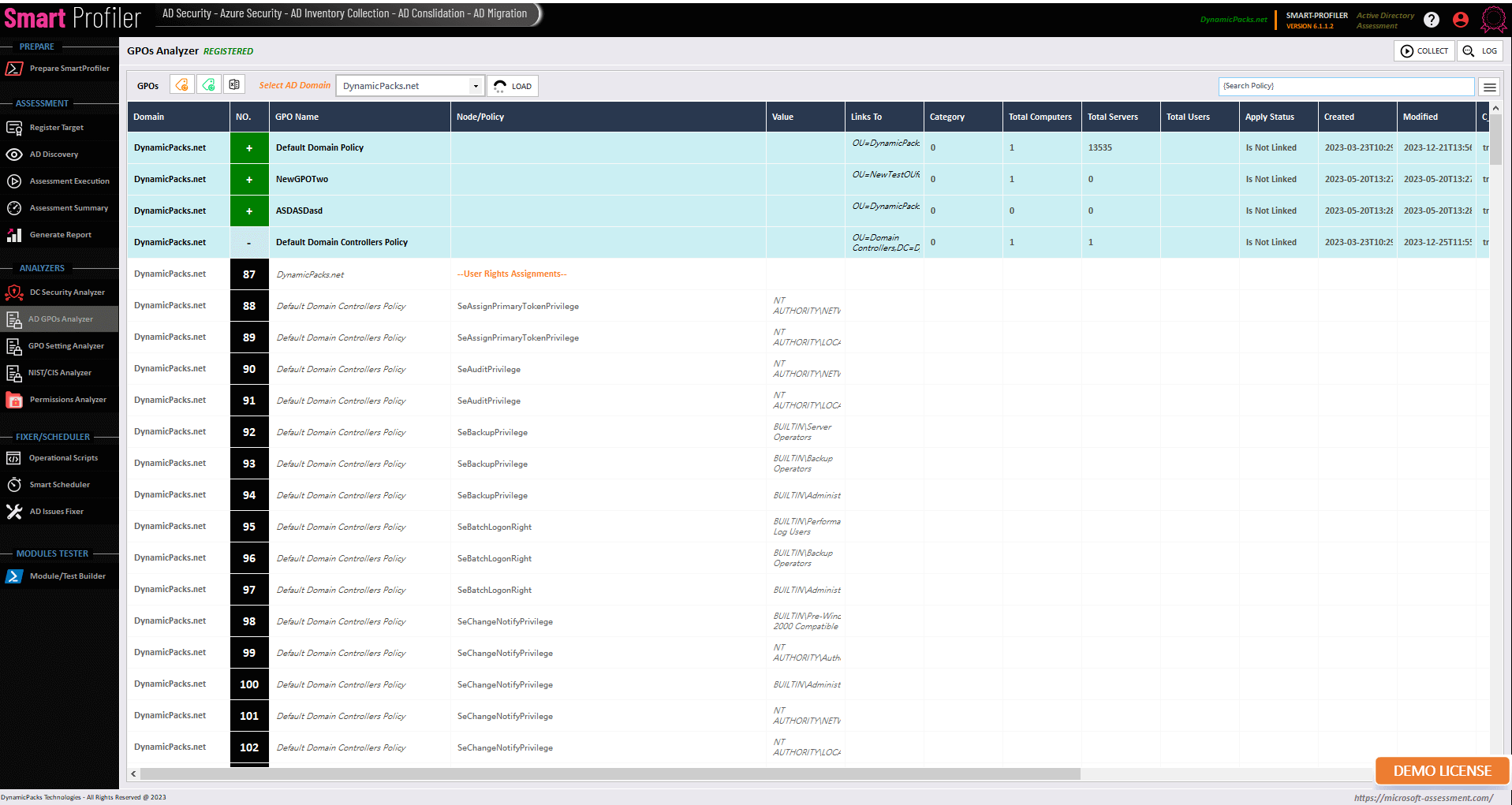
Using CIS/NIST Analyzer for Active Directory
The CIS/NIST Analyzer is designed to check CIS recommended GPO Settings in an Active Directory Domain. Currently, NIST/CIS Analyzer supports below templates. These templates are well-defined and written by CIS experts. However, there is no any automated way to check GPO settings defined in below templates. Why Check GPO Settings in Active Directory? Checking Group
Read More