (MSAs Used):
-Provides automatic password management and simplified administration, improving security and service reliability. |
| Configuration-Domain | Configuration |
Ensure Managed Service Accounts Are Linked | If not addressed: (MSAs Not Linked to Hosts):
-The MSA cannot be used by the intended computer or service, resulting in service failures and authentication errors.
If Addressed (MSAs Linked Correctly):
-Ensures MSAs are authorized to operate securely on specific computers, allowing automated password management and reliable service execution. |
| Domain Controller | Configuration |
Ensure Domain Controllers do not have other Roles Installed | If not addressed: (Other Roles Installed on DCs):
-Increases attack surface, resource contention, and risk of service conflicts or compromise on critical infrastructure.
If Addressed (DCs Have Only AD-Related Roles):
-Ensures stability, security, and performance of Active Directory by isolating its functions from unrelated services. |
| Domain Controller | HealthCheck |
Ensure Domain Controllers have SSL Authentication Enabled | If not addressed: (SSL Not Enabled):
-Sensitive data like user credentials and LDAP queries may be transmitted in clear text, making them vulnerable to interception or tampering.
If Addressed (SSL Enabled):
-Ensures secure, encrypted communication for LDAP and authentication traffic, aligning with security best practices and compliance requirements. |
| Domain Controller | Configuration |
Ensure Domain Controller Event Log Config is configured correctly | If not addressed: (Logs Misconfigured):
-Critical events like logons, policy changes, or replication issues may be missed or overwritten too quickly, impacting incident response and auditing.
If Addressed (Logs Properly Configured):
-Ensures reliable auditing, troubleshooting, and compliance by retaining essential security and system events for sufficient periods. |
| Domain Controller | Configuration |
Ensure Domain Controller Event Log Size is configured correctly | If not addressed: (Log Sizes Too Small):
-Critical security, system, or directory events may be overwritten before review, weakening incident response, auditing, and compliance.
If Addressed (Log Sizes Correctly Set):
-Ensures adequate log retention, supports effective monitoring, and improves security visibility across the domain. |
| Security and Risk | MITREANSSI |
Ensure Privileged Accounts are not sending Too Many Bad Logon Attempts | If addressed:
-Identifies misconfigured services or outdated credentials using privileged accounts, helping secure them and reduce unnecessary log failures.
If not addressed: :
-Frequent failed logons from privileged accounts can increase attack surface, trigger account lockouts, and obscure brute-force attempts |
| Security and Risk | MITREANSSI |
Ensure Domain Computers are not sending Too Many Bad Logon Attempts | If addressed:
-Identifies misconfigurations or outdated credentials on machines causing repeated logon failures.
If not addressed: :
-Could result in unnecessary log noise, account lockouts, or missed detection of brute-force attempts. |
| Security and Risk | MITREANSSI |
Ensure Normal Users are not sending Too Many Bad Logon Attempts | If not addressed: (Too Many Bad Logons Ignored):
-May indicate brute-force attacks, compromised devices, or misconfigured services -potentially leading to account lockouts or breaches.
If Addressed (Bad Logon Attempts Monitored):
-Helps detect early signs of attacks or misconfigurations, enhances account security, and supports proactive incident response. |
| Configuration-Domain | Configuration |
Ensure Domain Users have UPN Specified | If not addressed: (UPN Missing):
-Users may face login issues, especially with modern authentication protocols (e.g., Office 365, Azure AD), causing authentication failures and user frustration.
If Addressed (UPN Properly Set):
-Enables consistent, simplified login experience across services and supports hybrid identity and SSO implementations. |
| AD Forest | Configuration |
Ensure AD Recycle Bin Feature is Enabled | If not addressed: (Recycle Bin Disabled):
-Deleted AD objects are permanently lost or require complex recovery methods, increasing downtime and risk of data loss.
If Addressed (Recycle Bin Enabled):
-Allows easy restoration of deleted objects with all attributes intact, reducing recovery time and minimizing operational impact. |
| Security and Risk | MITREANSSI |
Ensure SMB1 Protocol is Disabled on Domain Controllers | If addressed:
-disabling SMBv1 protects against ransomware and other known SMB-based vulnerabilities.
If not addressed: :
-Leaving SMBv1 enabled exposes the domain controllers to known exploits like EternalBlue. |
| Security and Risk | MITREANSSI |
Ensure SMB1 Client Protocol is Disabled on Domain Controllers | If not addressed: (SMB1 Enabled):
-Legacy SMB1 exposes domain controllers to severe security vulnerabilities, including ransomware and remote code execution attacks.
If Addressed (SMB1 Disabled):
-Reduces attack surface by eliminating outdated protocol risks, improving domain controller security and compliance. |
| Security and Risk | MITREANSSI |
Ensure Pre-Windows 2000 Compatibility Group membership does not include Anonymous and Everyone | If not addressed: (Anonymous/Everyone Included):
-Risks unauthorized access and information disclosure, enabling unauthenticated users to gain elevated privileges.
If Addressed (Anonymous/Everyone Removed):
-Enhances security by limiting group membership to authorized accounts only, reducing exposure to anonymous access attacks. |
| Security and Risk | MITREANSSI |
Ensure Privileged accounts With a Password Never Expires are not configured | If not addressed: (Password Never Expires Set):
-Increases risk of password compromise over time, leading to persistent unauthorized access and potential data breaches.
If Addressed (Passwords Expire Regularly):
-Enforces regular password updates, reducing risk exposure and improving overall account security posture. |
| Security and Risk | MITREANSSI |
Ensure Unprivileged Active Directory Users can not add computer accounts to the domain | If not addressed: (Unprivileged Users Can Add Computers):
-Increases risk of unauthorized devices joining the domain, leading to potential security breaches and lateral movement by attackers.
If Addressed (Only Authorized Users Can Add Computers):
-Strengthens domain security by limiting computer account creation to trusted administrators, reducing attack surface. |
| Security and Risk | MITREANSSI |
Test User Accounts Whose LastPasswordSet Was Never Set | If addressed:
-Identifies accounts that never changed Passwords, helping enforce password policies and hygiene.
If not addressed: :
-accounts may be using default or Stale Passwords, exposing the environment to brute-force or replay attacks. |
| Security and Risk | MITREANSSI |
Ensure User Accounts PWDLastSet has no ZERO Value | If addressed:
-Forces these accounts to change Passwords and Ensures compliance with security policy.
If not addressed: :
-these accounts may allow login without password changes, leading to extended password reuse and risk of compromise. |
| Security and Risk | MITREANSSI |
Ensure Users with Kerberos pre-authentication disabled are identified | If not addressed: (Pre-authentication Disabled Users Unidentified):
-Increases risk of password guessing and brute force attacks, as accounts without pre-authentication are easier to compromise.
If Addressed (Users Identified and Reviewed):
-Enhances security by enabling investigation and remediation of vulnerable accounts, reducing attack vectors. |
| Security and Risk | MITREANSSI |
Ensure Kerberos pre-authentication is Enabled for privileged accounts | If not addressed: (Pre-authentication Disabled for Privileged Accounts):
-Privileged accounts become vulnerable to offline password guessing attacks, increasing risk of privilege escalation and domain compromise.
If Addressed (Pre-authentication Enabled for Privileged Accounts):
-Significantly improves security by requiring pre-authentication, making it harder for attackers to exploit privileged accounts. |
| Security and Risk | MITREANSSI |
Ensure Enabled admin accounts that are inactive are identified | If addressed: disabling or removing unused admin accounts limits entry points for attackers and strengthens security.
If not addressed: : Inactive privileged accounts can be exploited without detection due to Lack of regular use and monitoring. |
| Security and Risk | MITREANSSI |
Ensure User accounts with password not required are identified | If addressed: Enforces password requirements to maintain minimum authentication security standards.
If not addressed: : accounts may authenticate without Passwords, allowing easy unauthorized access. |
| Security and Risk | MITREANSSI |
Ensure User accounts that use DES encryption are Identified | If not addressed: (DES Encryption Users Not Identified): Accounts using weak DES encryption are vulnerable to cryptographic attacks, risking credential theft and unauthorized access.
If Addressed (DES Encryption Users Identified and Remediated): Strengthens security by eliminating use of weak encryption, reducing chances of Kerberos ticket compromise. |
| Security and Risk | MITREANSSI |
Ensure User accounts that store passwords with reversible encryption are identified | If not addressed: (Reversible Encryption Enabled and Not Identified): Increases risk of password disclosure and compromise because reversible encryption is easily reversible, weakening password protection.
If Addressed (Accounts Identified and Reversible Encryption Disabled): Improves security by eliminating weak password storage, protecting user credentials from potential decryption attacks. |
| Security and Risk | MITREANSSI |
Ensure Computer or user accounts with unconstrained delegation are identified | If not addressed: (Unconstrained Delegation Unidentified): Exposes accounts to Kerberos ticket theft and privilege escalation, enabling attackers to impersonate users across services.
If Addressed (Accounts Identified and Delegation Restricted): Reduces risk of lateral movement and enhances overall security by limiting delegation privileges. |
| Security and Risk | MITREANSSI |
Ensure Anonymous access to Active Directory is Disabled | If not addressed: (Anonymous Access Enabled): Allows attackers to enumerate sensitive AD information anonymously, increasing risk of reconnaissance and targeted attacks.
If Addressed (Anonymous Access Disabled): Enhances security by restricting unauthenticated access, protecting AD data from unauthorized disclosure. |
| Security and Risk | MITREANSSI |
Ensure Users with ServicePrincipalName are identified | If addressed: Prevents misuse of user accounts for Kerberoasting attacks by validating and minimizing SPN usage.
f Not Addressed: attackers Could request and crack service tickets tied to user SPNs, leading to credential theft. |
| Security and Risk | MITREANSSI |
Ensure Admin Accounts with ServicePrincipalName are identified | If addressed: Prevents SPN-linked privileged accounts from being targets of Kerberoasting attacks.
If not addressed: : Admins with SPNs can be exploited to extract service tickets and crack high-privilege credentials offline |
| Security and Risk | MITREANSSI |
List All Service Principals Used By Computer Accounts and Identify Them to Ensure they are in use | If not addressed: (SPNs Not Identified or Validated): Unused or stale SPNs can lead to Kerberos authentication issues, security vulnerabilities, and potential service disruptions.
If Addressed (SPNs Listed and Validated): Ensures accurate authentication, reduces attack surface, and improves overall Active Directory security posture. |
| Security and Risk | MITREANSSI |
Ensure Duplicate SPNs are identified and removed | If addressed: Ensures SPNs are only configured where necessary, reducing risk of Kerberoasting via computer accounts.
If not addressed: : Exposed SPNs on computer accounts Could be used to extract service tickets and perform offline attacks. |
| Configuration-DomainController | Configuration |
Ensure Active Directory Web Services (ADWS) to start automatically on All Domain Controllers | If not addressed: (ADWS Not Set to Automatic) AD management tools and services relying on ADWS may fail to connect, causing interruptions in AD administration and automation.
If Addressed (ADWS Set to Start Automatically): Ensures reliable remote management and automation of AD through services like Active Directory Administrative Center and PowerShell cmdlets. |
| Configuration-DomainController | Configuration |
Ensure Strict Replication Consistency is enabled on Domain Controllers | If not addressed: (Strict Replication Consistency Disabled): Increases risk of replication of corrupted or inconsistent data, leading to AD data integrity issues and authentication problems.
If Addressed (Strict Replication Consistency Enabled): Helps maintain data integrity by preventing replication of lingering objects and ensuring consistent AD data across all DCs. |
| Configuration-Domain | Configuration |
Ensure Orphaned Group Policy Containers are identified and removed | If not addressed: (Orphaned GPCs Present): Leads to Group Policy clutter, potential conflicts, and administrative confusion, increasing risk of misapplied or stale policies.
If Addressed (Orphaned GPCs Removed): Improves AD hygiene, reduces replication overhead, and ensures that only valid GPOs affect the environment. |
| Security and Risk | MITREANSSI |
Ensure AllowNT4Crypto setting on all Domain Controllers is disabled | If addressed: Enhances cryptographic security by disabling NT4-style encryption for authentication.
If not addressed: : Weakened cryptography can be exploited in downgrade or man-in-the-middle attacks. |
| Security and Risk | MITREANSSI |
Ensure LAN Manager password hashes are not stored on Domain Controllers | If not addressed: (LM Hashes Stored): LM hashes are weak and easily cracked, increasing risk of credential theft, lateral movement, and domain compromise.
If Addressed (LM Hashes Not Stored): Enhances password security by preventing storage of weak hashes, reducing attack surface for password cracking. |
| Security and Risk | MITREANSSI |
Ensure accounts with adminCount=1 are Identified and Monitored | If not addressed: (adminCount1 Accounts Unmonitored): Privileged accounts may go untracked, increasing risk of unauthorized access, privilege abuse, or insider threats.
If Addressed (adminCount1 Accounts Identified and Monitored): Enables timely detection of changes or suspicious activities on privileged accounts, improving security posture. |
| Security and Risk | MITREANSSI |
Ensure Disabled Privileged User Accounts are not part of Privileged Groups | If addressed: Ensures disabled accounts are Not retaining permissions through group membership, closing potential privilege escalation paths.
If not addressed: : Disabled accounts Could be reactivated and instantly regain high privileges through existing group memberships. |
| Security and Risk | MITREANSSI |
Ensure Privileged User Accounts are Changing Their Passwords Regularly | If addressed: Improves overall password hygiene by enforcing rotation policies, reducing the risk of Old password exposure.
If not addressed: : Long-standing Passwords are more likely to be guessed or already leaked, exposing accounts to compromise. |
| Security and Risk | MITREANSSI |
Ensure SMB Signing is Enabled on Domain Controllers | If not addressed: (SMB Signing Disabled): Vulnerable to man-in-the-middle (MITM) attacks allowing attackers to intercept or manipulate SMB traffic, risking data integrity and security.
