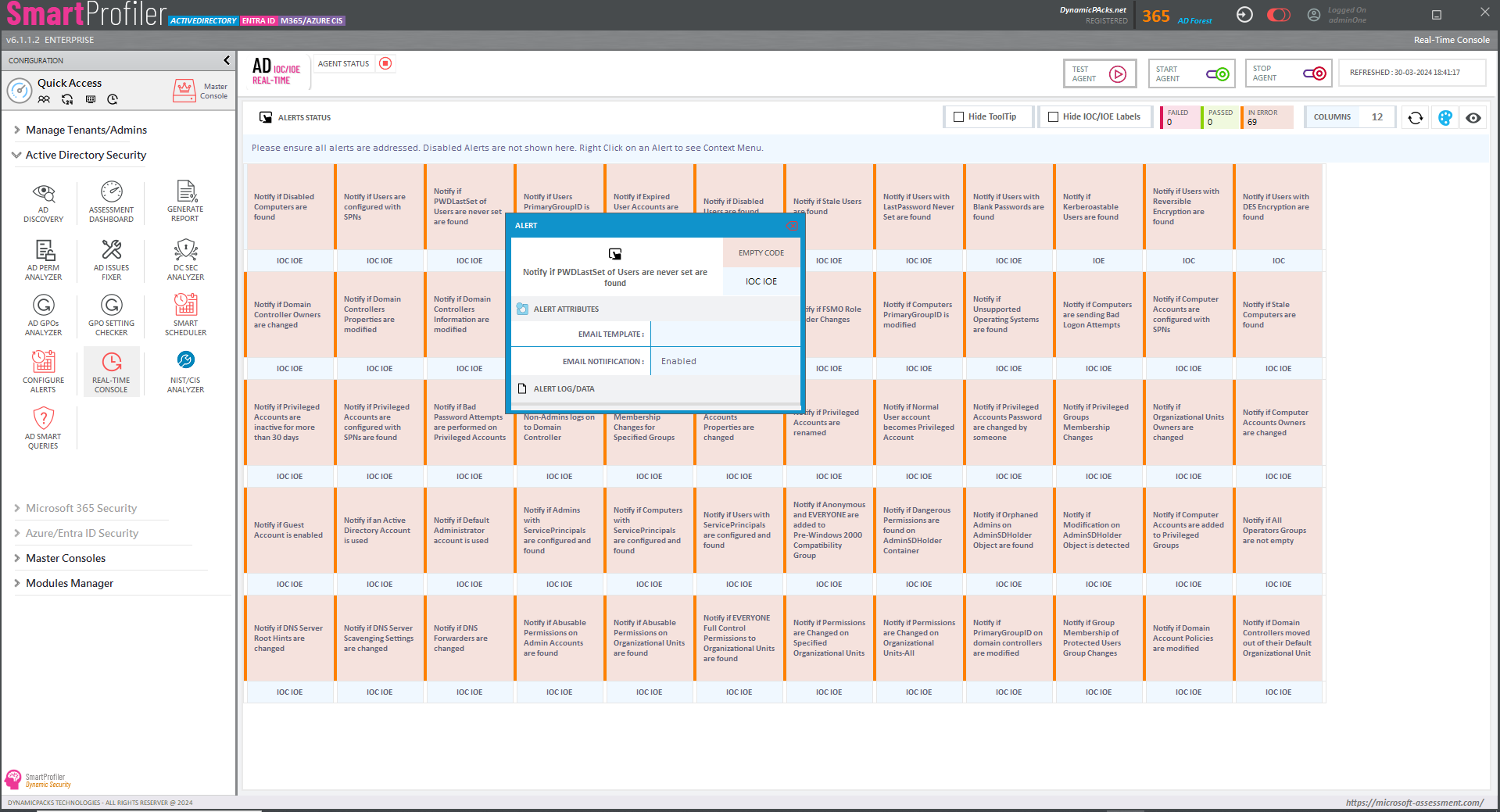
Active Directory (AD) serves as the backbone of network management, enabling organizations to effectively manage user accounts, permissions, and resources. A healthy and secure AD environment is vital for ensuring smooth operations, data integrity, and safeguarding against security breaches. In this article, we will delve into the importance of maintaining a healthy and secure Active Directory environment and explore various techniques for assessing and addressing health and security issues. Reporting Health and Security Issues in Active Directory is a challenging job. However, SmartProfiler for Active Directory can uncover all issues in your Active Directory environment.
