SmartProfiler for Active Directory now ships with Domain Controllers Security Analyzer – a tool designed to check domain controller security configuration. There are 11 Strategies for Securing Domain Controllers explained in this article. All domain controllers in an Active Directory environment need to be configured with standard configuration and they are protected by disabling some protocols and applying necessary Group Policy Settings. In this article we explain how to improve security posture of Domain Controllers by disabling unnecessary protocols, configuring encryption protocols, making sure unnecessary roles and features are not installed, and so on.
SmartProfiler for Active Directory conducts over 50 specialized tests tailored for domain controllers. These tests encompass a spectrum of assessments, ranging from scrutinizing security configurations to identifying potential misconfigurations. The tool offers a comprehensive list of tests it can perform against each domain controller, providing invaluable insights into the security posture of the entire Active Directory environment.
Here is a list of top Domain Controllers security configuration to check in an Active Directory environment:
As the test title suggests, the test checks to ensure all of the domain controllers have SMB 1 protocol disabled. The SMB 1 protocol is a security risk. Server Message Block (SMB) is a critical component for any Microsoft oriented networking environment. That’s why hardening SMB is one of the critical steps in securing Active Directory Domain Controllers. Disabling SMBv1 on Active Directory Domain Controllers improves the security posture of your Active Directory environment. It is recommended to disable SMB1 protocol on all affected domain controllers. SmartProfiler for Active Directory security assessment highlights the list of domain controllers that need to be disabled with SMB 1.
Ensure AllowNT4Crypto setting on all Domain Controllers is disabled. Allowing old NT4 cryptography algorithms could be a serious security risk on Domain Controllers, and could be a signal that in the environment there might still be very old and unsecure hardware or software being used (like NT4 or older SAMBA SMB clients). Besides, all currently supported Operating System don’t even honor this setting anymore. Recommended action is to disable NT4 Crypto on affected domain controllers. To disable NT4 Crypto, In Registry Editor navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters and change the value of AllowNT4Crypto to 0. SmartProfiler for Active Directory security assessment highlights the list of domain controllers that need to be disabled with AllowNT4Crypto.
Ensure LAN Manager password hashes are not stored on Domain Controllers. The LAN Manager hash is relatively weak and prone to attack compared to the cryptographically stronger NTLM hash. Because the LM hash is stored on the local device in the security database, the passwords can be compromised if the security database, Security Accounts Manager (SAM), is attacked. We need to ensure all domain controllers have LAN Manager Password hashes disabled. SmartProfiler
Ensure SMB Signing is Enabled on Domain Controllers. Unsigned network traffic is susceptible to attacks abusing the NTLM challenge-response protocol. A common example of such attacks is SMB Relay, where an attacker is positioned between the client and the server to capture data packets transmitted between the two, thus gaining unauthorized access to the server or other servers on the network.
Ensure TLS 1.1 protocol is disabled on Domain Controllers. Modern cyber-attacks methods often make specific use of legacy protocols in their attack and often utilize them to target organizations that have yet to implement the proper mitigation. To retire the use of legacy protocols, your organization must first discover which internal entities and applications rely on them. Recommendation is to disabled TLS 1.1 protocol on all affected domain controllers by applying a registry fix or using Default Domain Controllers GPO.
Ensure NTLMv1 Authentication is disabled on Domain Controllers. NTLM and NTLMv2 authentication is vulnerable to various malicious attacks, including SMB replay, man-in-the-middle attacks, and brute force attacks. Reducing and eliminating NTLM authentication from your environment forces the Windows operating system to use more secure protocols, such as the Kerberos version 5 protocol, or different authentication mechanisms, such as smart cards. The main risk of disabling NTLM is the potential usage of legacy or incorrectly configured applications that can still use NTLM authentication.
It is recommended to disable NTLM Protocol on domain controllers by using the registry or GPO. Edit the Default Domain Policy, go to the GPO section Computer Configurations, Select Policies, and then take, security Setting from Windows Settings, then choose Local Policies -> Security Options, and find the policy Network Security: LAN Manager authentication level. Configure Send LM & NTLM responses to use NTLMv2 session security if negotiated to apply settings to all domain controllers.
Enabling RC4 encrypted Kerberos tickets inadvertently exposes passwords to cracking speeds over 900 times faster than AES encrypted counterparts. Many environments unintentionally retain this vulnerability due to default configurations allowing RC4 downgrading. This undefined setting heightens the risk, enabling threat actors to crack passwords with alarming speed. From a security standpoint, disabling RC4 encryption for Kerberos Tickets is imperative to thwart attackers from effortlessly obtaining password hashes. SmartProfiler for Active Directory can delve deeper, uncovering instances where Service Principal Names (SPNs) assigned to accounts default to RC4 authentication method, further emphasizing the need for action.