If Addressed (SMB Signing Enabled): Provides protection against SMB relay attacks and tampering, ensuring secure and authenticated communication between clients and domain controllers. |
| Security and Risk | MITREANSSI |
Ensure LDAP Signing is Enabled on Domain Controllers | If not addressed: (LDAP Signing Disabled): LDAP traffic is vulnerable to man-in-the-middle (MITM) attacks and credential interception, risking unauthorized access and data breaches.
If Addressed (LDAP Signing Enabled): Ensures integrity and authentication of LDAP communications, preventing tampering and enhancing domain security. |
| Security and Risk | MITREANSSI |
Ensure gMSA Accounts are Identified and Are In Use | If not addressed: (gMSAs Not Used or Tracked): Services may run under standard or overly privileged accounts with hardcoded passwords, increasing the risk of compromise and management overhead.
If Addressed (gMSAs Identified and Used Properly): Enhances security, simplifies password management, and ensures compliance with least privilege principles for services and tasks. |
| Security and Risk | MITREANSSI |
Ensure Sensitive Group Policy Objects have not been changed Since Last 10 Days | If not addressed: (No Monitoring of GPO Changes): Unauthorized or accidental changes to critical GPOs can lead to security misconfigurations, user lockouts, or compromise of domain settings without detection.
If Addressed (Changes Detected and Reviewed): Enables early detection of unauthorized modifications, maintaining configuration integrity and compliance with security policies. |
| Security and Risk | MITREANSSI |
Ensure Kerberos krbtgt Account Password Is Changed Within 180 Days | If not addressed: (krbtgt Password Not Changed): Attackers with stolen Kerberos tickets (e.g., Golden Tickets) can persist undetected indefinitely, risking full domain compromise.
If Addressed (krbtgt Password Changed Within 180 Days): Ensures Kerberos ticket integrity, reduces the risk of ticket forgery, and limits the lifespan of previously compromised tickets. |
| Security and Risk | MITREANSSI |
Ensure RC4 Encryption is Disabled on Domain Controllers | If addressed: disabling RC4 Helps enforce the use of stronger cryptographic algorithms during Kerberos authentication.
If not addressed: : RC4 is outdated and vulnerable to cryptanalysis, risking Kerberos ticket integrity. |
| Security and Risk | MITREANSSI |
Ensure Orphaned Admins from AdminSDHolder are Identified and Removed | If not addressed: (Orphaned Admins Retain AdminSDHolder Protections): Former privileged accounts may retain elevated permissions and inherit protection, posing a major security risk due to unmanaged access.
If Addressed (Orphaned Admins Are Removed): Ensures only authorized privileged accounts receive elevated protection, maintaining least privilege and reducing attack surface. |
| Security and Risk | MITREANSSI |
Ensure Dangerous Permissions are Detected On AdminSDHolder Object | If addressed: It Ensures only trusted accounts (such as domain Admins) have permissions on AdminSDHolder, reducing the risk of privilege escalation. This Enhances the security posture by protecting high-privilege accounts from unauthorized changes.
If not addressed: : Non-admin accounts with write access to AdminSDHolder may gain elevated privileges or modify protected accounts, leading to potential domain compromise or persistence by attackers |
| Security and Risk | MITREANSSI |
Ensure AdminSDHolder Object was not modified in Last 30 days | If not addressed: (Recent Unauthorized Modifications Go Undetected): Attackers or misconfigurations can silently modify AdminSDHolder ACLs, allowing persistent privilege escalation on all protected accounts.
If Addressed (Modifications Detected Promptly): Ensures security integrity of privileged accounts, allows quick response to unauthorized changes, and supports audit/compliance efforts. |
| Security and Risk | MITREANSSI |
Ensure Changes to Privileged Groups are Identified and Monitored | If addressed: Helps detect unauthorized additions/removals from sensitive groups, improving audit and security visibility.
If not addressed: : unauthorized changes may go unnoticed, leading to privilege escalation or silent admin-level access. |
| Security and Risk | MITREANSSI |
Ensure Servers Are Changing Their Passwords Within 45 Days | If addressed: Forces servers to renew machine account Passwords, maintaining secure trust with the domain.
If not addressed: : servers using Old secrets Could be vulnerable to replay attacks, domain trust failures, or unauthorized access. |
| Security and Risk | MITREANSSI |
Ensure Servers Have Authenticated Within 90 Days | If addressed: Validates server trust relationships and Ensures all domain-joined systems authenticate regularly.
If not addressed: : Unauthenticated or disconnected servers may be unmanaged, misconfigured, or rogue, posing security risks. |
| Security and Risk | MITREANSSI |
Ensure Domain Controllers Have Authenticated Within 45 Days | If not addressed: (Inactive Domain Controllers Exist): Stale or decommissioned DCs can cause replication failures, authentication issues, and security vulnerabilities if reactivated by attackers.
If Addressed (All DCs Are Active and Accounted For): Ensures a healthy, synchronized AD environment, reduces attack surface, and avoids service disruption due to orphaned or unreachable DCs. |
| Security and Risk | MITREANSSI |
Ensure Domain Controllers Have renewed their secrets within 45 days | If not addressed: (Secrets Not Renewed in 45 Days): Domain controllers may use outdated secure channel passwords, leading to trust issues, replication failures, or vulnerability to replay attacks.
If Addressed (Secrets Renewed Within 45 Days): Maintains secure communication between DCs and the domain, ensuring trust, replication health, and security against credential-based attacks. |
| Security and Risk | MITREANSSI |
Ensure User Objects have not been Modified With PrimaryGroupID | If addressed: Restores standard group memberships and Prevents misuse of PrimaryGroupID for privilege escalation or hiding user memberships.
If not addressed: : Users may be improperly associated with privileged or abnormal groups, bypassing standard security filtering or gaining unintended access. |
| Security and Risk | MITREANSSI |
Ensure Computer Objects have not been Modified With PrimaryGroupID | If addressed: Ensures computer objects are properly classified and follow security boundaries defined by default group memberships.
If not addressed: : Cisconfigured PrimaryGroupID Could result in access control inconsistencies or group Policy application failures. |
| Security and Risk | MITREANSSI |
Ensure Domain Controller Objects have not been Modified With PrimaryGroupID | If not addressed: (PrimaryGroupID Is Maliciously Modified): Attackers can bypass group-based access control by assigning privileged groups via PrimaryGroupID, leading to unauthorized privilege escalation.
If Addressed (PrimaryGroupID Is Intact and Unaltered): Ensures accurate group membership enforcement for domain controllers and prevents abuse of hidden privilege escalation paths. |
| Security and Risk | MITREANSSI |
Ensure Active Directory Forest is running with Updated Schema | If not addressed: (Outdated Schema): Prevents new features, OS versions, and applications (like Exchange or hybrid Azure AD) from functioning properly, and may introduce security or compatibility issues.
If Addressed (Schema Is Updated): Enables full use of new Active Directory features, improves compatibility and security, and supports modern infrastructure (e.g., Windows Server, Azure AD). |
| Security and Risk | MITREANSSI |
Ensure DNSAdmin Groups do not include Member Accounts | If addressed: Reduces the attack surface by limiting DNSAdmin privileges, which can be exploited to gain system-level access.
If not addressed: : Members of the DNSAdmins group can be used for privilege escalation, especially on servers where DNS is installed. |
| Security and Risk | MITREANSSI |
Ensure Allowed RODC Password Replication Group is empty | If not addressed: (Group Contains Accounts): Sensitive passwords may be cached on Read-Only Domain Controllers (RODCs), increasing risk if an RODC is compromised.
If Addressed (Group is Empty): No passwords are cached on RODCs, reducing attack surface and protecting credentials from exposure on less secure servers. |
| Security and Risk | MITREANSSI |
Ensure Denied RODC Password Replication Group Includes Privileged Groups | If addressed: Ensures privileged credentials are never cached on RODCs, reducing exposure If the RODC is compromised.
If not addressed: : Privileged account credentials Could be replicated and cached on RODCs, making them vulnerable to offline attacks. |
| Security and Risk | MITREANSSI |
Ensure RODC Domain Controllers have Privileged Groups in msDS-NeverRevealGroupattribute Attribute | If not addressed: : Privileged group memberships (e.g., Domain Admins) may be exposed on RODCs, risking credential theft if the RODC is compromised.
If addressed: Privileged groups are hidden from RODCs, preventing password replication of high-privilege accounts and enhancing security. |
| Security and Risk | MITREANSSI |
Ensure Protected Users Group is in use | If addressed: Adding admin accounts to the protected Users group Reduces risks of credential theft, replay attacks, and disables legacy protocols like NTLM, DES, and unconstrained delegation.
If not addressed: : Privileged credentials remain Exposed to legacy authentication methods, making them more vulnerable to credential theft and misuse. |
| Security and Risk | MITREANSSI |
Ensure All Privileged Groups are part of Protected Users Group | If addressed: Adding privileged groups to the protected Users group disables legacy authentication and Enhances credential protection.
If not addressed: : privileged accounts remain Exposed to weaker protocols (NTLM, DES) and ticket forwarding. |
| Security and Risk | MITREANSSI |
Ensure Default Administrator Account is Protected | If not addressed: : The default Administrator account is a prime target for attackers; if unprotected, it can lead to unauthorized access and full domain compromise.
If addressed: Protecting this account reduces risk of brute force attacks, unauthorized use, and strengthens overall domain security. |
| Security and Risk | MITREANSSI |
Ensure Default Administrator account is disabled | If addressed:
disabling the default admin account Reduces exposure to well-known credentials and brute-force attacks.
If not addressed: :
attackers may target the default Administrator account as It exists in every domain and cannot be renamed without disabling it. |
| Security and Risk | MITREANSSI |
Ensure Default Administrator account is renamed | If addressed:
Renaming the default admin account adds a layer of obscurity and makes brute-force attacks more difficult.
If not addressed: :
attackers can directly target the default -Administrator- username, making It easier to attempt password guessing or exploit attempts. |
| Security and Risk | MITREANSSI |
Ensure Default Administrator account is not used in Last 10 days | If addressed:
Usage of the built-in admin can be restricted or monitored more closely to encourage use of named accounts for accountability.
If not addressed: :
Unmonitored use may hide malicious activity, as the account lacks personal attribution. |
| Security and Risk | MITREANSSI |
Ensure Default Administrator account password was changed within 90 days | If addressed:
Enforces password rotation for the most powerful account in the domain, improving security hygiene.
If not addressed: :
Stale Passwords increase the risk of compromise through replay, brute-force, or previously leaked credentials. |
| Security and Risk | MITREANSSI |
Ensure Guest Account is Disabled in All Domains | If not addressed: :
Enabled Guest accounts can be exploited by attackers to gain unauthorized, anonymous access to domain resources, increasing security risks.
If addressed:
Disabling the Guest account helps prevent unauthorized access and strengthens domain security posture. |
| Security and Risk | MITREANSSI |
Ensure Guest Account is Renamed in All Domains | If addressed:
Renaming the Guest account Helps prevent automated attacks that target default account names.
If not addressed: :
Guest accounts may be exploited for unauthorized access, especially If enabled and Not monitored. |
| Security and Risk | MITREANSSI |
Ensure Schema Admins Groups is Empty | If addressed:
Reduces risk of unauthorized schema changes by limiting membership to This powerful group.
If not addressed: :
Active membership may be misused to modify AD schema, potentially leading to directory corruption or privilege abuse. |
| Configuration-DomainController | Configuration |
Ensure DHCP Server Service is disabled on Domain Controllers | If not addressed: :
Running DHCP Server service on Domain Controllers can increase the attack surface, cause service conflicts, and lead to security and performance issues.
If addressed:
Disabling DHCP on Domain Controllers reduces security risks and ensures clear separation of roles and responsibilities. |
| Configuration-DomainController | Configuration |
Ensure Domain Controller Computer Accounts are owned by Privileged Accounts | If not addressed: :
Unowned or improperly owned Domain Controller computer accounts can be modified by unauthorized users, risking domain security and control.
If addressed:
Assigning ownership to privileged accounts ensures tight control, reducing risks of unauthorized changes and potential security breaches. |
| Configuration-DomainController | Configuration |
Ensure Domain Controllers are not using NTFRS for AD Replication | If not addressed: :
Continuing to use NTFRS (NT File Replication Service) risks replication failures, data inconsistencies, and unsupported legacy systems affecting AD reliability.
If addressed:
Migrating to DFS-R (Distributed File System Replication) ensures improved replication efficiency, reliability, and support for SYSVOL replication. |
| Security and Risk | MITREANSSI |
Ensure Privileged Accounts Password Expires | If addressed:
Forces regular password changes for admin accounts, reducing the risk of password-based attacks.
If not addressed: :
admin credentials remain unchanged for extended periods, increasing the chance of exposure and compromise. |
| Security and Risk | MITREANSSI |
Ensure Computer Objects are Managed by Privileged Accounts | If addressed:
Ensures administrative control and auditing over critical computer objects in the domain.
If not addressed: :
Non-admin Users may retain ownership over sensitive computer objects, potentially modifying settings or permissions without oversight. |
| Security and Risk | MITREANSSI |
Ensure Organizational Units are Managed by Privileged Accounts | If addressed: Ensuring only privileged accounts manage Organizational Units minimizes the risk of unauthorized changes, strengthens access control, and enhances overall security posture by limiting administrative privileges to trusted personnel.
If not addressed: : Unauthorized or improperly privileged accounts managing OUs can lead to misconfigurations, security breaches, privilege escalation, and potential compromise of critical directory services. |
| Security and Risk | MITREANSSI |
Constrained authentication delegation to a domain controller service | If addressed:
Removes unnecessary constrained delegation permissions, reducing the chance of attackers impersonating Users to access domain controllers.
