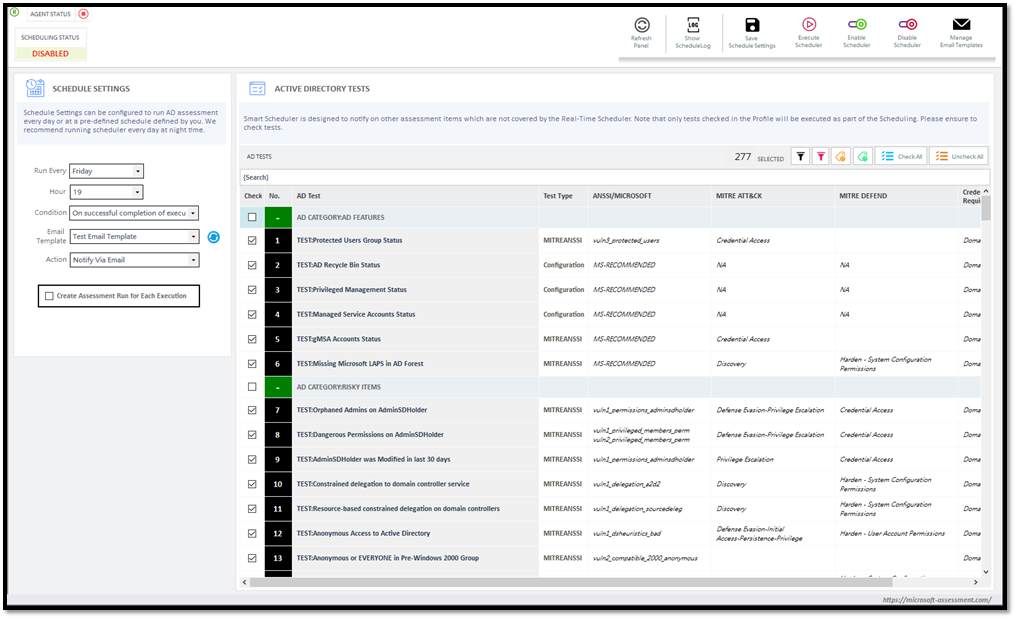
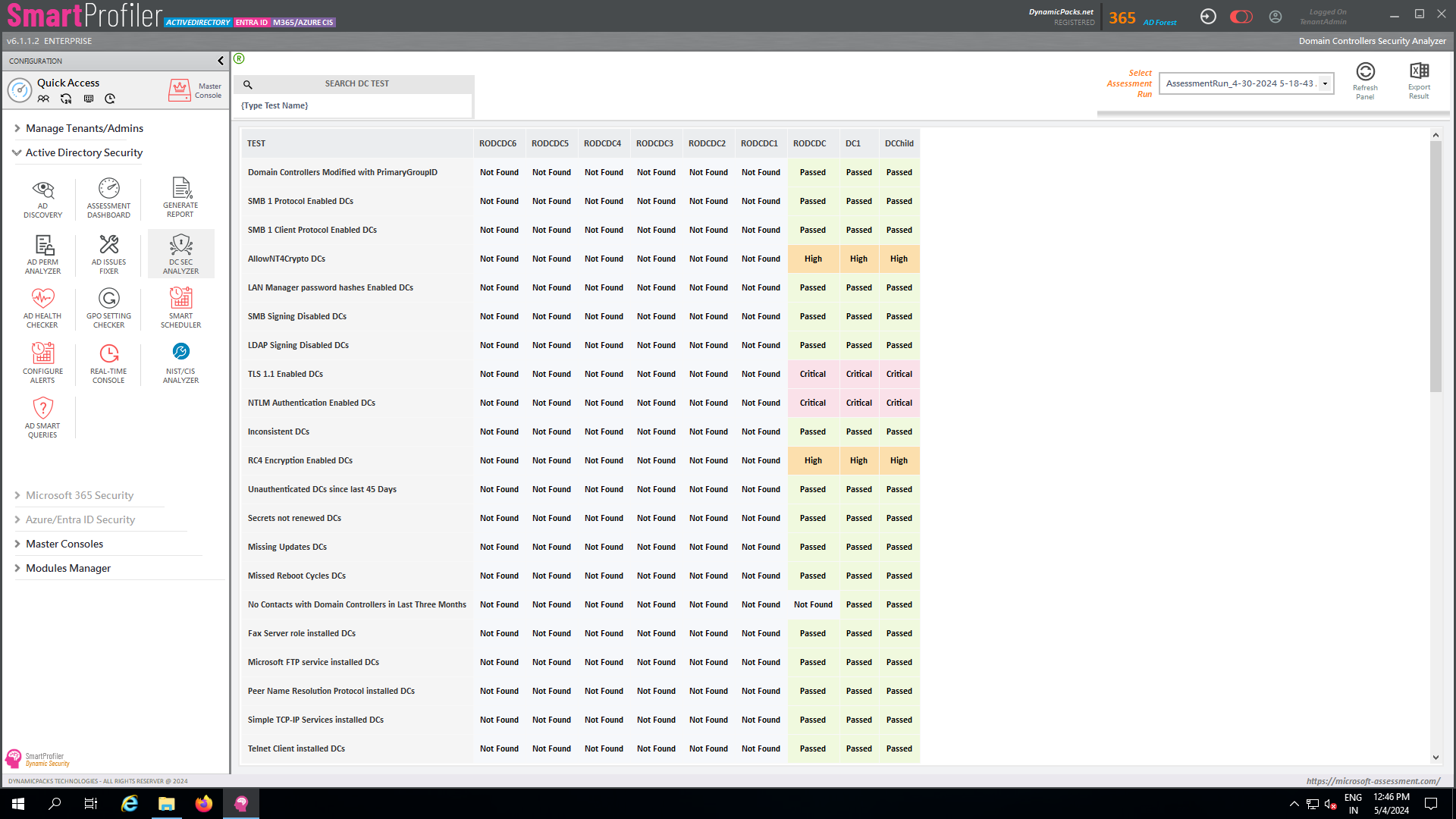
Checking GPO Settings in SmartProfiler
GPO Settings Checker is designed to check one or more GPO Settings in an AD Domain. The overall objective of GPO Settings Checker is to ensure a particular or a set of GPO settings are configured in the AD Domains and are applying to the objects. The resulting pane shows the OU to which the
Read More