SmartProfiler for Active Directory now ships with DC SEC ANALYZER – a tool designed to check domain controller misconfiguration. All domain controllers in an Active Directory environment need to be configured with standard configuration settings. In previous post, here, we explained recommended security settings to be configured on the domain controllers. In this article we explain how to improve configuration of Domain Controllers by configuring recommended settings by Microsoft, MITRE, ANSSI and other organizations.
A very TRUE statement: Before investing in any Microsoft Active Directory monitoring software, it’s imperative to do an advanced assessment of your Active Directory to ensure that the monitoring software can monitor and address any issues the assessment tool uncovers.
SmartProfiler for Active Directory conducts over 50 specialized tests developed for domain controllers. These tests encompass a range of assessments, ranging from scrutinizing security configurations to identifying potential misconfigurations. The tool offers a comprehensive list of tests it can perform against each domain controller, providing invaluable insights into the security posture of the entire Active Directory environment.
Here is a list of top Domain Controllers misconfiguration to avoid in an Active Directory environment:
Ensure DNS Server Level Scavenging is Configured on Domain Controllers. Disabling Scavenging might result in a huge number of stale DNS Entries. Note that if all your Domain Zones are AD Integrated it is recommended to keep Scavenging enabled only on one DNS Server.
Ensure Domain Controllers are in Default OU. Domain Controller Default GPO might not be applying to domain controllers located outside Domain Controllers OU. Domain controllers pull some security settings only from group policy objects linked to the root of the domain. Because domain controllers share the same account database for the domain, certain security settings must be set uniformly on all domain controllers. Please make sure to move domain controllers back to Domain Controllers OU. The domain controller gathers the list of group policy objects by searching the parent containers of the domain controller’s Computer object. The domain controller applies the settings listed earlier only if the group policy object is linked to the Domain container.
Ensure that domain controllers have enough DNS servers specified in their network card properties to ensure reliable DNS resolution. Any domain controller that has only one DNS Server configured as a forwarded might fail resolutions for client and other devices if the configured DNS Server is not responding or down.
Ensure NIC on Domain Controllers Have DNS Dynamic Update Configured. If Domain Controllers have Dynamic DNS Registration disabled for active NICs, Domain Controllers cannot update records in DNS Servers automatically. Please ensure Dynamic DNS Registration is enabled. Disabling Dynamic DNS Registration will disable the ability for domain controller to register its resource records dynamically to DNS Servers.
Ensure unnecessary Scheduled Tasks are removed or disabled on Domain Controllers. Scheduled tasks have been known to be exploited to allow attackers to elevate privileges, gain persistence and download and deploy malware. This finding indicates that scheduled tasks were found on the Domain Controllers within the domain queried. Review scheduled tasks listed in test for legitimacy and validate that they are needed. Remove any unneeded unnecessary tasks.
Ensure Enough DNS Servers are configured on Domain Controller NIC. All Domain Controllers must be configured with two or more DNS Servers in TCP/IP Property of network card. Domain Controllers will not be able to reach other DNS Servers for DNS lookups. Configuring enough DNS Servers will ensure a DNS Query can be resolved. Please check affected domain controllers object in the DC SEC ANALYZER and check which Domain Controller requires updating with DNS configuration. It is recommended to configure domain controllers with at least 2 DNS Servers.
Strict Replication Consistency is a registry value that prevents destination domain controllers (DC) from replicating in lingering objects. Lingering objects are objects that deleted from DC, but replication failures prevent a partner DC learning of the deletion. The result is those deleted objects remain Active on the replication partners. If the replication failure persists for longer than tombstone lifetime but is later corrected, the DC that failed to inbound replicate the deletions will continue to have lingering objects in its copy of the AD database. When one or more attributes are modified on these live objects, that object must replicate outbound. DCs that don’t have Strict Replication Consistency enforced will replicate in these formerly deleted objects, re-animating them. It is recommended to enable Strict Replication Consistency on all affected domain controllers by modifying the registry entry at HKLM\SYSTEM\CurrentControlSet\Services\NTDS\Parameters and then creating Strict Replication Consistency. Set the value of Strict Replication Consistency to 1.
Ensure Domain Controllers are not using NTFRS for AD Replication. Some domain controllers are configured to use the NTFRS protocol to replicate the SYSVOL file share. This protocol is obsolete and exposes unnecessary additional administration interfaces to domain controllers. Furthermore, latest Windows Server versions have dropped support of NTFRS altogether, blocking upgrades for existing infrastructures pending migration to DFSR. Please note support for NTFRS has been dropped in latest Windows Server versions. Please ensure all domain controllers are using DSFR for AD Replication.