If not addressed: :
Improper delegation Could allow lateral movement or unauthorized access to sensitive services by compromising a delegated account or system. |
| Security and Risk | MITREANSSI |
Resource-based constrained delegation on domain controllers | If addressed: Properly configuring resource-based constrained delegation on domain controllers prevents unauthorized delegation of credentials, reducing the risk of credential theft and lateral movement attacks within the network.
If not addressed: : Misconfigured or unchecked delegation can allow attackers to impersonate privileged accounts on domain controllers, leading to full domain compromise and severe security breaches. |
| Security and Risk | MITREANSSI |
Ensure Computer Accounts are not part of Privileged Groups | If addressed: Ensuring computer accounts are excluded from privileged groups reduces the attack surface by preventing machines from having elevated permissions, thereby limiting the scope of compromise and privilege escalation.
If not addressed: : Allowing computer accounts in privileged groups can enable attackers who compromise a machine to gain domain-wide administrative privileges, leading to potential full domain takeover. |
| Security and Risk | MITREANSSI |
Ensure All Operators Groups are Empty in Domain | If addressed: Keeping all Operators groups empty eliminates unnecessary elevated privileges, reducing the risk of privilege abuse and insider threats, thereby strengthening overall domain security.
If not addressed: : Non-empty Operators groups can provide excessive administrative access to users or accounts, increasing the attack surface and the potential for unauthorized changes or domain compromise. |
| Security and Risk | MITREANSSI |
Review Recently created Privileged Accounts in Domains in Last 10 Days | If addressed: Timely review of newly created privileged accounts helps detect and prevent unauthorized privilege escalation or malicious account creation, reducing the risk of insider threats and domain compromise.
If not addressed: : Failure to review new privileged accounts can allow attackers or malicious insiders to maintain unauthorized elevated access, increasing the chance of persistent compromise and damaging security breaches. |
| Security and Risk | MITREANSSI |
Ensure Print Spooler Service is disabled on Domain Controllers | If addressed:
disabling the Print Spooler service on domain controllers Reduces exposure to PrintNightmare and similar remote code execution vulnerabilities.
If not addressed: :
An attacker Could exploit Spooler-related vulnerabilities to escalate privileges or execute code remotely on domain controllers. |
| Security and Risk | MITREANSSI |
Ensure Privileged Users are using Strong Password Policy | If addressed: Enforcing strong password policies for privileged users significantly reduces the risk of account compromise through brute force, guessing, or credential theft, thereby protecting critical systems and data.
If not addressed: : Weak passwords on privileged accounts increase vulnerability to attacks, potentially leading to unauthorized access, privilege escalation, and full domain or system compromise. |
| Security and Risk | MITREANSSI |
Ensure TLS 1.1 protocol is disabled on Domain Controllers | If addressed:
Disabling TLS 1.1 ensures domain controllers use modern, secure encryption protocols, reducing vulnerabilities to outdated cipher suite attacks.
If not addressed: :
TLS 1.1 remains an exploitable protocol, increasing risk of downgrade attacks or exposure to weak encryption exploits. |
| Security and Risk | MITREANSSI |
Ensure NTLMv1 Authentication is disabled on Domain Controllers | If addressed:
Reduces reliance on NTLM, An outdated and less secure protocol, helping prevent NTLM relay attacks and credential theft.
If not addressed: :
Continued NTLM Usage increases risk of relay attacks, pass-the-hash, and other legacy protocol vulnerabilities. |
| Security and Risk | MITREANSSI |
Ensure No Groups are Excluded by AdminSDHolder and SDProp | If addressed: Ensuring all privileged groups are protected by AdminSDHolder and SDProp maintains consistent and secure permissions, preventing unauthorized changes and protecting sensitive accounts from privilege escalation.
If not addressed: : Groups excluded from AdminSDHolder and SDProp protections may have inconsistent permissions, increasing the risk of privilege abuse, unauthorized access, and potential domain compromise. |
| Security and Risk | MITREANSSI |
Ensure User Objects sIDHistory does not contain Privileged Accounts | If addressed: Ensuring that sIDHistory attributes on user objects do not contain privileged account SIDs prevents unauthorized privilege inheritance, reducing the risk of privilege escalation and unauthorized access.
If not addressed: : If sIDHistory contains privileged SIDs, users may retain unintended elevated privileges, enabling attackers to exploit these for lateral movement or domain compromise. |
| Security and Risk | MITREANSSI |
Ensure Computer Objects sIDHistory does not contain Privileged Accounts | If addressed: Ensuring that computer objects-sIDHistory does not include privileged account SIDs prevents unauthorized elevation of machine permissions, thereby reducing the risk of compromised systems gaining excessive access.
If not addressed: : If privileged SIDs are present in computer objects-sIDHistory, attackers could exploit these to escalate privileges or move laterally, potentially compromising critical systems and the entire domain. |
| Security and Risk | MITREANSSI |
Ensure Microsoft LAPS is deployed in AD Forest | If addressed: Deploying Microsoft LAPS ensures that local administrator passwords on domain-joined computers are unique, randomly generated, and securely stored, greatly reducing the risk of lateral movement and credential theft.
If not addressed: : Without LAPS, local administrator accounts often share common or static passwords, making it easier for attackers to move laterally and escalate privileges across multiple systems in the domain. |
| Security and Risk | MITREANSSI |
Ensure Krbtgt account do not have Resource-Based Constrained Delegation | If addressed: Ensuring the Krbtgt account has no Resource-Based Constrained Delegation prevents attackers from exploiting this highly sensitive account to forge Kerberos tickets, thereby protecting the integrity of domain authentication.
If not addressed: : If the Krbtgt account is granted RBCD rights, attackers could abuse it to perform Golden Ticket attacks or escalate privileges, leading to full domain compromise. |
| Security and Risk | MITREANSSI |
Ensure Members in Privileged Groups have AdminCount=1 Set | If addressed: Ensuring adminCount1 is set on members of privileged groups enables Active Directory- AdminSDHolder process to protect these accounts with consistent, hardened permissions, reducing risk of unauthorized privilege escalation.
If not addressed: : If adminCount1 is not set on privileged group members, those accounts may not receive necessary security descriptor protections, increasing the likelihood of permission tampering and compromise. |
| Security and Risk | MITREANSSI |
Ensure ForeignSecurityPrincipal in Privileged Groups are identified | If addressed: Identifying ForeignSecurityPrincipal objects in privileged groups helps detect external or cross-domain accounts that have been granted elevated access, improving security visibility and reducing risk of unauthorized privilege use.
If not addressed: : Undetected ForeignSecurityPrincipal objects in privileged groups can allow unmonitored external accounts to have administrative privileges, increasing the risk of lateral movement and domain compromise. |
| Azure-Infra | MITREANSSI |
Ensure On-Prem AD Users are not Privileged Users in Azure Entra ID | If addressed: Ensuring on-prem AD users do not have unintended privileged roles in Azure Entra ID prevents unauthorized elevation of privileges across hybrid environments, strengthening security posture and reducing attack surface.
If not addressed: : If on-prem AD users have excessive privileged roles in Azure Entra ID, attackers who compromise those accounts can gain broad access to cloud resources, potentially leading to data breaches or service disruptions. |
| Azure-Infra | MITREANSSI |
Ensure Azure Administrative Units are used | If addressed: Using Azure Administrative Units enables granular delegation of administrative permissions, improving security by limiting admin scope and reducing the risk of privilege misuse.
If not addressed: : Without Administrative Units, administrators may have overly broad permissions, increasing the risk of accidental or malicious changes affecting the entire tenant. |
| Azure-Infra | MITREANSSI |
Ensure Azure Guests cannot invite other Guests | If addressed: Preventing guest users from inviting other guests helps maintain tighter control over external access, reducing the risk of unauthorized or malicious external users entering the tenant.
If not addressed: : Allowing guests to invite others can lead to uncontrolled guest proliferation, increasing attack surface and potential data exposure to untrusted users |
| Azure-Infra | MITREANSSI |
Ensure privileged accounts have MFA Configured | If addressed: Enforcing MFA on privileged accounts significantly strengthens security by adding an additional authentication factor, reducing the risk of account compromise even if passwords are stolen.
If not addressed: : Without MFA, privileged accounts remain vulnerable to phishing, credential theft, and brute force attacks, potentially leading to unauthorized access and full domain or system compromise. |
| Azure-Infra | MITREANSSI |
Ensure non-Admins cannot register custom applications | If addressed: Restricting custom application registration to admins prevents unauthorized or malicious apps from being registered, reducing the risk of data exfiltration, privilege escalation, or insider threats.
If not addressed: : Allowing non-admins to register applications increases the attack surface, enabling potential abuse such as rogue app creation, excessive permissions requests, or unauthorized access to sensitive resources. |
| Azure-Infra | MITREANSSI |
Ensure no Guest Accounts in Azure Privileged groups | If addressed: Removing guest accounts from Azure privileged groups reduces the risk of external attackers gaining elevated access, thereby strengthening tenant security and protecting sensitive resources.
If not addressed: : Allowing guest accounts in privileged groups increases the risk of privilege misuse or compromise by external users, potentially leading to data breaches or unauthorized control over critical systems. |
| Azure-Infra | MITREANSSI |
Ensure Security Defaults is enabled | If addressed: Enabling Security Defaults provides a baseline level of protection by enforcing MFA for all users, blocking legacy authentication, and reducing risks like compromised credentials and identity attacks.
If not addressed: : Without Security Defaults, the tenant is more vulnerable to common attacks such as password spray, phishing, and unauthorized access due to weaker default security settings. |
| Azure-Infra | MITREANSSI |
Ensure Normal Azure Users do not have Permissions to provide unrestricted user Consent | If addressed: Restricting user consent to applications prevents users from inadvertently granting excessive permissions to malicious or poorly designed apps, protecting sensitive data and resources.
If not addressed: : Allowing normal users to provide unrestricted consent can lead to over-permissioned apps, increasing the risk of data leakage, unauthorized access, and security breaches. |
| Azure-Infra | MITREANSSI |
Ensure Conditional Access Policy with signin user-risk location as Factor | If addressed: Using sign-in risk and location in Conditional Access policies strengthens security by dynamically blocking or restricting risky or unusual logins (e.g., from unfamiliar countries or IPs), preventing potential compromise.
If not addressed: : Without these controls, users may authenticate from high-risk or malicious locations without restriction, increasing exposure to account compromise and data breaches. |
| Azure-Infra | MITREANSSI |
Ensure no Guest accounts that are inactive for more than 45 days | If addressed: Regularly removing inactive guest accounts reduces the risk of dormant identities being exploited by attackers and improves overall identity hygiene in your Azure AD environment.
If not addressed: : Inactive guest accounts can remain unnoticed for long periods, providing potential backdoors for attackers or former partners to gain unauthorized access. |
| Azure-Infra | MITREANSSI |
Conditional Access policy with Continuous Access Evaluation disabled | If addressed: Enabling Continuous Access Evaluation (CAE) allows real-time enforcement of Conditional Access policies when critical events occur (e.g., token revocation, user disablement, or location change), significantly reducing exposure time during attacks.
If not addressed: : Without CAE, policy enforcement relies on token expiration (usually 1 hour), meaning revoked access or risk signals may take effect too late, increasing vulnerability to session hijacking and unauthorized access. |
| Azure-Infra | MITREANSSI |
AAD Connect sync account password reset | If addressed: Resetting the AAD Connect sync account password (properly updated in both AD and AAD Connect) ensures continued secure directory synchronization without service disruption.
If not addressed: : If the password is reset but not updated in the AAD Connect configuration, directory sync will fail, potentially halting user provisioning, password sync, and group updates between on-premises AD and Azure AD. |
| Azure-Infra | MITREANSSI |
Ensure Guest users are restricted | If addressed: Restricting guest users helps enforce least privilege access, reducing the risk of data leakage or unauthorized activity by external collaborators.
If not addressed: : Unrestricted guest users can access sensitive information or lateral move within the tenant, increasing the risk of insider threats and data breaches. |
| Azure-Infra | MITREANSSI |
Ensure user are configured with MFA | If addressed: Enabling MFA significantly strengthens account security by requiring an additional authentication factor beyond passwords, greatly reducing the risk of unauthorized access due to credential theft or phishing.
If not addressed: : Without MFA, user accounts are vulnerable to common attacks like password spray, phishing, and brute force, potentially leading to data breaches and system compromise. |
| Azure-Infra | MITREANSSI |
Conditional Access Policy that disables admin token persistence | If addressed: Disabling token persistence for admins reduces the risk of session hijacking by ensuring that privileged sessions do not remain active across browser restarts or long idle periods.
If not addressed: : Persistent tokens allow admin sessions to stay active longer than necessary, increasing exposure if the session is hijacked or the device is compromised. |
| Azure-Infra | MITREANSSI |
Conditional Access Policy that does not require a password change from high risk users | If addressed: Requiring a password change for high-risk users helps mitigate account compromise by resetting credentials that may have been exposed or misused.
If not addressed: : Without forcing password changes for high-risk users, compromised accounts can continue to be exploited, increasing the likelihood of lateral movement, data theft, or privilege escalation. |
| Azure-Infra | MITREANSSI |
Conditional Access Policy that does not require MFA when sign-in risk has been identified | If addressed: Enforcing MFA when sign-in risk is detected helps block or challenge potentially malicious login attempts, greatly reducing the risk of unauthorized access.
If not addressed: : Allowing risky sign-ins without requiring MFA exposes accounts to compromise, especially in scenarios like credential theft, unfamiliar sign-ins, or impossible travel. |
| Azure-Infra | MITREANSSI |
Ensure Guest invites not accepted in last 30 days are identified | If addressed: Identifying and cleaning up unaccepted guest invitations improves Azure AD hygiene, reduces unnecessary exposure, and ensures only active, engaged external users retain access paths.