Make sure that Domain Controller Objects remain unaltered in terms of their PrimaryGroupID attribute. Altering the Primary Group ID represents a covert method for attackers to elevate privileges without activating member attribute auditing for group membership alterations. It’s advisable to inspect the impacted domain controllers and restore the primaryGroupID to its original state.
Verify that Domain Controllers remain in a consistent state, as inconsistencies may arise from manual or software-induced misconfigurations, potentially indicating malicious activity. All writable domain controllers within the Active Directory (AD) Forest should maintain UserAccountControl set to 532480, alongside the existence of an NTDS Object for AD Replication. Any presence of unauthorized machines masquerading as Domain Controllers signals a compromised environment. Even partially functional legitimate Domain Controllers pose security risks if compromised, warranting thorough inspection and remediation measures.
Ensure Domain Controllers Have renewed their secrets within 45 days. If some domain controllers have not changed their password for more than 45 days, indicating their secrets are not renewed. All domain controllers must renew their secrets every 30 days. Default domain controller settings have them change their passwords automatically every 30 days. The reason for this change not occurring properly must be investigated as it may be indicative of a compromise.
First, check the following registry values – HKLM\System\CurrentControlSet\Services\Netlogon\Parameters\DisablePasswordChange: must be set to 0 or inexistent and HKLM\System\CurrentControlSet\Services\Netlogon\Parameters\MaximumPasswordAge: must be set to 30. Incorrect values should be reset to their default setting, and GPOs must be checked to ensure they do not override those.
All Open Shares other than the default shares must be removed from domain controllers. Domain controllers automatically generate several default shares upon installation, including IPC$, C$, and ADMIN$. The IPC$ share serves as a mechanism for inter-process communication, facilitating remote administration tasks such as connecting to shared resources and managing network devices. The C$ share provides administrative access to the root of the system drive on the domain controller, allowing administrators to remotely access and manage files and directories. Similarly, the ADMIN$ share grants administrative access to the Windows directory on the domain controller. While these default shares streamline administrative tasks and facilitate remote management, they also pose potential security risks if not properly secured. Administrators must implement access controls and adhere to best practices to mitigate the risk of unauthorized access and maintain the integrity of the domain controller environment.
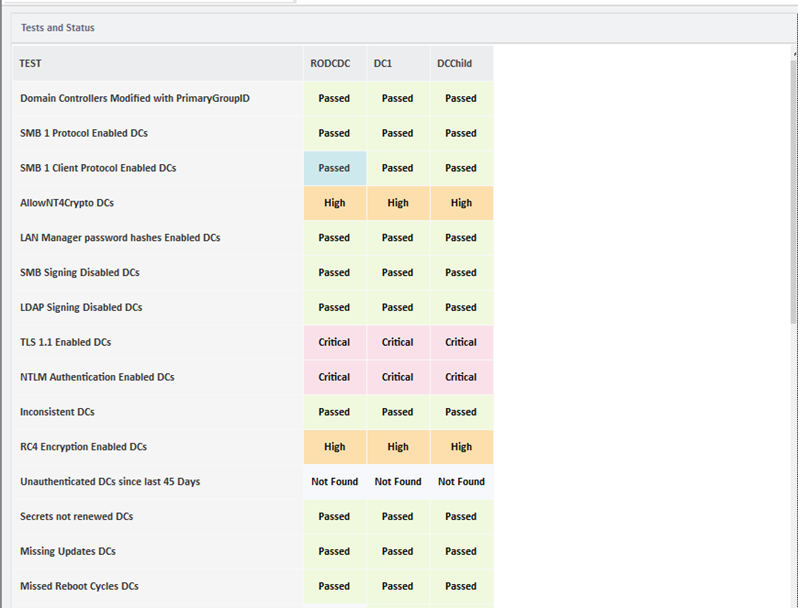
SmartProfiler for Active Directory Security assessment features the “DC SEC ANALYZER” module, designed for verifying the status of each domain controller against the security configurations outlined in this article. Upon accessing the DC SEC ANALYZER, users can view a comprehensive list of tests and the corresponding status for each domain controller, displayed as depicted in the screenshot below:
Note: All of the tests shown as part of the DC SEC ANALYZER are recommended by ANSSI, MITRE, and Microsoft.

Try SmartProfiler, a unified tool to help with security evaluation across many Microsoft technologies.