Ensure Domain Controllers have SSL Authentication Enabled. It is a security risk. All clients must be authenticated via a secure channel. Please review the list provided in the DC SEC ANALYZER and make sure to configure Domain Controllers with SSL.
Ensure Domain Controllers DNS Loopback Address Configured. Some Domain Controllers do not have Loopback Address configured is reported by the DC SEC ANALYZER which may result in delay in loading DNS Zone database. It is recommended to configure 127.0.0.1 as DNS Server on each domain controller to avoid delay in loading DNS Zone database.
Ensure Domain Controller Local Disks are configured as per Microsoft. Disks on Domain Controllers configured as per Active Directory best practices. Domain Controllers will result in performance issues if enough local disks are not configured. As per best practices, domain controllers file must be hosted on separate volumes to avoid any performance issues. For example, SYSVOL to be hosted on a separate disk – Active Directory Logs to be hosted on another disk and so on.
Unnecessary roles/features on Domain Controllers increase the attack surface. Some of these services may not support required levels of authentication or encryption or may provide unauthorized access to the system. For example, the below roles/features must not be running on the domain controllers:
Make sure that the Domain Controllers’ Print Spooler Service is turned off. In order to exploit Domain Controllers, CVE-2021-1675 is weaponized. A zero-day vulnerability event is actually already occurring in the real world as a result of this. Fortunately, turning down the Print Spooler service on Domain Controllers is an easy way to circumvent the vulnerability. By default, print spooler services are turned on. Disable the service on each domain controller if it’s not absolutely necessary. Make sure the server is completely patched if necessary, then adhere to Microsoft’s instructions here. Update-guide: https://msrc.microsoft.com/vulnerability/CVE-2021-34527.
Ensure Active Directory Web Services (ADWS) to start automatically on All Domain Controllers. The ADWS provides a Web Service interface to instances of the directory service (AD DS and AD LDS) that are running locally on this server. If the service is stopped or disabled, client applications, such as Active Directory PowerShell, will not be able to access or manage any directory service instances that are running locally on the server. Recommendation step is to set ADWS Service to start automatically in Services.msc snap-in.
Ensure DHCP Server Service is disabled on Domain Controllers. The DHCP Server service performs TCP/IP configuration for DHCP clients, including dynamic assignments of IP addresses, specification of DNS servers, and connection-specific DNS names. Domain controllers do not require the DHCP Server service to operate and for higher security and server hardening it is recommended not to install the DHCP Server role on domain controllers. Domain controllers do not require the DHCP Server service to operate and for higher security and server hardening, it is recommended not to install the DHCP Server role on domain controllers, but to install the DHCP Server role on member servers instead.
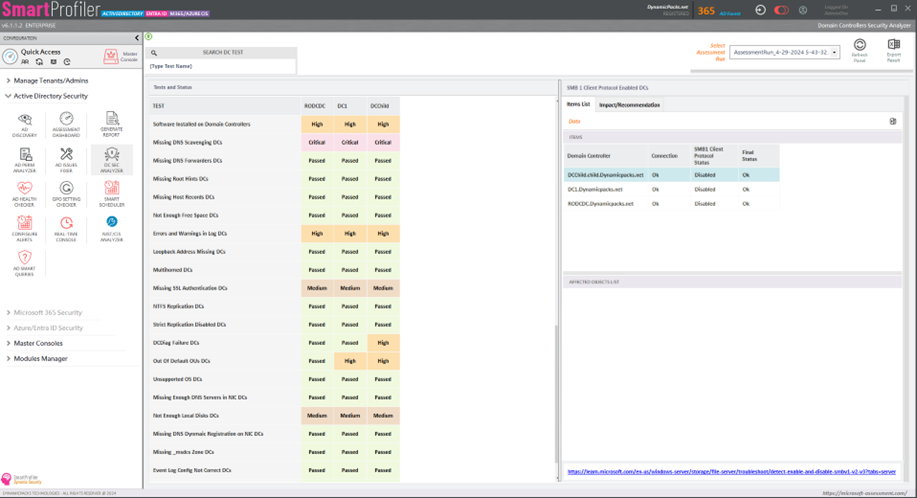
SmartProfiler for Active Directory Security assessment features the “DC SEC ANALYZER” module, designed for verifying the status of each domain controller against the security configurations outlined in this article. Upon accessing the DC SEC ANALYZER, users can view a comprehensive list of tests and the corresponding status for each domain controller, displayed as depicted in the screenshot below:
Microsoft provides a list of articles to address these misconfiguration in details here.

Try SmartProfiler, a unified tool to help with security evaluation across many Microsoft technologies.