If not addressed: : Unaccepted guest invites remain open indefinitely, increasing the risk of delayed unauthorized access if the invitation is accepted later under unexpected or malicious circumstances. |
| Azure-Infra | MITREANSSI |
Ensure Synced AAD Users not privileged Users in Azure | If addressed: Ensuring synced users from on-premises AD do not have unintended privileged roles in Azure AD reduces the risk of privilege escalation and limits attack surfaces to only authorized personnel.
If not addressed: : Synced users with inappropriate privileged roles can lead to unauthorized access, compromising critical resources and increasing the risk of data breaches or service disruption. |
| Azure-Infra | MITREANSSI |
Ensure No Private IP Addresses in Conditional Access policies | If addressed: Excluding private IP addresses from Conditional Access policies prevents misconfigurations that can block legitimate user access or create security gaps by improperly trusting internal or VPN traffic.
If not addressed: : Including private IP ranges can cause unintended access denials or allow attackers to exploit trusted network conditions, weakening policy effectiveness. |
| Azure-Infra | MITREANSSI |
Ensure Number Matching enabled in MFA | If addressed: Enabling Number Matching in MFA enhances security by requiring users to confirm a number displayed on their sign-in screen during authentication, preventing unauthorized approvals from blind or accidental MFA prompts.
If not addressed: : Without Number Matching, users may inadvertently approve fraudulent MFA prompts, increasing the risk of account compromise through MFA fatigue or phishing attacks. |
| Azure-Infra | MITREANSSI |
Ensure AD privileged users are not synced to AAD | If addressed: Preventing AD privileged users from syncing to Azure AD reduces the risk of excessive privilege exposure in the cloud, helping enforce stricter access control boundaries between on-prem and cloud environments.
If not addressed: : Syncing privileged AD users to Azure AD can lead to unintended elevated privileges in cloud services, increasing the attack surface and risk of compromise across hybrid environments. |
| Azure-Infra | MITREANSSI |
Ensure no more than 5 Global Administrators | If addressed: Limiting Global Administrators to five or fewer reduces the attack surface by minimizing the number of highly privileged accounts, enhancing security and making it easier to manage and monitor critical admin access.
If not addressed: : Having too many Global Administrators increases the risk of accidental or malicious misuse of elevated privileges, complicates auditing, and raises the potential for security breaches. |
| Azure-Infra | MITREANSSI |
Ensure SSO computer account with latest password | If addressed: Ensuring SSO computer accounts have updated passwords maintains secure authentication between devices and services, preventing authentication failures and potential security breaches.
If not addressed: : Outdated or stale computer account passwords can cause SSO failures, service disruptions, and may allow attackers to exploit compromised or unsynchronized credentials. |
| Azure-Infra | MITREANSSI |
Ensure RBCD is not applied to AZUREADSSOACC account | If addressed: Preventing RBCD on the AZUREADSSOACC account mitigates risks of privilege escalation and lateral movement, protecting the sensitive Azure AD Connect SSO service account from being exploited.
If not addressed: : If RBCD is improperly enabled on AZUREADSSOACC, attackers could impersonate the account or services it controls, leading to potential domain compromise and unauthorized access. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Prevent enabling lock screen camera is enabled on Domain Controllers | If addressed: Enabling this policy prevents the use of cameras on the lock screen of Domain Controllers, reducing the risk of unauthorized surveillance or data leakage through image capture.
If not addressed: : Allowing the lock screen camera on Domain Controllers may expose sensitive environments to privacy breaches, insider threats, or accidental data leaks via unauthorized photography. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Prevent enabling lock screen slide show is enabled on Domain Controllers | If addressed: Enabling this policy disables the lock screen slideshow on Domain Controllers, reducing the risk of information leakage or distractions caused by unauthorized or inappropriate images.
If not addressed: : Allowing the lock screen slideshow can expose sensitive information through displayed images or cause unnecessary resource usage and potential security gaps on critical systems. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Do not allow passwords to be saved is enabled on Domain Controllers | If addressed: Enabling this policy on Domain Controllers prevents passwords from being cached or saved, reducing the risk of credential theft through stored passwords and enhancing overall security.
If not addressed: : Allowing passwords to be saved on Domain Controllers increases the risk of attackers extracting cached credentials, leading to potential privilege escalation and domain compromise. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Always prompt for password upon connection is enabled on Domain Controllers | If addressed: Enabling this policy ensures that users must enter their password every time they connect to Domain Controllers, reducing the risk of unauthorized access through cached or saved credentials.
If not addressed: : Without this prompt, passwords may be cached or reused automatically, increasing the risk of credential theft or unauthorized access to critical systems. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Require secure RPC communication is enabled on Domain Controllers | If addressed: Enabling secure RPC communication on Domain Controllers ensures that Remote Procedure Calls are encrypted and authenticated, protecting sensitive data and preventing man-in-the-middle attacks.
If not addressed: : Without secure RPC, communications to Domain Controllers can be intercepted or tampered with, exposing the network to eavesdropping, credential theft, and potential compromise |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Set client connection encryption level is enabled on Domain Controllers | If addressed: Enabling and configuring the client connection encryption level on Domain Controllers ensures all Remote Desktop Protocol (RDP) sessions are encrypted, protecting data in transit from interception or tampering.
If not addressed: : Without enforced encryption, RDP sessions to Domain Controllers may transmit data in clear text, exposing sensitive credentials and information to attackers via network sniffing. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Windows Defender SmartScreen is enabled on Domain Controllers | If addressed: Enabling Windows Defender SmartScreen on Domain Controllers helps protect against phishing and malware by warning users about potentially malicious websites and files, enhancing overall security posture.
If not addressed: : Without SmartScreen enabled, domain controllers are more vulnerable to users inadvertently running malicious files or visiting harmful websites, increasing the risk of compromise. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure AutoPlay is Turned off on Domain Controllers | If addressed: Disabling AutoPlay on Domain Controllers prevents automatic execution of potentially malicious software from removable media, reducing the risk of malware infection and unauthorized access.
If not addressed: : Leaving AutoPlay enabled can allow malware or unauthorized programs to run automatically when removable devices are connected, posing a serious security risk to critical domain controller systems. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure default behavior for AutoRun is set on Domain Controllers | If addressed: Setting the default behavior for AutoRun to disabled on Domain Controllers prevents automatic execution of scripts or programs from removable media, significantly reducing the risk of malware infections and unauthorized code execution.
If not addressed: : If AutoRun is enabled or misconfigured, attackers could exploit removable media to automatically run malicious code on Domain Controllers, leading to potential system compromise and domain-wide security breaches. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure UNC Paths are Hardened on Domain Controllers | If addressed: Hardening UNC (Universal Naming Convention) paths on Domain Controllers strengthens network file share security by enforcing strict access controls and reducing exposure to man-in-the-middle and relay attacks.
If not addressed: : Unsecured UNC paths can be exploited by attackers to intercept, modify, or redirect network traffic, potentially leading to credential theft, lateral movement, and domain compromise. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure insecure guest logons are disabled on Domain Controllers | If addressed: Disabling insecure guest logons on Domain Controllers prevents anonymous or unauthenticated access to network resources, reducing the risk of unauthorized access and potential lateral movement within the network.
If not addressed: : Allowing insecure guest logons exposes Domain Controllers to unauthorized users who can exploit this access for reconnaissance, privilege escalation, or launching attacks on the domain. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit- Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings is enabled | If addressed: Enabling this setting ensures that detailed audit policy subcategories take precedence over broader category settings, providing granular and accurate auditing essential for effective security monitoring and compliance.
If not addressed: : Without this enabled, audit policies might be inconsistent or overly broad, leading to gaps in security logging, missed critical events, and challenges in forensic investigations. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Domain controller- LDAP server signing requirements is enabled | If addressed: Enabling LDAP server signing on Domain Controllers enforces signing of LDAP traffic, protecting against man-in-the-middle attacks and ensuring the integrity and authenticity of LDAP communications.
If not addressed: : Without LDAP signing enforced, LDAP traffic can be intercepted or tampered with by attackers, leading to potential credential theft, unauthorized directory access, and domain compromise. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Domain controller- Refuse machine account password changes is enabled | If addressed: Enabling this setting prevents domain controllers from automatically changing their machine account passwords, ensuring stability and avoiding potential authentication issues in the domain.
If not addressed: : If this setting is disabled, domain controllers might attempt to change their machine account passwords, which can lead to replication errors, trust relationship failures, and authentication problems within the domain. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Domain member- Digitally encrypt or sign secure channel data (always) is enabled | If addressed: Enabling this setting ensures that all secure channel communications between domain members and domain controllers are encrypted or signed, protecting data integrity and confidentiality during authentication and replication.
If not addressed: : Without this enforced, secure channel data can be vulnerable to interception or tampering by attackers, risking credential theft, man-in-the-middle attacks, and unauthorized access to domain resources. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Domain member- Digitally encrypt secure channel data (when possible) is enabled | If addressed: Enabling this setting allows domain member machines to encrypt secure channel data when supported, enhancing the confidentiality and integrity of communications with domain controllers.
If not addressed: : If not enabled, secure channel data might be transmitted without encryption when possible, increasing the risk of interception and potential credential exposure during network communication. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Domain member- Digitally sign secure channel data (when possible) is enabled | If addressed: Enabling this setting allows domain member machines to digitally sign secure channel data when supported, ensuring data integrity and authenticity in communications with domain controllers.
If not addressed: : Without this enabled, secure channel data may be unsigned when possible, increasing the risk of data tampering or man-in-the-middle attacks that compromise authentication security. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Domain member- Disable machine account password changes is disabled | If addressed (setting disabled): Allowing domain member machines to change their machine account passwords regularly enhances security by preventing stale or compromised credentials, maintaining trust with domain controllers.
If not addressed: (setting enabled): If machine account password changes are disabled, domain members won- update their passwords, which can lead to trust relationship failures and authentication problems over time. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Domain member- Maximum machine account password age is set | If addressed: Setting a maximum machine account password age enforces regular password changes for domain member computer accounts, which helps prevent long-term credential exposure and maintains secure trust relationships with domain controllers.
If not addressed: : Without a defined maximum password age, machine account passwords may never change or change infrequently, increasing the risk of compromised credentials and domain trust failures. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Domain member- Require strong (Windows 2000 or later) session key is enabled | If addressed: Enabling this setting enforces the use of strong session keys for secure channel communications, enhancing cryptographic strength and protecting data integrity and confidentiality between domain members and domain controllers.
If not addressed: : Without this enforcement, weaker session keys may be used, increasing the risk of cryptographic attacks such as session hijacking or data tampering during authentication and communication. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Interactive logon- Machine inactivity limit is set | If addressed: Setting a machine inactivity limit ensures that inactive sessions automatically lock after a specified time, reducing the risk of unauthorized access from unattended logged-in computers.
If not addressed: : Without an inactivity timeout, machines remain accessible even when left unattended, increasing the chances of unauthorized use or data exposure. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Microsoft network client- Digitally sign communications (always) is enabled | If addressed: Enabling this setting ensures that all SMB communications from the client to servers are digitally signed, protecting data integrity and preventing man-in-the-middle attacks during file and resource sharing.
If not addressed: : Without mandatory digital signing, SMB traffic can be intercepted or tampered with, leading to potential data breaches or unauthorized access. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Microsoft network client- Send unencrypted password to third-party SMB servers is disabled | If addressed: Disabling the sending of unencrypted passwords prevents sensitive credentials from being transmitted in clear text to third-party SMB servers, significantly reducing the risk of credential theft and man-in-the-middle attacks.
If not addressed: : Allowing unencrypted password transmission exposes user credentials to interception and compromise, increasing the risk of unauthorized access and lateral movement within the network. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Microsoft network server- Digitally sign communications (always) is enabled | If addressed: Enabling this setting enforces digital signing of all SMB communications on the server side, ensuring data integrity and protecting against man-in-the-middle attacks during file sharing.
If not addressed: : Without enforced digital signing, SMB traffic may be vulnerable to tampering or interception, leading to potential data breaches or unauthorized access to resources. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Network access- Do not allow anonymous enumeration of SAM accounts is enabled | If addressed: Enabling this setting prevents anonymous users from listing user accounts in the Security Accounts Manager (SAM), reducing information disclosure risks and protecting against reconnaissance attacks by unauthorized parties.
If not addressed: : Allowing anonymous enumeration exposes account details that attackers can use to plan targeted attacks such as password guessing or privilege escalation. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Network access- Do not allow anonymous enumeration of SAM accounts and shares is enabled | If addressed: Enabling this setting prevents anonymous users from enumerating both SAM accounts and network shares, protecting sensitive account information and shared resources from unauthorized discovery and potential exploitation.
If not addressed: : Allowing anonymous enumeration exposes user account details and shared folders to attackers, increasing the risk of reconnaissance activities that could lead to targeted attacks or unauthorized access. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Network security- Allow LocalSystem NULL session fallback is enabled | If addressed (enabled): Allowing LocalSystem NULL session fallback can provide backward compatibility for legacy applications but significantly increases the risk of anonymous access to system resources, making the system vulnerable to unauthorized access and potential attacks.
If not addressed: (disabled): Disabling this setting enhances security by preventing the system from accepting NULL session fallback connections, reducing the attack surface and mitigating risks associated with anonymous access exploits. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Network security- Allow LocalSystem NULL session fallback is disabled | If addressed (disabled): Disabling LocalSystem NULL session fallback strengthens security by preventing anonymous fallback connections, reducing the risk of unauthorized access and exploitation through legacy authentication methods.
If not addressed: (enabled): Allowing NULL session fallback exposes the system to potential anonymous access attacks, increasing the attack surface and enabling attackers to gain unauthorized access to system resources. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Network security- Do not store LAN Manager hash value on next password change is enabled | If addressed (enabled): Enabling this setting prevents the storage of weak LAN Manager (LM) hashes for user passwords, significantly enhancing password security by mitigating risks related to hash cracking and replay attacks.
