The CIS/NIST Analyzer is designed to check CIS recommended GPO Settings in an Active Directory Domain. Currently, NIST/CIS Analyzer supports below templates. These templates are well-defined and written by CIS experts. However, there is no any automated way to check GPO settings defined in below templates.
Checking Group Policy Object settings in Active Directory can ensure consistent and secure configuration across your Active Directory environment. GPOs enable you to enforce consistent settings, such as security policies, desktop configurations, and software deployment, across all computers in the Active Directory. By regularly checking GPO settings, administrators can ensure that these configurations remain uniform and aligned with your organizational standards. Analyzing GPO settings is also important for security compliance.
To open the NIST/CIS Analyzer, please click on “NIS/CIS ANALYZER” button in the left pane. By default, there will be no templates. You will need to create a template.
To create a template, click on “Create New Template” button on the action bar, which, in turn, will show below screen:
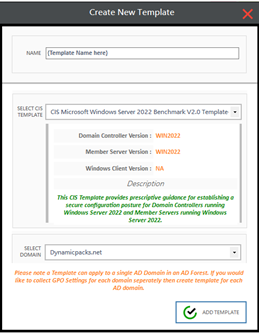
In the “Create New Template” screen, provide following inputs:
Once done, click on the “Add Template” button to add the template.
Once the template has been created, from the “Select Template” dropdown, select the template and then click on the “Open Template” button.
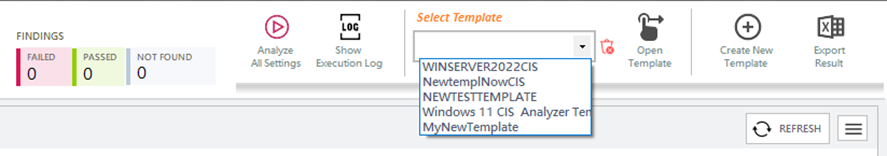
The Template will open with all the settings defined in it.
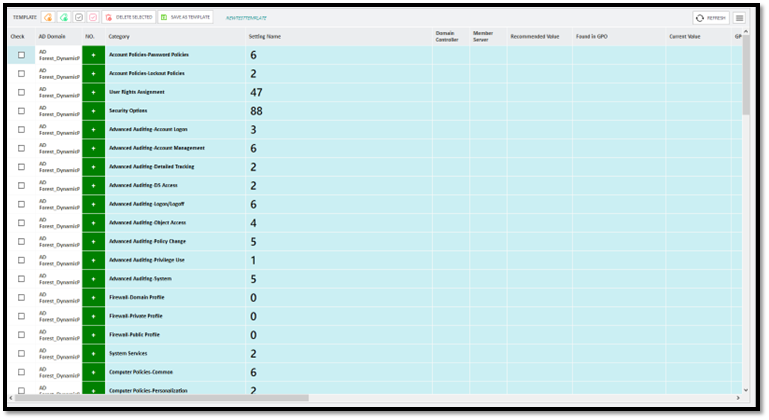
Once the Template has been opened, you can click on “Analyze All Settings” button on the action bar to start checking all GPO Settings defined in the template in the selected AD domain. Once the process has been completed, the template will refresh, and you can see the status of each setting.
You can also create a custom template using CIS/NIST Analyzer. The idea is to ensure settings that you define are checked in the AD environment by CIS/NIST Analyzer. Please note that a custom template can be created from a pre-defined CIS Template. To create a custom template, open an existing template and then delete the settings and section that you do not wish to include as part of the template. For example, in currently opened template, we selected three settings that we do not wish to include in the template.
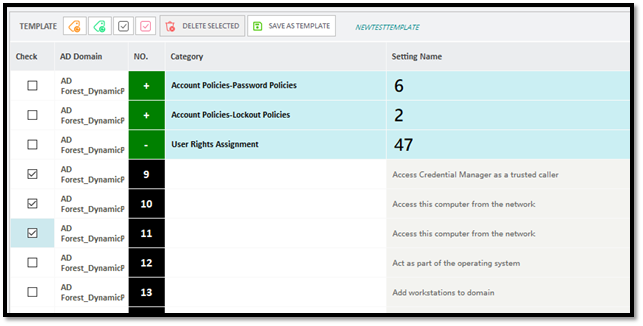
After selecting settings click on “Delete Selected” button to delete the settings from the template. Once you have deleted the not required settings, click on “Save As Template” button.
In the “Copy Current Template As” window, please provide following inputs:
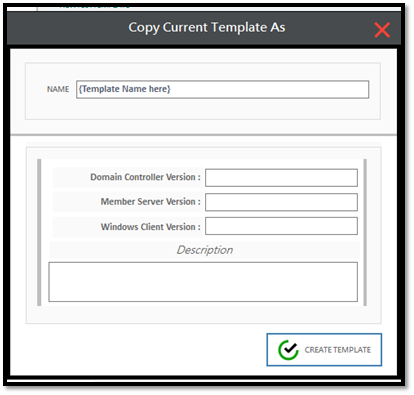
Once done, click on “Create Template” button to create the template. Once the template has been created you can open the template and then analyze the settings which are part of the template.
There are several attributes as part of a template. These attributes are explained below:
SmartProfiler CIS/NIST Analyzer can check all GPO settings recommended by CIS. It is also worth noting that CIS/NIST Analyzer result can be exported to an excel sheet for easy reviewing.
Try SmartProfiler, a unified tool to help with security evaluation across many Microsoft technologies.