Active Directory health refers to the overall state of the AD environment, encompassing factors such as replication, DNS configuration, global catalog functionality, and database integrity. A healthy AD environment ensures efficient authentication, timely replication of data, and reliable access to resources. By monitoring and conducting regular health checks, organizations can identify and resolve potential issues, thereby maintaining optimal network performance.
DNS misconfiguration is another prevalent health issue in AD environments. Improper DNS configuration can disrupt authentication processes and result in difficulties locating domain resources. Best practices for DNS configuration include ensuring correct DNS server settings, proper delegation, and avoiding common pitfalls like split-brain DNS. Regularly monitoring and maintaining DNS infrastructure is crucial for a healthy AD environment.
The global catalog, a distributed data repository that facilitates faster searches and universal group membership, can also encounter issues. Common problems include failure of the global catalog server or replication issues affecting the global catalog partition. Troubleshooting global catalog problems involves verifying server availability, resolving replication issues, and ensuring proper partitioning.
AD database corruption is a critical health issue that can lead to data inconsistencies and authentication failures. Signs of database corruption may include replication failures, user authentication issues, or errors while accessing directory services. To repair a corrupted AD database, organizations can utilize tools like the ntdsutil command-line utility or third-party recovery tools, following appropriate guidelines and best practices.
Assessing Active Directory Security
In addition to AD health, maintaining a secure environment is crucial for protecting sensitive data and preventing unauthorized access. Active Directory holds valuable information, making it an attractive target for attackers. Evaluating the security posture of an AD deployment is essential to identify vulnerabilities and implement necessary safeguards.
One of the common security issues in AD is weak password policies. Weak passwords make AD environments vulnerable to brute-force attacks and unauthorized access. Implementing strong password policies and enforcing their usage, including requirements for complexity and regular password changes, is vital to mitigate these risks.
Privilege escalation attacks, where unauthorized users gain excessive privileges, can lead to data breaches and compromise network security. Preventing privilege escalation involves implementing the principle of least privilege, regularly reviewing and adjusting permissions, and monitoring privileged accounts for suspicious activities.
Unauthorized access attempts pose a significant threat to AD security. Organizations must implement effective access controls and monitoring mechanisms to detect and prevent unauthorized access to AD resources. This includes utilizing techniques like two-factor authentication, implementing proper network segmentation, and regularly reviewing access control lists.
Misconfigurations in Group Policies can inadvertently grant unauthorized permissions or expose sensitive settings, making it crucial to follow best practices for securing Group Policy objects. Organizations should regularly review and audit Group Policies, ensure secure baseline configurations, and utilize tools like Group Policy Management Console (GPMC) to enforce security settings consistently.
Active Directory Auditing and Monitoring
Auditing and monitoring play a crucial role in maintaining a secure AD environment. By implementing comprehensive auditing practices, organizations can track user activities, detect security incidents, and meet compliance requirements. Various tools and techniques are available for auditing and monitoring Active Directory, allowing organizations to proactively identify and respond to security threats.
Active Directory auditing involves capturing and analyzing event logs to track user activities, such as login attempts, changes to user accounts, or modifications to security settings. By enabling auditing policies and configuring the appropriate audit settings, organizations can generate audit logs that provide valuable information for security analysis and incident response.
Monitoring Active Directory involves real-time observation of events and activities within the AD environment. This includes monitoring authentication attempts, privilege escalation activities, and suspicious behavior that may indicate a security breach. Various monitoring solutions and tools, such as SIEM (Security Information and Event Management) systems and specialized AD monitoring software, can help organizations effectively monitor their AD environment.
By combining auditing and monitoring practices, organizations can gain visibility into their AD environment and quickly detect and respond to security incidents. Timely identification of potential threats allows for proactive mitigation measures, minimizing the impact of security breaches and ensuring the integrity and confidentiality of AD resources.
Active Directory Health and Security Best Practices
To maintain a healthy and secure AD environment, organizations should adhere to best practices. These practices include:
Maintaining a healthy and secure Active Directory environment is crucial for organizations. By understanding the indicators of AD health, diagnosing common issues, and implementing appropriate resolution strategies, organizations can ensure optimal network performance. Evaluating AD security posture, addressing common security vulnerabilities, and implementing auditing and monitoring practices enable organizations to safeguard against threats. By following best practices and prioritizing AD health and security, organizations can effectively protect their network infrastructure, data, and resources, ensuring the overall success and stability of their IT environment. With continuous efforts to maintain AD health and security, organizations can mitigate risks, enhance operational efficiency, and protect their valuable assets.