If not addressed: (disabled): Storing LM hashes exposes user passwords to easy compromise due to their weak cryptographic nature, increasing the risk of credential theft and unauthorized access |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Network security- LAN Manager authentication level is configured | If addressed (properly configured): Configuring the LAN Manager authentication level enforces stronger authentication protocols, reducing vulnerabilities to downgrade attacks and ensuring only secure authentication methods are used.
If not addressed: (misconfigured or left default): Weak or default LAN Manager authentication settings allow fallback to insecure authentication methods, exposing systems to credential theft and man-in-the-middle attacks. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Network security- LDAP client signing requirements | If addressed (enabled): Enforcing LDAP client signing ensures that LDAP communication between clients and domain controllers is signed, protecting against man-in-the-middle attacks and data tampering.
If not addressed: (disabled): Lack of LDAP signing leaves LDAP traffic vulnerable to interception and modification, potentially exposing sensitive information and enabling credential theft or unauthorized access. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Network security- Minimum session security for NTLM SSP based (including secure RPC) clients is configured | If addressed (properly configured): Configuring minimum session security enforces encryption and signing for NTLM SSP communication, protecting data integrity and confidentiality during authentication and RPC sessions.
If not addressed: (not configured or disabled): Lack of minimum session security leaves NTLM SSP communications vulnerable to interception, replay, and man-in-the-middle attacks, compromising sensitive authentication data. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Network security- Minimum session security for NTLM SSP based (including secure RPC) servers is configured | If addressed (properly configured): Enforcing minimum session security on NTLM SSP servers ensures that all incoming NTLM authentication and secure RPC sessions require encryption and signing, reducing the risk of man-in-the-middle attacks and data tampering.
If not addressed: (not configured or disabled): Without this enforcement, NTLM authentication and RPC sessions can occur without adequate protection, making servers vulnerable to interception, replay attacks, and unauthorized access. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure System objects- Strengthen default permissions of internal system objects is enabled | If addressed (enabled): Strengthening default permissions on internal system objects prevents unauthorized users or processes from modifying critical system objects, enhancing overall system security and stability.
If not addressed: (disabled or not configured): Weak default permissions can allow malicious actors or software to alter or exploit system objects, potentially leading to privilege escalation, system compromise, or denial of service. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure User Account Control- Admin Approval Mode for the Built-in Administrator account is enabled | If addressed (enabled): Enabling Admin Approval Mode for the built-in Administrator account enforces User Account Control (UAC) prompts for administrative actions, reducing the risk of unauthorized or accidental changes and limiting malware impact.
If not addressed: (disabled): Without Admin Approval Mode, the built-in Administrator account runs with full privileges all the time, increasing the risk of unmonitored administrative actions, privilege escalation, and malware persistence. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure User Account Control- Behavior of the elevation prompt for administrators in Admin Approval Mode is defined | If addressed (properly defined): Defining the elevation prompt behavior ensures that administrators receive consistent, secure prompts before performing tasks requiring elevated privileges, reducing the risk of accidental or unauthorized elevation.
If not addressed: (undefined or misconfigured): Undefined or insecure prompt behavior can lead to silent elevation, increasing the risk of unauthorized system changes, privilege escalation, and malware exploiting elevated privileges without user awareness. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure User Account Control- Behavior of the elevation prompt for standard users is defined | If addressed (properly defined): Defining the elevation prompt behavior for standard users ensures that administrative tasks require explicit credentials, preventing unauthorized privilege escalation and reinforcing least privilege principles.
If not addressed: (undefined or misconfigured): If this setting is not defined, standard users may be allowed to bypass elevation prompts or receive inconsistent behavior, increasing the risk of security breaches and malware executing with elevated privileges. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure User Account Control- Detect application installations and prompt for elevation is defined | If addressed (enabled): Enabling this setting ensures that application installation attempts are automatically detected and trigger an elevation prompt, helping prevent unauthorized or silent installations by non-admin users or malware.
If not addressed: (disabled or undefined): If this setting is not defined, standard users may install applications without administrative approval, increasing the risk of malware infections, software conflicts, or system instability. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure User Account Control- Only elevate UIAccess applications that are installed in secure locations is enabled | If addressed (enabled): Enabling this setting ensures that only UIAccess applications installed in secure directories (e.g., Program Files or Windows\System32) can be elevated, preventing unauthorized or malicious UIAccess apps from gaining elevated privileges.
If not addressed: (disabled or not configured): If this setting is not enabled, attackers could place UIAccess applications in non-secure locations (like temp folders or user profiles) to exploit UAC and gain elevated access. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure User Account Control- Run all administrators in Admin Approval Mode is enabled | If addressed (enabled): Enabling this setting ensures that only UIAccess applications installed in secure directories (e.g., Program Files or Windows\System32) can be elevated, preventing unauthorized or malicious UIAccess apps from gaining elevated privileges.
If not addressed: (disabled or not configured): If this setting is not enabled, attackers could place UIAccess applications in non-secure locations (like temp folders or user profiles) to exploit UAC and gain elevated access. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure User Account Control- Virtualize file and registry write failures to per-user locations is enabled | If addressed (enabled): Enabling this setting ensures that legacy applications that try to write to protected system locations (like Program Files or HKLM) are redirected (virtualized) to per-user locations, allowing them to function without compromising system security.
If not addressed: (disabled): Disabling this setting can cause legacy or poorly written applications to fail when attempting restricted writes, potentially leading to application crashes or user complaints, or worse-ncouraging users to run apps with full admin rights, increasing security risk. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Credential Validation is configured | If addressed (configured): Configuring audit for Credential Validation allows security teams to monitor and detect credential-based attacks (e.g., brute force, pass-the-hash, or account lockouts) through detailed logon event records.
If not addressed: (not configured): Without this audit, malicious authentication attempts may go unnoticed, making it difficult to identify or respond to credential misuse, compromise, or policy violations. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Computer Account Management is configured | If addressed (configured): Enabling auditing for Computer Account Management ensures that creation, deletion, modification, or renaming of computer accounts in Active Directory is logged, supporting security auditing, incident response, and change tracking.
If not addressed: (not configured): Without this audit policy, changes to computer accounts may go undetected, increasing the risk of unauthorized device registrations or malicious tampering within AD. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Other Account Management Events is configured | If addressed (configured): Enabling Audit Other Account Management Events ensures actions such as password resets, user account disablement, or changes to user group memberships are logged, which is critical for tracking administrative changes and detecting insider threats.
If not addressed: (not configured): Without this auditing, important account changes could go unnoticed, reducing visibility into potential misuse of privileges and hampering forensic investigations. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Security Group Management is configured | If addressed (configured): Enabling Audit Security Group Management ensures all changes to security groups (creation, deletion, membership changes) are logged, which is essential for detecting privilege escalation, unauthorized access, and compliance tracking.
If not addressed: (not configured): Without this audit, malicious or accidental changes to security groups (e.g., adding a user to Domain Admins) may go unnoticed, leading to potential data breaches or administrative misuse. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit User Account Management is configured | If addressed (configured): Enabling Audit User Account Management ensures that key changes to user accounts-uch as creation, deletion, password resets, and account disables-re logged for accountability, forensic investigations, and compliance.
If not addressed: (not configured): Without this setting, unauthorized or accidental modifications to user accounts may go undetected, increasing the risk of privilege misuse, insider threats, or audit failures. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit PNP Activity is configured | If addressed (configured): Enabling Audit PnP (Plug and Play) Activity helps track device installations and removals on systems, allowing detection of unauthorized or suspicious hardware changes that could indicate security breaches or policy violations.
If not addressed: (not configured): Without auditing PnP activity, unauthorized devices might be connected without detection, increasing the risk of data exfiltration, malware introduction, or hardware-based attacks. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Process Creation is configured | If addressed (configured): Enabling Audit Process Creation provides detailed logging of every process started on a system, which is crucial for detecting malicious activities, forensic analysis, and understanding system behavior.
If not addressed: (not configured): Without auditing process creation, attackers could execute malicious programs undetected, making it difficult to investigate security incidents or identify unauthorized software execution. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Directory Service Access is configured | If addressed (configured): Enabling Audit Directory Service Access allows monitoring and logging of access to Active Directory objects, which helps detect unauthorized changes or access attempts to sensitive directory data.
If not addressed: (not configured): Without auditing Directory Service access, malicious or accidental changes to AD objects could go unnoticed, increasing the risk of privilege escalation, data compromise, and compliance violations. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Directory Service Changes is configured | If addressed (configured): Enabling Audit Directory Service Changes ensures that all modifications to Active Directory objects (such as user accounts, groups, and policies) are logged, helping detect unauthorized or accidental changes that could compromise security.
If not addressed: (not configured): Without auditing directory service changes, malicious modifications could occur without detection, increasing the risk of privilege escalation, data breaches, and compliance failures. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Account Lockout is configured | If addressed (configured): Enabling Audit Account Lockout provides visibility into account lockout events, helping to detect potential brute-force attacks or unauthorized access attempts and facilitating timely security response.
If not addressed: (not configured): Without auditing account lockouts, suspicious activity may go unnoticed, increasing the risk of prolonged attacks and compromised accounts. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Group Membership is configured | If addressed (configured): Enabling Audit Group Membership provides detailed logging of changes to group memberships, which helps detect unauthorized privilege escalations and maintain the integrity of access controls.
If not addressed: (not configured): Without auditing group membership changes, malicious additions or removals of users from sensitive groups can go unnoticed, increasing risk of insider threats and security breaches. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Logon is configured | If addressed (configured): Enabling Audit Logon provides visibility into all user logon and logoff activities, enabling detection of unauthorized access attempts and forensic investigations.
If not addressed: (not configured): Without auditing logon events, suspicious or malicious login attempts may go unnoticed, increasing the risk of undetected breaches and insider threats. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Other Logon and Logoff Events is configured | If addressed (configured): Enabling Audit Other Logon and Logoff Events provides comprehensive logging of additional logon and logoff activities such as network connections, remote desktop sessions, and special system logons, improving detection of suspicious or unauthorized access.
If not addressed: (not configured): Without auditing these events, certain types of access may not be tracked, creating blind spots that attackers could exploit to move laterally or maintain persistence unnoticed. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Special Logon is configured | If addressed (configured): Enabling Audit Special Logon captures important events such as logons by users with elevated privileges (e.g., administrators) or service accounts, helping detect unauthorized privilege escalation or suspicious activities.
If not addressed: (not configured): Without auditing special logons, malicious use of privileged accounts or service accounts can go unnoticed, increasing the risk of undetected attacks and privilege misuse. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Detailed File Share is configured | If addressed (configured): Enabling detailed file share auditing provides visibility into access and changes to shared files and folders, helping detect unauthorized or malicious activity on critical data.
If not addressed: (not configured): Lack of detailed auditing on file shares can lead to undetected unauthorized access or data leakage, increasing the risk of data breaches and non-compliance with security policies. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit File Share is configured | If addressed: Enabling Audit File Share allows organizations to track access to shared folders and files, which helps detect unauthorized access, data exfiltration attempts, and supports compliance requirements.
If not addressed: : Without auditing, malicious or accidental access to sensitive shared data may go unnoticed, increasing the risk of data breaches and non-compliance with security standards. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Other Object Access Events is configured | If addressed: Configuring audit for other object access events ensures that access and modifications to system objects like registry keys, printers, or kernel objects are logged, improving visibility into potentially malicious or unauthorized activities.
If not addressed: : Lack of auditing for these object types can result in blind spots where critical system changes go unnoticed, increasing the risk of undetected compromises or policy violations. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Removable Storage is configured | If addressed: Enabling audit for removable storage devices helps track usage of USB drives, external hard disks, and other removable media, providing visibility into potential data exfiltration or malware introduction vectors.
If not addressed: : Without auditing removable storage, organizations risk undetected unauthorized data transfers or malware infections via external devices, leading to data breaches or system compromises. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Audit Policy Change is configured | If addressed: Configuring audit for policy changes ensures that any modifications to audit policies are logged, providing visibility into potential tampering or unauthorized changes that could hide malicious activity.
If not addressed: : Without auditing audit policy changes, attackers or insiders can alter or disable audit settings to avoid detection, increasing the risk of undetected security breaches. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Authentication Policy Change is configured | If addressed: Enabling auditing for authentication policy changes provides visibility into modifications of authentication methods, helping detect unauthorized or malicious alterations that could weaken security.
If not addressed: : Without this audit, attackers may change authentication policies undetected, potentially allowing easier unauthorized access and increasing risk of credential compromise. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit MPSSVC Rule-Level Policy Change is configured | If addressed: Enabling audit for MPSSVC (Microsoft Protection Service) rule-level policy changes ensures that any modifications to Windows Firewall rules are logged, helping detect unauthorized or accidental security changes.
If not addressed: : Without auditing, changes to firewall rules may go unnoticed, potentially exposing systems to attacks or allowing malicious traffic through, increasing the risk of breaches. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Other Policy Change Events is configured | If addressed: Configuring audit for Other Policy Change Events ensures that any modifications to security or system policies not covered by other audit categories are logged, providing comprehensive visibility into policy changes.
If not addressed: : Lack of auditing may allow unauthorized or accidental policy changes to go undetected, increasing the risk of security misconfigurations and potential breaches. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Sensitive Privilege Use is configured | If addressed: Enabling auditing for sensitive privilege use allows organizations to monitor and log whenever critical privileges (like SeDebugPrivilege, SeTakeOwnershipPrivilege) are used, enhancing detection of potential privilege abuse or malicious activity.
