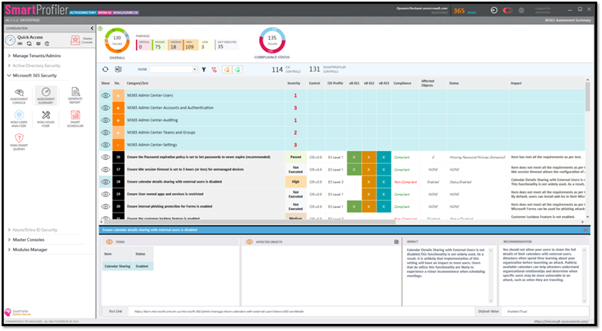
SmartProfiler M365 CIS Assessment
Allows you to run assessment for single Microsoft 365 Tenant.
- 234 Microsoft 365 Tests recommended by CIS, NIST and other security organizations.
- Quick Assessment
- Assessment Dashboard
- Assessment Summary
- Explore Microsoft 365 Tests
- Explore Assessment Requirements
- Generate Reports
Execution Steps can be found here.