Looking to assess the health and security of your Active Directory environment? Microsoft-Assessment.com offers free Active Directory Security Assessment and AD Health and Security Assessment services. With SmartProfiler Active Directory, we diagnose and resolve issues like replication problems, DNS misconfigurations, and database corruption. Our expert team also evaluates your AD security posture and helps you implement best practices. Experience active monitoring, auditing, and protection for your AD environment. Visit Microsoft-Assessment.com today for a comprehensive AD assessment.
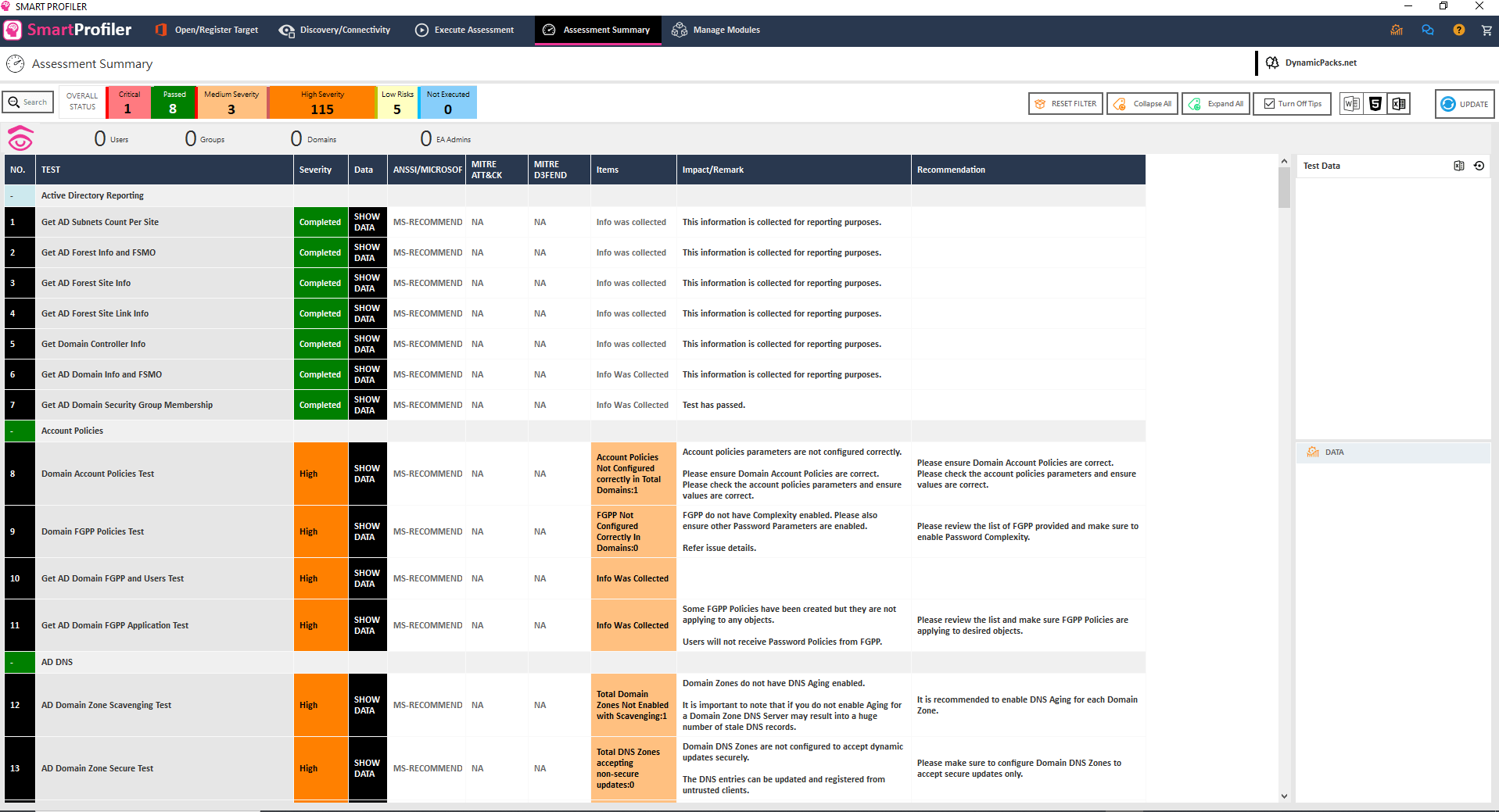
SmartProfiler can quickly perform a health and security assessment of multiple Active Directory forests and generate an actionable report.
Try SmartProfiler, a unified tool to help with security evaluation across many Microsoft technologies.