If not addressed: : Without auditing, unauthorized or malicious use of sensitive privileges may go unnoticed, increasing the risk of privilege escalation attacks and insider threats. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Other System Events is configured | If addressed: Configuring auditing for other system events ensures that important but less common system activities (like system shutdowns, driver installations, or changes in system state) are logged, aiding in comprehensive security monitoring and forensic investigations.
If not addressed: : Failure to audit these events can result in missing critical indicators of system compromise or improper changes, weakening overall security posture and incident detection. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Security State Change is configured | If addressed: Enabling auditing for Security State Changes provides visibility into critical changes to the security subsystem, such as security policy modifications or security system shutdowns, which helps detect unauthorized or malicious activity.
If not addressed: : Without auditing Security State Changes, important security modifications may go unnoticed, increasing the risk of undetected breaches or policy tampering that could compromise system integrity. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit Security System Extension is configured | If addressed: Enabling auditing for Security System Extensions helps track the loading and unloading of security-related system extensions, aiding in detecting unauthorized or malicious components that could compromise system security.
If not addressed: : Without this auditing, malicious or unauthorized security extensions might be installed or removed without detection, increasing the risk of persistent threats or system compromise. |
| NIST-CIS Domain Controllers Settings | MITREANSSI |
Ensure Audit System Integrity is configured | If addressed: Enabling Audit System Integrity helps detect and log attempts to violate system integrity, such as kernel code injections, unauthorized driver loads, or other tampering activities, improving early detection of attacks on core system components.
If not addressed: : Without this auditing, critical system integrity violations may go unnoticed, allowing attackers to compromise system trustworthiness and persist undetected. |
| Configuration-DomainController | MITREANSSI |
Roles and Features-The Fax Server role must not be installed | If addressed: Removing the Fax Server role reduces the attack surface by eliminating unnecessary services, lowering the risk of exploitation and resource consumption on the server.
If not addressed: : Keeping the Fax Server role installed when not needed increases potential vulnerabilities, possibly exposing the system to attacks or misuse and wasting system resources. |
| Configuration-DomainController | MITREANSSI |
Roles and Features-The Microsoft FTP service must not be installed unless required | If addressed: Removing or not installing the Microsoft FTP service reduces the attack surface by eliminating unnecessary network services, lowering the risk of exploitation and unauthorized access.
If not addressed: : Having the FTP service installed when not required can expose the server to potential vulnerabilities, unauthorized data access, or data leakage through insecure FTP protocols. |
| Configuration-DomainController | MITREANSSI |
Roles and Features-The Peer Name Resolution Protocol must not be installed | If addressed: Removing or not installing PNRP reduces the attack surface by disabling a protocol that can be exploited for unauthorized peer-to-peer communication, enhancing network security and reducing potential lateral movement vectors.
If not addressed: : Leaving PNRP installed unnecessarily can expose systems to peer-to-peer network threats, increasing the risk of malware propagation and unauthorized device discovery within the network. |
| Configuration-DomainController | MITREANSSI |
Roles and Features-Simple TCP-IP Services must not be installed | If addressed: Removing or not installing PNRP reduces the attack surface by disabling a protocol that can be exploited for unauthorized peer-to-peer communication, enhancing network security and reducing potential lateral movement vectors.
If not addressed: : Leaving PNRP installed unnecessarily can expose systems to peer-to-peer network threats, increasing the risk of malware propagation and unauthorized device discovery within the network. |
| Configuration-DomainController | MITREANSSI |
Roles and Features-The Telnet Client must not be installed | If addressed: Removing the Telnet Client prevents the use of an insecure, plaintext protocol, reducing the risk of credential interception and unauthorized access, thereby enhancing network security.
If not addressed: : Having the Telnet Client installed allows users to connect to remote systems using Telnet, which transmits data unencrypted and can be intercepted by attackers, leading to potential compromise of credentials and sensitive information. |
| Configuration-DomainController | MITREANSSI |
Roles and Features-The TFTP Client must not be installed | If addressed: Removing the TFTP Client reduces the attack surface by eliminating an insecure protocol that transmits data without encryption, helping protect sensitive data and prevent unauthorized access.
If not addressed: : Having the TFTP Client installed allows use of the Trivial File Transfer Protocol, which is inherently insecure due to lack of authentication and encryption, increasing the risk of data interception and malicious file transfers. |
| Configuration-DomainController | MITREANSSI |
Roles and Features-The Server Message Block (SMB) v1 protocol must be uninstalled | If addressed: Removing SMB v1 mitigates significant security vulnerabilities, such as those exploited by ransomware (e.g., WannaCry), by disabling an outdated and insecure protocol. This enhances the overall security posture by ensuring only modern, secure SMB versions (v2/v3) are used.
If not addressed: : Leaving SMB v1 enabled exposes the environment to severe risks including man-in-the-middle attacks, data interception, and propagation of malware, since SMB v1 lacks modern security features and is widely exploited. |
| Configuration-DomainController | MITREANSSI |
Roles and Features-Windows PowerShell 2.0 must not be installed | If addressed: Removing PowerShell 2.0 reduces the attack surface by eliminating a legacy version that lacks modern security features, such as script block logging and constrained language mode, thereby enhancing system security.
If not addressed: : Retaining PowerShell 2.0 increases risk because attackers can exploit its outdated features to execute malicious scripts without detection or restrictions, potentially leading to compromise or lateral movement. |
| Security and Risk | MITREANSSI |
Found Hidden Domain Controllers | If addressed: Discovering and removing hidden or unauthorized domain controllers ensures the security and integrity of the Active Directory environment by preventing rogue or compromised DCs from undermining authentication and replication processes.
If not addressed: : Hidden domain controllers can be exploited by attackers to gain persistent, stealthy access to the network, manipulate authentication, and cause replication issues, leading to a potential full domain compromise. |
| Security and Risk | MITREANSSI |
Successful Exploit Machine Accounts Found | If addressed: Identifying and mitigating exploited machine accounts prevents attackers from maintaining persistence, escalating privileges, or moving laterally within the network, thereby reducing the risk of a broader compromise.
If not addressed: : Exploited machine accounts can allow attackers to impersonate trusted machines, access sensitive resources, and perform unauthorized actions, significantly increasing the risk of data breaches and network compromise. |
| Security and Risk | MITREANSSI |
Possible User-based Service Accounts found | If addressed:
Allows identification and migration of legacy user-based service accounts to managed service accounts (like gMSA), improving automation and password security.
If not addressed: :
Manual password management continues for service accounts, increasing risk of password leaks, reuse, or credential theft. |
| Security and Risk | MITREANSSI |
Scheduled Tasks found on Domain Controllers | If addressed:
Reviewing scheduled tasks Ensures no unauthorized scripts or malicious jobs are running on DCs.
If not addressed: :
malicious tasks Could persist, execute commands silently, or exfiltrate data from domain controllers. |
| Security and Risk | MITREANSSI |
High Value Targets | If addressed:
Allows you to monitor and apply stricter policies to critical objects (admins, DCs, VIPs).
If not addressed: :
High-value assets may remain unprotected, increasing risk of targeted attacks or data breaches. |
| Security and Risk | MITREANSSI |
Accounts with Extended Rights to Read LAPS Passwords Found | If addressed:
Ensures only authorized Users/groups can retrieve LAPS-managed local admin Passwords, protecting against privilege escalation.
If not addressed: :
unauthorized Users may read local Administrator Passwords from AD and gain control over machines across the environment.J341 |
| Security and Risk | MITREANSSI |
Misconfigured Administrative Accounts Found | If addressed:
Enabling -sensitive and cannot be delegated- Prevents admin credentials from being Exposed during delegation, significantly strengthening security for privileged accounts.
If not addressed: :
admin credentials may be Exposed through delegation, increasing the risk of credential theft and lateral movement by attackers |
| Security and Risk | MITREANSSI |
Administrator Account ServicePrincipalNames Found | If addressed: Identifying and properly managing SPNs associated with Administrator accounts prevents misuse in Kerberos authentication and reduces the risk of privilege escalation through Kerberoasting attacks.
If not addressed: : Uncontrolled or exposed SPNs linked to Administrator accounts can be exploited by attackers to extract service tickets and crack them offline, potentially leading to domain admin credential compromise. |
| Security and Risk | MITREANSSI |
Software Installed on Domain Controllers | If addressed:
Reviewing and removing unnecessary software limits attack vectors and maintains a hardened DC environment.
If not addressed: :
Unvetted or outdated software may introduce vulnerabilities or violate compliance standards on critical infrastructure. |
| Security and Risk | MITREANSSI |
Domain Trusts Found | If addressed: Properly managing and securing domain trusts ensures that only authorized domains have access, reducing the attack surface and preventing unauthorized access across trusted domains.
If not addressed: : Unmonitored or misconfigured domain trusts can allow attackers to pivot between domains, escalate privileges, and compromise additional resources in the trusted environment. |
| Security and Risk | MITREANSSI |
Group Policy Object Assignments with Improper Permissions Found | If addressed:
Restricts GPO editing and delegation to only authorized administrators, preventing unauthorized GPO changes and privilege escalation.
If not addressed: :
Improper permissions may allow attackers or Non-admin Users to modify GPOs, leading to security Policy violations or environment compromise |
| Security and Risk | MITREANSSI |
No Group Policy Objects Defining Log Size and Retention | If addressed:
Ensures logs are retained Long enough and sized appropriately for incident response and auditing.
If not addressed: :
Important logs may be overwritten quickly or lost, reducing visibility into attacks or misconfigurations. |
| Security and Risk | MITREANSSI |
Group Policy Objects with Improper Permissions Found | If addressed: Securing Group Policy Objects (GPOs) with proper permissions prevents unauthorized users from modifying policies, thereby maintaining the integrity and security of the domain environment.
If not addressed: : Improper permissions on GPOs can allow attackers or malicious insiders to alter policies, leading to privilege escalation, deployment of malicious configurations, or disruption of security controls. |
| Security and Risk | MITREANSSI |
No Group Policy Objects to Prevent Domain Admins from logging on to Workstations or Servers Found | If addressed:
Implementing the GPO Restricts domain admin logons to only domain controllers, reducing exposure of privileged credentials to potentially compromised machines.
If not addressed: :
domain admin credentials can be Exposed on less secure endpoints, increasing risk of credential theft and domain compromise. |
| Security and Risk | MITREANSSI |
No Group Policy Objects to Block ISO Execution Found | If addressed:
Blocking ISO file execution Prevents Users from running potentially malicious content from ISO images, aligning with CIS security best practices.
If not addressed: :
Users can mount and run ISO files, potentially launching malware, ransomware, or unauthorized software. |
| Security and Risk | MITREANSSI |
No Group Policy Objects to Mitigate SMBv1 Found | If addressed:
disabling SMBv1 via GPO protects all machines from known exploits targeting the protocol.
If not addressed: :
Environments remain Exposed to ransomware like WannaCry, which exploit SMBv1 |
| Security and Risk | MITREANSSI |
No Group Policy Objects Enforcing UAC Prompt for Elevation Found | If addressed: Enforcing UAC (User Account Control) prompts for elevation ensures that administrative actions require explicit user consent, reducing the risk of unauthorized or silent privilege escalation by malware or users.
If not addressed: : Without UAC elevation prompts, malicious software or users may perform administrative tasks without notification, increasing the likelihood of system compromise and unauthorized changes. |
| Security and Risk | MITREANSSI |
No Group Policy Objects to Mitigate Accidental Script Execution | If addressed:
Blocks unauthorized or unintentional script execution via GPO, reducing attack surface.
If not addressed: :
scripts may be run by mistake or maliciously, Enabling privilege escalation or system compromise. |
| Security and Risk | MITREANSSI |
No Group Policy Objects to Mitigate NTLMv1 Protocol | If addressed:
disabling NTLMv1 protects the environment from Weak authentication exploits.
If not addressed: :
use of NTLMv1 Allows downgrade attacks, hash cracking, and man-in-the-middle exploits. |
| Security and Risk | MITREANSSI |
AdminsCount Flag set users not acting as Admins | If addressed:
Prevents unnecessary protection of Non-privileged Users and Ensures only actual admin accounts are flagged, reducing unintended permission inheritance issues.
If not addressed: :
unnecessary AdminCount flags may result in Improper ACLs, leading to access control inconsistencies and potential privilege misuse. |
| Security and Risk | MITREANSSI |
Accounts vulnerable to Kerberoasting Found | If addressed:
Validates that service accounts with SPNs are protected and Not exposing password hashes to potential attackers. This Reduces the risk of Kerberoasting attacks.
If not addressed: :
attackers may request Kerberos tickets for these accounts, extract them offline, and crack the password hash to escalate privileges. |
| Security and Risk | MITREANSSI |
No Contacts with Domain Controllers in Last Three Months | If addressed:
Secures domain controllers by removing unnecessary resource-based delegations, limiting the risk of lateral movement via impersonation.
If not addressed: :
Improper resource-based delegation Could let compromised machines impersonate Users to sensitive services hosted on domain controllers. |
| Security and Risk | MITREANSSI |
Password Expiration is missing for smart card users | If addressed: Enforcing password expiration for smart card users ensures that backup password credentials remain secure and are regularly updated, reducing the risk of unauthorized access if the smart card is lost or compromised.
If not addressed: : Without password expiration, stale or compromised passwords may remain valid indefinitely, increasing the attack surface and potential for unauthorized access despite the use of smart cards. |
| Security and Risk | MITREANSSI |
Found Groups with SID history Set | If addressed: Removing or properly managing SID History reduces the risk of privilege escalation or unauthorized access due to lingering old permissions from migrated or renamed groups. It helps maintain clear and secure access control by preventing misuse of outdated security identifiers.
If not addressed: : Groups with SID History can be exploited by attackers to gain unauthorized access by leveraging legacy permissions, increasing the attack surface and potential for privilege escalation or access to sensitive resources. |
| Security and Risk | MITREANSSI |
Pre-Windows 2000 Compatible Access Group is not empty | If addressed:
Removes legacy access paths to modern resources and Ensures tighter access control.
