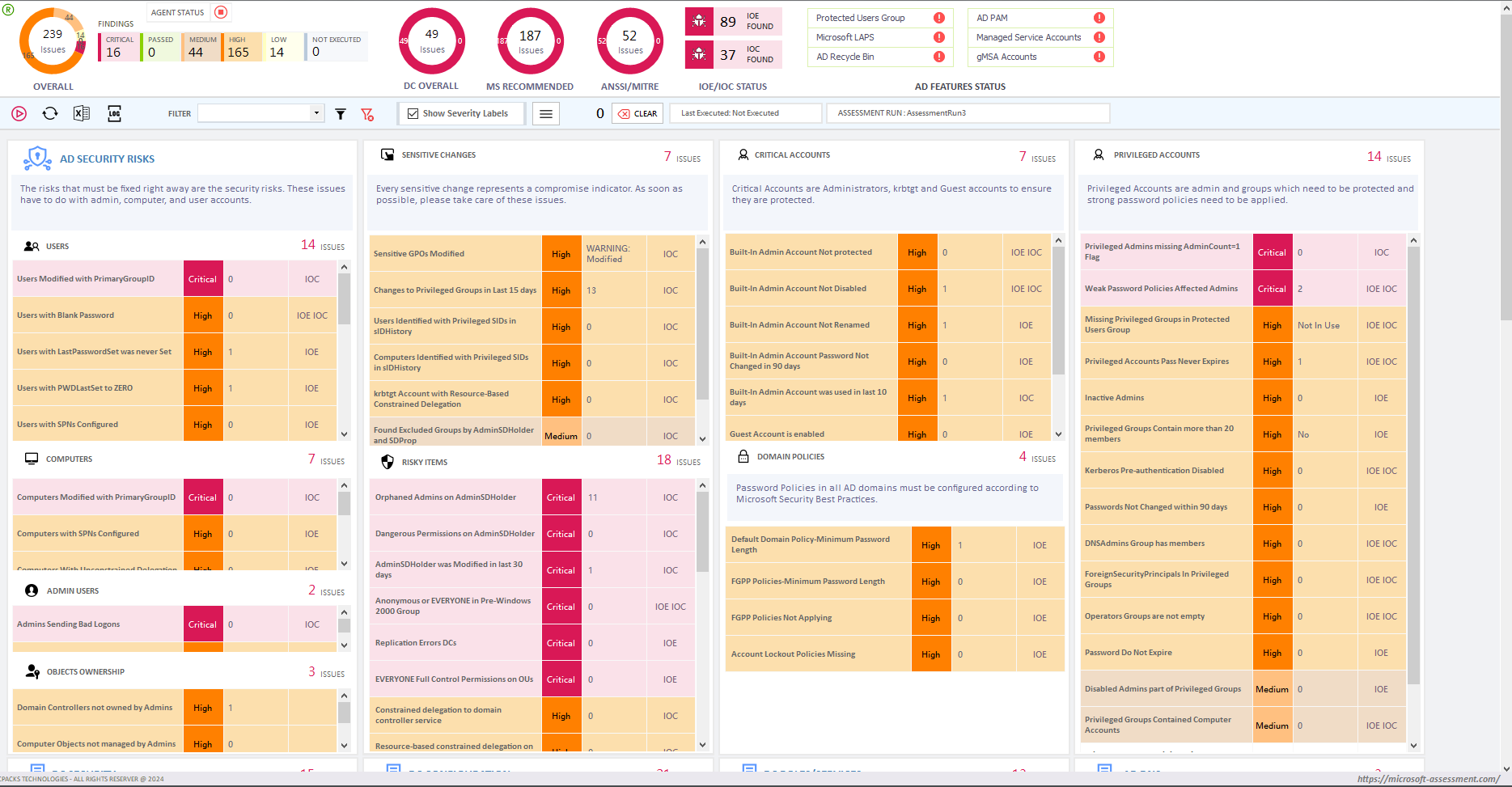
Complete Active Directory Security Assessment
In this article we define a how to perform Complete Active Directory Security Assessment for an Active Directory system, and do you actually have the expertise reviewing Active Directory beyond using the default criteria that come with an Active Directory assessment tool? Complete Active Directory Security Assessment: Why Attackers are more interested in breaking into
Read More