If not addressed: :
Users in This group may access objects anonymously or bypass newer security models. |
| Security and Risk | MITREANSSI |
Managed service accounts with passwords unchanged for more than 90 days | If addressed: Regularly changing managed service account passwords reduces the risk of credential compromise and unauthorized access, ensuring stronger security hygiene and compliance with best practices.
If not addressed: : Stale passwords increase the risk of exploitation if credentials are leaked or cracked, potentially allowing attackers persistent access to critical services and systems. |
| Security and Risk | MITREANSSI |
Too Many Privileged Accounts | If addressed:
Reduces attack surface by ensuring only required Users have administrative privileges.
If not addressed: :
Excess privileged accounts increase the chance of misuse, misconfiguration, or compromise. |
| Security and Risk | MITREANSSI |
Dangerous Permissions Found on MicrosoftDNS Container | If addressed:
Secures DNS-related configuration by revoking excessive permissions from Non-administrators.
If not addressed: :
improperly permissioned accounts Could manipulate DNS settings, Enabling redirection or spoofing. |
| Security and Risk | MITREANSSI |
Dangerous Permissions Found on Naming Contexts | If addressed:
protects critical AD partitions from unauthorized modification.
If not addressed: :
attackers Could escalate privileges or tamper with directory replication and schema. |
| Security and Risk | MITREANSSI |
Found Unused Netlogon Scripts | If addressed: Removing unused Netlogon scripts reduces the attack surface by eliminating outdated or potentially vulnerable scripts that could be exploited by attackers, improving system security and management clarity.
If not addressed: : Unused Netlogon scripts may contain outdated code or credentials that attackers could leverage to compromise systems or gain unauthorized access, increasing security risks and administrative confusion. |
| Security and Risk | MITREANSSI |
Abusable Permissions Found on SYSVOL and NETLOGON | If addressed:
Removes excessive write permissions on critical shares used by GPOs, preventing tampering.
If not addressed: :
malicious Users may modify login scripts or GPOs to spread malware or create persistence. |
| Security and Risk | MITREANSSI |
No Group Policy Objects for Preventing passwords using reversible encryption | If addressed: Enforcing a Group Policy to prevent storing passwords using reversible encryption enhances password security by ensuring passwords are not stored in a format easily decrypted or compromised, reducing the risk of credential theft.
If not addressed: : Passwords stored with reversible encryption can be decrypted by attackers who gain access to the system, potentially leading to unauthorized access and lateral movement within the network. |
| Security and Risk | MITREANSSI |
Ensure UNC Paths for SYSVOL and NETLOGON are harderend | If addressed: Hardening UNC paths for SYSVOL and NETLOGON protects critical domain controller shares from unauthorized access or tampering, reducing the risk of malicious modifications to Group Policy and login scripts.
If not addressed: : Unsecured UNC paths can be exploited by attackers to modify or replace files in SYSVOL and NETLOGON shares, leading to privilege escalation, persistent malware, or domain-wide compromise. |
| Security and Risk | MITREANSSI |
GPO Preferences Containing Passwords | If addressed:
Removes plaintext Passwords from SYSVOL and Prevents credential disclosure.
If not addressed: :
Any user can retrieve and decrypt GPP-stored Passwords from SYSVOL, leading to lateral movement or privilege escalation. |
| Security and Risk | MITREANSSI |
Unauthorized Users having GPLink Rights on Domain NC | If addressed: Restricting GPLink rights to authorized users ensures that only trusted administrators can link Group Policy Objects (GPOs) to the Domain Naming Context (NC), reducing the risk of unauthorized policy changes and potential security breaches.
If not addressed: : Unauthorized users with GPLink rights can link malicious or misconfigured GPOs to the domain, potentially enforcing harmful policies, compromising security, and disrupting domain operations. |
| Security and Risk | MITREANSSI |
Unauthorized Users having GPLink Rights on Domain Controllers OU | If addressed: Restricting GPLink permissions to authorized users ensures that only trusted administrators can link Group Policy Objects (GPOs) to the Domain Controllers OU, preventing unauthorized policy changes and maintaining security posture.
If not addressed: : Unauthorized users with GPLink rights can link malicious or misconfigured GPOs to the Domain Controllers OU, potentially causing security breaches, privilege escalation, or disruption of domain controller operations. |
| Security and Risk | MITREANSSI |
Unauthorized Users having GPLink Rights on AD Sites | If addressed: Ensuring only authorized users have GPLink rights on Active Directory Sites limits the ability to link Group Policy Objects (GPOs) to AD Sites, reducing the risk of malicious or accidental policy application that could affect network behavior and security.
If not addressed: : Unauthorized users with GPLink rights on AD Sites can link harmful or inappropriate GPOs, potentially leading to security vulnerabilities, network disruptions, or unintended policy enforcement within the site. |
| Security and Risk | MITREANSSI |
LAPS SearchFlag modified | If addressed: Correctly configuring the LAPS (Local Administrator Password Solution) SearchFlag ensures that the schema attributes for storing local admin passwords are set as intended, enabling secure password management and retrieval.
If not addressed: : A modified or incorrect SearchFlag can cause LAPS to malfunction, leading to failure in password expiration, update, or retrieval processes, which increases the risk of compromised local administrator accounts and security gaps. |
| Security and Risk | MITREANSSI |
Found Bitlocker Disabled Computers | If addressed: Enabling BitLocker ensures full disk encryption, protecting sensitive data on computers from unauthorized access in case of theft or loss, thereby reducing the risk of data breaches.
If not addressed: : Computers without BitLocker are vulnerable to data theft and unauthorized access, especially if lost or stolen, which can lead to significant data breaches and compliance violations. |
| Security and Risk | MITREANSSI |
Found Computers Running Obsolete OS Versions | If addressed: Updating or replacing obsolete OS versions reduces exposure to unpatched vulnerabilities and security risks, enhancing the overall security posture and compliance with industry standards.
If not addressed: : Running outdated OS versions leaves systems vulnerable to exploits, malware, and compatibility issues, increasing the risk of security breaches and potential data loss. |
| Security and Risk | MITREANSSI |
Found Service Accounts With Unchanged Passwords | If addressed: Regularly changing service account passwords reduces the risk of unauthorized access due to password compromise, enhancing overall security and limiting potential attack vectors.
If not addressed: : Unchanged passwords increase the likelihood of credential theft or misuse, potentially leading to privilege escalation, data breaches, or persistent attacker presence. |
| Security and Risk | MITREANSSI |
Service Accounts Supported Encryption Algorithms | If addressed: Ensuring service accounts use strong, modern encryption algorithms protects credentials during authentication, reducing the risk of interception and unauthorized access.
If not addressed: : Use of weak or outdated encryption algorithms can lead to credential compromise through attacks such as downgrade or brute force, increasing the risk of account takeover and data breaches. |
| Security and Risk | MITREANSSI |
Found Inactive Service Accounts | If addressed: Removing or disabling inactive service accounts reduces your attack surface and helps prevent unauthorized use or compromise of dormant credentials.
If not addressed: : Inactive service accounts can be exploited by attackers to gain persistent access, escalate privileges, or move laterally within the environment unnoticed. |
| Security and Risk | MITREANSSI |
Found Computers With Anomalous Primary Group ID | If addressed: Ensuring computer accounts have correct Primary Group IDs maintains AD integrity and prevents unauthorized privilege escalation or misconfigured permissions.
If not addressed: : Anomalous Primary Group IDs may indicate misconfigured or malicious activity, potentially allowing attackers to hide in privileged groups or bypass security controls. |
| Security and Risk | MITREANSSI |
Found Computers With Unreadable Primary Group ID | If addressed: Fixing unreadable Primary Group IDs on computer accounts ensures proper AD group relationships and avoids potential issues with permissions, access control, or domain services.
If not addressed: : Unreadable or corrupted Primary Group IDs may indicate AD integrity issues, misconfigurations, or potential tampering, which can lead to access anomalies or security risks. |
| Security and Risk | MITREANSSI |
Found Large Groups | If addressed: Identifying and managing large groups improves visibility, reduces risks of excessive privilege assignments, and enhances auditing and group management performance.
If not addressed: : Unchecked large groups may include unauthorized or dormant members, increasing the attack surface and leading to privilege escalation or unintentional data access. |
| Security and Risk | MITREANSSI |
Found Shadow Admins | If addressed: Identifying and remediating shadow admins-sers with indirect or unintended administrative privileges-educes the risk of privilege escalation and helps enforce the principle of least privilege.
If not addressed: : Shadow admins can silently abuse or escalate privileges, making them prime targets for attackers seeking to move laterally or take control of the domain undetected. |
| Security and Risk | MITREANSSI |
Found Smart Card Authentication Not Enforced for AD Users | If addressed: Enforcing smart card authentication adds an extra layer of security by requiring two-factor authentication, significantly reducing the risk of credential theft or reuse.
If not addressed: : Without smart card enforcement, users can authenticate with only a username and password, increasing exposure to phishing, credential stuffing, and brute-force attacks. |
| Security and Risk | MITREANSSI |
Found Dangerous dsHeuristics Settings | If addressed: Resolving dangerous dsHeuristics settings improves Active Directory (AD) security by restoring secure default behaviors like LDAP signing, anonymous bind restrictions, and proper replication controls.
If not addressed: : Unchecked, these settings can allow weak authentication, enable unauthorized directory access, and expose sensitive domain data to potential attackers. |
| Security and Risk | MITREANSSI |
Found Servers with Remote Desktop Drive Redirection Enabled | If addressed: Disabling RDP drive redirection prevents users from copying sensitive data between local and remote systems, reducing data leakage and malware introduction risks.
If not addressed: : Attackers or unauthorized users can exfiltrate data or introduce malicious files through redirected local drives during RDP sessions, compromising system integrity and data confidentiality. |
| Security and Risk | MITREANSSI |
Found Servers with Remote Desktop Connections Allowed Without Password Prompt | If addressed: Enforcing password prompts for RDP ensures secure authentication, preventing unauthorized access via saved credentials or blank passwords.
If not addressed: : Systems are exposed to credential misuse, allowing attackers or users to gain RDP access without authentication, risking full system compromise. |
| Security and Risk | MITREANSSI |
Found Servers with Microsoft Defender Antivirus SmartScreen Disabled | If addressed: Enabling SmartScreen helps protect servers from phishing sites, malicious downloads, and unsafe apps by providing reputation-based warnings and blocking risky content.
If not addressed: : With SmartScreen disabled, users and processes are more likely to access or execute untrusted content, increasing the risk of malware infections, phishing attacks, and data breaches. |
| Security and Risk | MITREANSSI |
Found Servers with Automatic Sign-in After Restart Enabled | If addressed: Disabling automatic sign-in ensures that servers require manual authentication after restart, reducing the risk of unauthorized access if physical or remote control of the machine is gained.
If not addressed: : Automatic sign-in can expose servers to unauthorized access, allowing anyone with physical or console access to gain control without needing credentials, risking data theft and system compromise. |
| Security and Risk | MITREANSSI |
Found Servers with Backup Rights Assigned to Non-Administrators | If addressed: Restricting backup rights to only trusted administrators minimizes the risk of unauthorized data access, ensuring sensitive system and user data are protected from improper disclosure or tampering.
If not addressed: : Granting backup rights to non-administrators can allow unauthorized users to read and copy sensitive files and system data, potentially leading to data breaches and compliance violations. |
| Security and Risk | MITREANSSI |
Found Servers with Remote Desktop Client Saving Passwords | If addressed: Disabling saved passwords in Remote Desktop clients reduces the risk of credential theft, helping prevent unauthorized access through compromised or stolen machines.
If not addressed: : Saved RDP passwords can be extracted by attackers or malware, enabling lateral movement and unauthorized access to servers without needing to know or guess credentials. |
| Security and Risk | MITREANSSI |
Found Servers with Print Driver Packages Downloaded Over HTTP | If addressed: Enforcing driver downloads over HTTPS ensures print drivers are securely obtained, protecting servers from tampered or malicious drivers and reducing the risk of man-in-the-middle attacks.
If not addressed: : Downloading print drivers over unsecured HTTP exposes servers to potential injection of malicious drivers, which can compromise system integrity or enable privilege escalation. |
| Security and Risk | MITREANSSI |
Found Servers with Internet Printing Enabled | If addressed: Disabling Internet Printing reduces the attack surface by preventing exposure of print services over HTTP, which helps protect servers from remote exploitation and unauthorized print job interception.
If not addressed: : Leaving Internet Printing enabled can expose servers to risks such as unauthorized access, interception of print data, and potential exploitation through vulnerabilities in the Internet Printing Protocol (IPP). |
| Security and Risk | MITREANSSI |
Found Servers with Secure Boot Disabled | If addressed: Enabling Secure Boot ensures only trusted, signed bootloaders and OS kernels run during startup, protecting servers from bootkits, rootkits, and unauthorized firmware-level malware.
If not addressed: : Disabled Secure Boot leaves servers vulnerable to low-level malware infections that can persist across reboots and evade traditional security controls, leading to deep system compromise. |
| Security and Risk | MITREANSSI |
Found Duplicate SamAccountNames | If addressed: Resolving duplicate sAMAccountName values ensures unique user identification within Active Directory, preventing authentication conflicts and access control errors.
If not addressed: : Duplicate sAMAccountName entries can cause login failures, incorrect permission assignments, and security policy misapplication, leading to potential security risks and user access issues. |
| Security and Risk | MITREANSSI |
Found Duplicate UPNs | If addressed: Ensuring unique UPNs prevents login conflicts and guarantees proper user identification across services like Azure AD and Office 365, supporting seamless authentication and access control.
If not addressed: : Duplicate UPNs can cause authentication failures, user confusion, and issues with cloud service integrations, potentially leading to access disruptions and security gaps. |
| Security and Risk | MITREANSSI |
Found Duplicate Emails | If addressed: Ensuring unique email addresses across user accounts helps prevent email delivery issues, misdirected communications, and confusion in identity verification processes.
If not addressed: : Duplicate email addresses can cause email routing errors, data leakage, and authentication problems in systems relying on email for user identification and password recovery. |
| Security and Risk | MITREANSSI |
Found Authenticated Users can create DNS records | If addressed: Restricting DNS record creation to authorized administrators reduces the risk of DNS spoofing, poisoning, and unauthorized service discovery, thus protecting network integrity and security.
If not addressed: : Allowing all authenticated users to create DNS records can lead to malicious or accidental insertion of rogue DNS entries, enabling man-in-the-middle attacks, phishing, and disruption of network services. |
| Security and Risk | MITREANSSI |
Found Historical SIDs on User Accounts | If addressed: Cleaning up historical SIDs (Security Identifiers) from user accounts prevents unauthorized access and ensures accurate permission assignments by removing obsolete or orphaned security references.
If not addressed: : Historical SIDs can cause lingering access rights for deleted or migrated accounts, potentially leading to privilege escalation or unauthorized resource access. |
| Security and Risk | MITREANSSI |
Found Sensitive Group Members with Oldest Password Age | If addressed: Enforcing password changes for sensitive group members reduces the risk of credential compromise due to stale passwords, enhancing overall account security and protecting critical resources.
If not addressed: : Allowing sensitive accounts to retain old passwords increases the likelihood of password guessing, brute-force attacks, or credential theft, potentially leading to unauthorized access and privilege escalation. |
| Security and Risk | MITREANSSI |
Found Admin Accounts with Unprivileged Owners | If addressed: Ensuring that administrative accounts are owned and managed only by privileged, authorized personnel reduces the risk of accidental or malicious misuse and helps maintain strict control over critical account permissions.
If not addressed: : Having unprivileged or unauthorized owners for admin accounts increases the risk of unauthorized changes, privilege abuse, and potential security breaches due to weak oversight or malicious activity. |
| Security and Risk | MITREANSSI |
Found Users With Empty Passwords | If addressed: Removing empty passwords enforces account security by requiring strong authentication, significantly reducing the risk of unauthorized access and compromise.
If not addressed: : Accounts with empty passwords are highly vulnerable to immediate exploitation, allowing attackers easy entry into systems and potentially leading to data breaches or privilege escalation. |
| Security and Risk | MITREANSSI |
Found gMSAs With Passwords Older Than 60 Days | If addressed: Regularly updating Group Managed Service Account (gMSA) passwords enhances security by reducing the risk of credential compromise and ensuring compliance with password rotation policies.
If not addressed: : Stale gMSA passwords increase the likelihood of unauthorized access through credential theft or misuse, potentially leading to service disruptions or security breaches. |
| Security and Risk | MITREANSSI |
Found Users With Passwords Older Than a Year | If addressed: Enforcing regular password changes enhances security by minimizing the risk of compromised credentials being exploited and helps maintain compliance with organizational policies.
If not addressed: : Allowing passwords to age beyond a year increases the chance of unauthorized access due to password cracking, reuse, or leaks, putting systems and data at significant risk. |
| Security and Risk | MITREANSSI |
Found Non-DC Servers with Unconstrained Delegation | If addressed: Removing unconstrained delegation from non-domain controller servers reduces the risk of credential theft and lateral movement attacks, strengthening overall network security.
If not addressed: : Servers with unconstrained delegation can be exploited by attackers to impersonate users and access sensitive resources, potentially leading to full domain compromise. |
| Security and Risk | MITREANSSI |
Found users with Unconstrained Delegation | If addressed: Removing unconstrained delegation from user accounts reduces the risk of attackers impersonating these users to access resources, significantly limiting potential lateral movement and privilege escalation within the network.
If not addressed: : Users with unconstrained delegation can be exploited to impersonate any service, allowing attackers to gain unauthorized access to sensitive systems and potentially compromise the entire domain. |
| Security and Risk | MITREANSSI |
Found Computers with Unconstrained Delegation | If addressed: Removing unconstrained delegation from computer accounts mitigates the risk of attackers abusing these machines to impersonate any user and access sensitive resources, thereby enhancing overall domain security.
If not addressed: : Computers with unconstrained delegation can be exploited to perform unrestricted Kerberos delegation attacks, enabling attackers to move laterally and escalate privileges across the network. |
| Security and Risk | MITREANSSI |
Found Computers with Resource-Based Constrained Delegation | If addressed: Properly managing resource-based constrained delegation ensures that only authorized computers can delegate user credentials to specified services, reducing the risk of unauthorized access and lateral movement attacks.
If not addressed: : Misconfigured or excessive resource-based constrained delegation can allow attackers to impersonate users on sensitive services, leading to privilege escalation and compromise of critical resources. |
| Security and Risk | MITREANSSI |
Found Service Accounts Configured with Constrained Delegation | If addressed: Properly managing constrained delegation on service accounts limits the ability of these accounts to delegate credentials only to specified services, reducing the risk of credential theft and lateral movement.
If not addressed: : Misconfigured or excessive constrained delegation on service accounts can allow attackers to impersonate users on unauthorized services, leading to potential privilege escalation and security breaches. |
| Security and Risk | MITREANSSI |
Found Objects with msds-AllowedToDelegateTo Attribute Populated | If addressed: Properly managing the msDS-AllowedToDelegateTo attribute restricts delegation to specific services only, minimizing the risk of unauthorized credential delegation and reducing attack surface for lateral movement.
If not addressed: : Misuse or over-permission of this attribute can allow attackers to exploit delegation rights, impersonate users, and gain unauthorized access to sensitive services, potentially leading to domain compromise. |
| Security and Risk | MITREANSSI |
Users with Write Access to msDS-AllowedToActOnBehalfOfOtherIdentity on DCs | If addressed: Restricting write access to the msDS-AllowedToActOnBehalfOfOtherIdentity attribute on domain controllers prevents unauthorized users from configuring resource-based delegation, thereby reducing the risk of Kerberos delegation attacks and privilege escalation.
If not addressed: : Users with write permissions to this attribute can grant themselves or others the ability to impersonate any user, potentially leading to full domain compromise through unconstrained delegation abuse. |
| Security and Risk | MITREANSSI |
Users with Write Access to msDS-AllowedToActOnBehalfOfOtherIdentity on krbtgt | If addressed: Restricting write access to the msDS-AllowedToActOnBehalfOfOtherIdentity attribute on the krbtgt account prevents attackers from configuring dangerous delegation permissions, thereby protecting the Kerberos ticket-granting process and maintaining domain security.
If not addressed: : Unauthorized users with write access to this attribute on the krbtgt account can manipulate Kerberos delegation, potentially allowing them to impersonate any user, compromise authentication tokens, and achieve full domain takeover. |
| Security and Risk | MITREANSSI |
Resource-Based Constrained Delegation Enabled for KRBTGT | If addressed: Disabling resource-based constrained delegation on the krbtgt account strengthens domain security by preventing attackers from abusing delegation rights to impersonate any user, thus protecting the Kerberos ticket-granting service from compromise.
If not addressed: : Leaving resource-based constrained delegation enabled on krbtgt exposes the domain to severe security risks, including the possibility of attackers forging Kerberos tickets (Golden Ticket attacks) and gaining unrestricted access to all domain resources. |
| Security and Risk | MITREANSSI |
NSPI Access Enabled | If addressed: Restricting NSPI (Name Service Provider Interface) access reduces the risk of unauthorized enumeration or exposure of Active Directory information, thereby protecting sensitive directory data from potential attackers.
If not addressed: : Unrestricted NSPI access can allow attackers or malicious users to gather detailed information about users, groups, and other directory objects, facilitating reconnaissance and targeted attacks. |
| Security and Risk | MITREANSSI |
Computers Without PowerShell Logging Enabled | If addressed: Enabling PowerShell logging improves visibility into script execution and command usage, aiding in early detection of malicious activities such as script-based attacks or unauthorized changes.
If not addressed: : Without PowerShell logging, malicious or unauthorized PowerShell activities can go unnoticed, increasing the risk of undetected attacks and complicating forensic investigations. |
| Security and Risk | MITREANSSI |
DC Computer Accounts with Unprivileged Owners | If addressed: Ensuring that only privileged and trusted administrators own Domain Controller (DC) computer accounts helps prevent unauthorized changes, enhancing the security and integrity of critical DC objects.
If not addressed: : If unprivileged users own DC computer accounts, they may modify sensitive attributes or permissions, potentially leading to privilege escalation, unauthorized access, or domain compromise. |
| Security and Risk | MITREANSSI |
Foreign Security Principals in Administrative Groups | If addressed: Removing or properly managing foreign security principals (FSPs) in administrative groups prevents unauthorized access from external trusted domains, strengthening security by limiting admin privileges to only trusted accounts.
If not addressed: : Presence of FSPs in admin groups can allow users from external or untrusted domains to gain administrative rights, increasing the risk of privilege escalation and potential domain compromise. |
| Security and Risk | MITREANSSI |
Outbound Trust with SID History Enabled | If addressed: Disabling or properly managing SID history in outbound trusts reduces the risk of privilege abuse and unauthorized access, ensuring that only valid and current security identifiers are used for access control.
If not addressed: : Leaving SID history enabled on outbound trusts can allow attackers to exploit legacy permissions, potentially gaining unauthorized access or elevating privileges across trusted domains. |
| Security and Risk | MITREANSSI |
Ensure SDProp Process is Enabled for Critical Groups | If addressed: Enabling the SDProp (Security Descriptor Propagator) process for critical groups ensures that security permissions are consistently and correctly propagated, maintaining group security integrity and reducing permission misconfigurations.
If not addressed: : Without SDProp enabled, critical groups may have inconsistent or outdated permissions, leading to potential unauthorized access, privilege escalation, or security gaps in Active Directory. |
| Security and Risk | MITREANSSI |
Found Computers with SERVER_TRUST_ACCOUNT Enabled | If addressed: Properly managing computers with the SERVER_TRUST_ACCOUNT flag ensures secure trust relationships between domains, reducing the risk of unauthorized access through compromised or misconfigured server accounts.
If not addressed: : Leaving unnecessary or unmanaged SERVER_TRUST_ACCOUNT flags enabled can expose the environment to trust exploitation attacks, allowing attackers to impersonate trusted servers and escalate privileges across domain boundaries. |
| Security and Risk | MITREANSSI |
Found Users using smart card with unchanged password for a long time | If addressed: Enforcing regular password changes for smart card users reduces the risk of credential compromise, ensuring strong multi-factor authentication and minimizing the chances of unauthorized access.
If not addressed: : Allowing long-standing unchanged passwords alongside smart card usage can weaken overall account security, increasing vulnerability to attacks like credential theft or replay attacks despite the smart card protection. |
| Security and Risk | MITREANSSI |
Users with AD Replication Permissions | If addressed: Enforcing regular password changes alongside smart card authentication strengthens security by ensuring credentials remain fresh, reducing the risk of credential theft or misuse despite the added layer of smart card protection.
If not addressed: : Allowing passwords to remain unchanged for extended periods, even with smart card use, increases vulnerability to attacks such as password guessing, replay, or theft, potentially compromising accounts despite multi-factor authentication. |
| Security and Risk | MITREANSSI |
Domain Controllers vulnerable to MS17-010 | If addressed: Patching MS17-010 vulnerability on Domain Controllers protects the network from critical exploits like EternalBlue, preventing ransomware attacks (e.g., WannaCry) and unauthorized remote code execution that could compromise the entire domain.
If not addressed: : Unpatched Domain Controllers remain highly susceptible to devastating attacks, enabling attackers to gain control over domain infrastructure, steal data, disrupt services, and propagate malware rapidly across the network. |
| Security and Risk | MITREANSSI |
Domain Controllers vulnerable to MS17-010-Patch Status | If addressed: Patching MS17-010 vulnerability on Domain Controllers protects the network from critical exploits like EternalBlue, preventing ransomware attacks (e.g., WannaCry) and unauthorized remote code execution that could compromise the entire domain.
If not addressed: : Unpatched Domain Controllers remain highly susceptible to devastating attacks, enabling attackers to gain control over domain infrastructure, steal data, disrupt services, and propagate malware rapidly across the network. |
| Security and Risk | MITREANSSI |
Domain Controllers vulnerable to MS14-068 | If addressed: Applying the MS14-068 patch protects Domain Controllers from a critical Kerberos elevation of privilege vulnerability, preventing attackers from forging Kerberos tickets to gain unauthorized domain admin rights.
If not addressed: : Unpatched Domain Controllers remain vulnerable to attackers exploiting the flaw to elevate privileges, potentially leading to full domain compromise and persistent unauthorized access. |
| Security and Risk | MITREANSSI |
Certificate Templates Editable by Everyone | If addressed: Restricting edit permissions on certificate templates prevents unauthorized users from issuing rogue certificates, thereby protecting the organization’s PKI integrity and reducing risks like impersonation and man-in-the-middle attacks.
If not addressed: : If certificate templates are editable by everyone, attackers can abuse this to create fraudulent certificates, potentially leading to unauthorized access, data interception, or compromise of secure communications. |
| Security and Risk | MITREANSSI |
Trusts SID Filtering Check | If addressed: Enabling and properly configuring SID filtering on trusts prevents unauthorized access by blocking the use of malicious or forged SIDs, thereby protecting the integrity of cross-domain authentication and resource access.
If not addressed: : Without SID filtering, attackers can exploit trust relationships by injecting harmful SIDs through token manipulation, potentially gaining unauthorized access to resources in trusted domains. |
| Security and Risk | MITREANSSI |
Unauhtorized Conditional Forwarders Found |